
Check Point Research: Third quarter of 2022 reveals increase in cyberattacks and unexpected developments in global trends
Highlights:
-
- Global attacks increased by 28%in the third quarter of 2022 compared to same period in 2021. The average weekly attacks per organization worldwide reached over 1,130
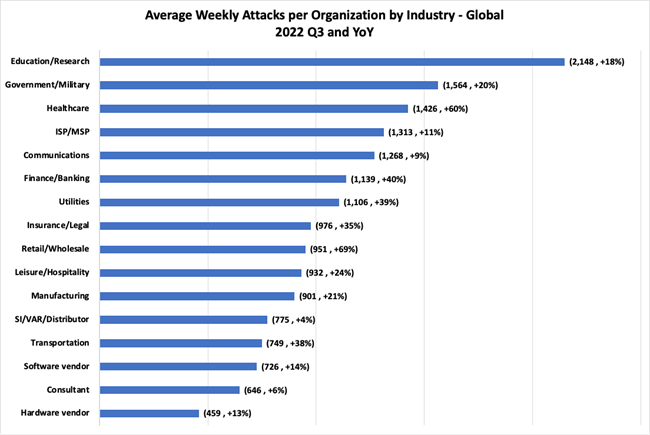
- The most attacked industry in the third quarter of the year was the Education/Research sector, with an average of 2,148 attacks per organization every week, an increase of 18% compared to third quarter of 2021
- The Healthcare sector was the most targeted industry for ransomware during the third quarter of 2022, with one in 42 organizations impacted by ransomware, a 5% increase YoY
- Check Point Research urges organizations to choose prevention over detection tactics and details recommendations
A fierce and stormy 2022
This year has been largely dominated by the Russia-Ukraine war, with major concerns about its impact on the global threat level. Just three days after the invasion of Ukraine, on February 27th, Check Point Research (CPR) noted a 196% increase in cyber-attacks on Ukraine’s government-military sector, and a 4% increase in cyber-attacks per organization in Russia.
It is not only war-related cyber activity that has seen a sharp rise over the last few months. It seems that hackers and attack groups have gained momentum and confidence, luring and attacking what seems to be endless targets around the globe. A few notable events are the LA Unified School District, the US’ second largest school district, which suffered “significant infrastructure disruption” in September. In Europe, Moody’s Investors Service cited that cyberattacks are accelerating across the continent, in a latest report. In Australia, Singtel-owned telecoms company Optus suffered one of the largest cyber breaches in the country’s history followed by data hacks on Medibank, Australia’s biggest health insurer. In October, Woolworths, one of Australia’s largest supermarket chains reported a data breach and, following on from the Optus attack, a second Australia-Based Singtel subsidiary, Dialog, an IT services consulting company, was also hacked.
Global Data
Check Point Research (CPR) has found that global attacks increased by 28% in the third quarter of 2022 compared to the same period in 2021. The average weekly number of attacks per organization worldwide reached over 1,130. While there has been an increase this year, it has plateaued when compared to the sharp rise seen in 2021. This could be an indication of how enterprises and governments are addressing the risks by increasing investment in their cybersecurity strategies and putting a greater focus on finding and detaining hackers.

Attacks per industry: Education still most attacked industry and Healthcare sees a 60% increase YoY
In a report published back in August 2022, CPR noted that the Education sector was experiencing more than double weekly attacks, compared to other industries. We have seen this trend continue, with the Education/Research sector facing an average of 2,148 attacks per organization every week in the third quarter this year, an increase of 18% compared to the third quarter last year.
Academic institutions have become a popular feeding ground for cybercriminals following the rapid digitization they undertook in response to the COVID-19 pandemic. Many were ill-prepared for the unexpected shift to online learning, which created ample opportunity for hackers to infiltrate networks through any means necessary. Schools and universities also have the unique challenge of dealing with children or young adults, many of which use their own devices, work from shared locations, and often connect to public WiFi without thinking of the security implications.
The second most attacked industry was Government/Military, with 1,564 average weekly attacks, marking a 20% increase from the same period last year. The Healthcare sector saw the largest change compared to last year, with 1,426 average attacks per week – a significant increase of 60% YoY.
Regional Data: Asia experienced the most attacks while ANZ saw largest increase amid latest breaches
As a region, Asia experienced the most cyberattacks in the third quarter of 2022, with an average of 1,778 weekly attacks per organization, which is an increase of 21% compared to the same period last year. The United Arab of Emirates (UAE) saw the largest individual growth with a 151% increase YoY.
