
Cybercriminals go after Amazon Prime Day Shoppers
Highlights
- In the last 30 days, over 2300 new domains were registered about Amazon, a 10% increase from the previous Amazon Prime Day, where the majority now are either malicious or suspicious
- Almost 1 out of 2 (46%) of new domains registered containing the word “Amazon” are malicious
- Almost 1 out of 3 (32%) of new domains registered with the word “Amazon” are deemed suspicious
- CPR provides examples of malicious impersonations of Amazon Customer Service, as well as the log-in page for Amazon Japan
Amazon Prime Day, the e-retail giant’s two-day festival of promotions, special deals and discounts, is right around the corner, expected to launch on June 21st. Shoppers are eager and already seeking the web for the one time offers and deals that are traditionally breaking grounds and records in online shopping.
But shoppers aren’t the only one warming up in the sidelines, it seems that threat actors and hackers are already on the field, spreading malicious content and gearing up to leverage their own “special deals” on these online days.
Check Point Research has conducted an analysis of cyber threats related to Amazon’s Prime Day in the weeks leading up to the event. They have found alarming signs of malicious and suspected domains being erected, which are expected to lure eager online shoppers in various phishing campaigns to steal credentials, and gain unauthorized access to funds and financial transactions.
Alarm over Domain Registrations
In the previous Amazon Prime Day period, during October 2020, 28% of domains registered containing the word “Amazon”, were found to be malicious and another 10% suspicious. Furthermore, 20% of domains registered containing the words “Amazon” and “Prime” were found to be malicious.
In the past 30 days, over 2,303 new Amazon-related domains were registered, compared to 2137 in 2020. However, this year, almost half (46%) of those domains have been found to be malicious and another 32% suspicious. As for new Amazon Prime’s related domains, there were 32% malicious sites.
Phishing for Your Click
Phishing methods and techniques constantly get creative and innovative, with threat actor’s constantly seeking for ways to lure victims into click on what seems to look like a very legitimate website or email coming from an “expected” or familiar source. The basic element of a phishing attack is a message, sent by email, social media, or other electronic communication means.
A phisher may use public resources, especially social networks, to collect background information about the personal and work experience of their victim. These sources are used to gather information such as the potential victim’s name, job title, and email address, as well as interests and activities. The phisher can then use this information to create a reliable fake message.
Typically, the emails the victim receives appear to come from a known contact or organization. Attacks are carried out through malicious attachments or links to malicious websites. Attackers often set up fake websites, which appear to be owned by a trusted entity like the victim’s bank, workplace, or university. Via these websites, attackers attempt to collect private information like usernames and passwords, or payment information.
Example: Impersonation of the “Amazon Team”
Below is an example our researchers found of a phishing mail which seems like it was sent from “Customer Service”, but from looking on the email address it’s clearly understood that it’s phishing (admin@fuseiseikyu-hl[.]jp). The attacker was trying to lure the victim to click on a malicious link, which redirects the user to http://www[.]betoncire[.]es/updating/32080592480922000 – The link is inactive. Subject: Mail sent from Amazon:Wednesday, June 2, 2021 (GMT+10)
From: Customer Service (admin@fuseiseikyu-hl[.]jp)
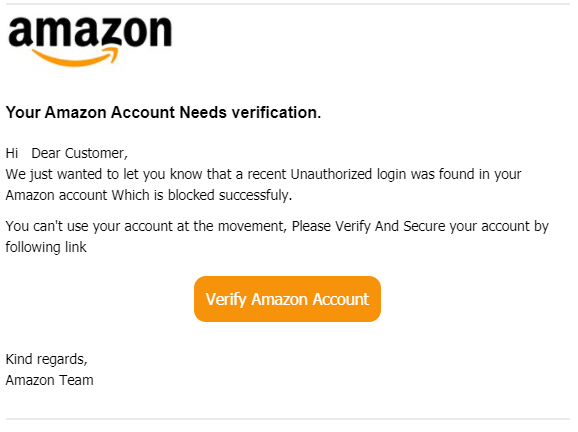
Phishing example, using Amazon logo coming from “Amazon Team”
Another Example
Another example is a fake, fraudulent malicious page that CPR found, disguised behind what looks like the real Amazon login website in Japan.
amazon[.]update-prime[.]pop2[.]live
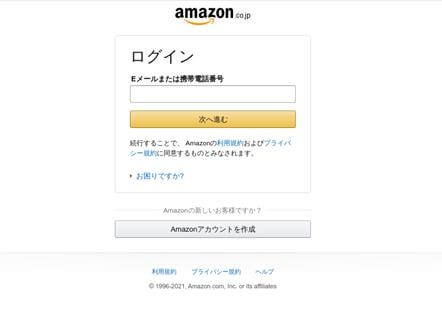
Fake website imitating Amazon Japan
How to Stay Safe on Amazon Prime Day
To help online shoppers stay safe this year, Check Point researchers have outlined practical security and safety tips:
- Watch for misspellings of Amazon.com. Beware of misspellings or sites using a different top-level domain other than Amazon.com. For example, a .co instead of .com. Deals on these copy-cat sites may look just as attractive as on the real site, but this is how hackers fool consumers into giving up their data.
- Look for the lock. Avoid buying something online using your payment details from a website that does not have secure sockets layer (SSL) encryption installed. To know if the site has SSL, look for the “S” in HTTPS, instead of HTTP. An icon of a locked padlock will appear, typically to the left of the URL in the address bar or the status bar down below. No lock is a major red flag.
- Share the bare minimum. No online shopping retailer needs your birthday or social security number to do business. The more hackers know, the more they can hijack your identity. Always maintain the discipline of sharing the bare minimum when it comes to your personal information.
- Always note the language in the email. Social engineering techniques are designed to take advantage of human nature. This includes the fact that people are more likely to make mistakes when they’re in a hurry and are inclined to follow the orders of people in positions of authority. Phishing attacks commonly use these techniques to convince their targets to ignore their potential suspicions about an email and click on a link or open an attachment.
- Before Prime Day, create a strong password for Amazon.com. Once a hacker is inside your account, it is game over. Make sure your password for Amazon.com is uncrack-able, well before June 21.
- Don’t go public. If you find yourself at an airport, a hotel or your local coffee shop, please refrain from using their public wi-fi to shop on Amazon Prime Day. Hackers can intercept what you are looking at on the web. This can include emails, payment details, browsing history or passwords.
- Beware of “too good to be true” bargains. This will be tough to do, as Prime Day is all about great offers. But, if it seems WAY too good to be true, it probably is. Go with your gut: an 80% discount on the new iPad is usually not a reliable or trustworthy purchase opportunity.
- Stick to credit cards. During Prime Day, it’s best to stick to your credit card. Because debit cards are linked to our bank accounts, we’re at much higher risk if someone is able to hack our information. If a card number gets stolen, credit cards offer more protection and less liability.