Following reports of attacks on its telecom operators, health insurers and energy companies, the ANZ region has seen the highest increase in cyberattacks, a rise of 72% YoY.
| Region | Weekly Attacks per Organizations | YoY Change |
| Asia | 1,778 | +21% |
| Latin America | 1,572 | +32% |
| Africa | 1,549 | -6% |
| ANZ | 904 | +72% |
| Europe | 896 | +22% |
| North America | 849 | +47% |
Healthcare industry in ransomware peril, with one in 42 organizations impacted
In Check Point’s ‘Cyber Attack Trends: 2022 Mid-Year Report, our researches pointed to ransomware as the number one threat to organizations, stepping up to nation-state actor levels. Overall, the number of ransomware attacks has fallen worldwide by 8% compared with the third quarter of 2021. This could be due to a shift towards alternative attack methods such as botnets and hacktivism. However, ransomware continues to garner the most public attention and cause the greatest disruption.
The Healthcare sector was the most targeted industry in terms of ransomware in the third quarter of 2022, with one in 42 organizations impacted by ransomware, a 5% increase YoY. The second sector was ISP/MSP, where one in 43 organizations was impacted, a decrease of 25% YoY. This was followed by the Finance/Banking industry, where one out of every 49 organizations was affected by ransomware, indicating a 17% increase in the past year.
The Retail/Wholesale sector has seen the highest increase YoY of ransomware attacks, a 39% increase from the third quarter of 2021.
Don’t wait for the next attack – prevention is possible
There are several best practices and actions a company can take to minimize their exposure to the next attack or breach. Prevention is possible:
- Cyber Awareness Training: Phishing emails are one of the most popular ways to spread ransom malware. By tricking a user into clicking on a link or opening a malicious attachment, cybercriminals can gain access to the employee’s computer and begin the process of installing and executing the ransomware program on it. Frequent cybersecurity awareness training is crucial to protecting the organization against ransomware. This training should instruct employees to do the following:
- Not click on malicious links
- Never open unexpected or untrusted attachments
- Avoid revealing personal or sensitive data to phishers
- Verify software legitimacy before downloading it
- Never plug an unknown USB into their computer
- Use a VPN when connecting via untrusted or public Wi-Fi
- Up-to-Date Patches: Keeping computers and servers up-to-date and applying security patches, especially those labelled as critical, can help to limit an organization’s vulnerability to ransomware attacks.
- Keep your software updated. Ransomware attackers sometimes find an entry point within your apps and software, noting vulnerabilities and capitalizing on them. Fortunately, some developers are actively searching for new vulnerabilities and patching them out. If you want to make use of these patches, you need to have a patch management strategy in place—and you need to make sure all your team members are constantly up to date with the latest versions.
- For some businesses it may be beneficial to employ the help of tools that fortify endpoint resilience and secure remote users. Check Point Harmony for instance, uses real-time threat intelligence to actively guard against zero-day phishing campaigns, and URL filtering to block access to known malicious websites from any browser.
- Anti-ransomware technology allows you to detect signs of ransomware and uncover running mutations of known and unknown malware families by using behavioural analysis and generic rules.
- Deploy Email Security Solutions– Modern email filtering solutions can protect against malware and other malicious payloads in email messages. Solutions can detect emails that contain malicious links, attachments, spam content, and language that could suggest a phishing attack. Email security solutions automatically block and quarantine suspicious emails and use sandboxing technology to “detonate” emails to check if they contain malicious code.
- Choose Prevention over detection: Traditional cybersecurity vendors often claim that attacks will happen, and there is no way to avoid them, and therefore the only thing left to do is to invest in technologies that detect the attack once it has already breached the network and mitigate the damage as soon as possible. This is not true. Not only can attacks be blocked, but they can be prevented, including zero-day attacks and unknown malware. With the right technologies in place, most attacks, even the most advanced ones, can be prevented without disrupting the normal business flow. Learn more
The statistics and data used in this report present data detected by Check Point’s Threat Prevention technologies, stored and analyzed in ThreatCloud. ThreatCloud provides real-time threat intelligence derived from hundreds of millions of sensors worldwide, over networks, endpoints and mobiles. The intelligence is enriched with AI-based engines and exclusive research data from the Check Point Research (CPR) – The intelligence and research Arm of Check Point.



