
3CXDesktop App Trojanizes in A Supply Chain Attack: Check Point Customers Remain Protected
30/3/2023 03:35 EST
What is 3CXDesktop App?
3CXDesktopApp is a desktop client of 3CX voice over IP (VoIP) system. The application allows users to communicate within and outside the organization through their desktop or laptops.
The app can record calls and facilitate video conferencing and can be used on Windows, macOS, and Linux operating systems. It’s a tool that businesses use when they have a hybrid or remote workforce and their customers include government service providers like the NHS as well as large enterprises including Coca-Cola, Ikea and Honda.
What happened?
Over the past few days there has been accumulated evidence a Trojanized version of the original 3CXDesktopApp client is being downloaded to unsuspecting victims around the world. The Trojanized version includes a malicious DLL file, which replaced an original one, which is known to come with the benign version of the app. Then, when the application is loaded, the signed 3CXDesktopApp is executing the malicious DLL as part of its predefined execution procedure.
This turned the innocent popular VoIP app into a full blown malware that beacons to remote servers and capable of running second stage malware.
Supply chain attack indeed
This is a classic supply chain attack, although there is no evidence as of writing these lines to any intervention in the source code of 3CXDesktopApp. And yet, no one expected the application to be served with a malicious implant.
Supply chain attacks are designed to exploit trust relationships between an organization and external parties. These relationships could include partnerships, vendor relationships, or the use of third-party software. Cyber threat actors will compromise one organization and then move up the supply chain, taking advantage of these trusted relationships to gain access to other organizations’ environments.
This joins the weaponization of legitimate tools –
The basic layer of cyber protection is recognizing malicious tools and behaviors before they can strike. Security vendors invest substantial resources in the research and mapping of malware types and families, and their attribution to specific threat actors and the associated campaigns, while also identifying TTPs (Techniques, Tactics and Procedures) that inform the correct security cycles and security policy.
To combat sophisticated cybersecurity solutions, threat actors are developing and perfecting their attack techniques, which increasingly rely less on the use of custom malware and shift instead to utilizing non-signature tools. They use built-in operating system capabilities and tools, which are already installed on target systems, and exploit popular IT management tools that are less likely to raise suspicion when detected. Commercial off-the-shelf pentesting and Red Team tools are often used as well. Although this is not a new phenomenon, what was once rare and exclusive to sophisticated actors has now become a widespread technique adopted by threat actors of all types.
What We Know About the Attack
30th March 2023, 9.00 ET
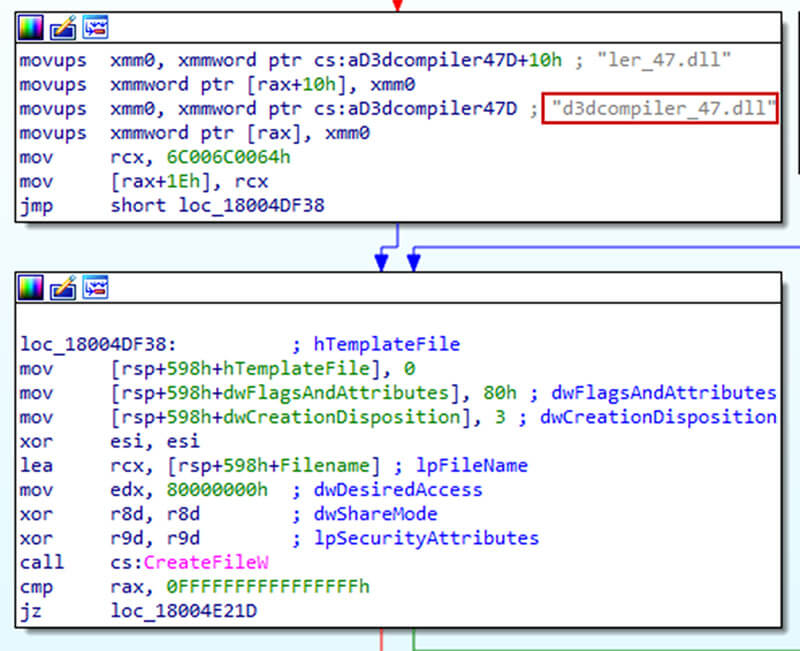
Infection chain in this attack abuses DLL side-loading via signed executable (MSI package). The DLL which is side-loaded (ffmpeg.dll) is malicious and is modified so that it in turn reads the encrypted data from another DLL (d3dcompiler_47.dll). Then an encoded URL is downloaded in the form of an icon from GitHub with Base64 block appended to the end of the file. The important point about communication with GitHub is that the delay of one week is set in the code before the request to GitHub actually occurs. After this step is finally accomplished, the final payload is downloaded from one of these URLs and executed.
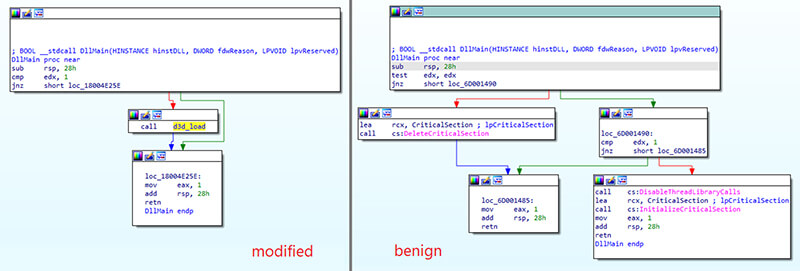
The key points of the infection chain are depicted in the following scheme:

ffmpeg.dll is modified at DllMain function to load the data from d3dcompiler_47.dll:
The process of loading the data from d3dcompiler_47.dll is performed with the help of XMM registers:
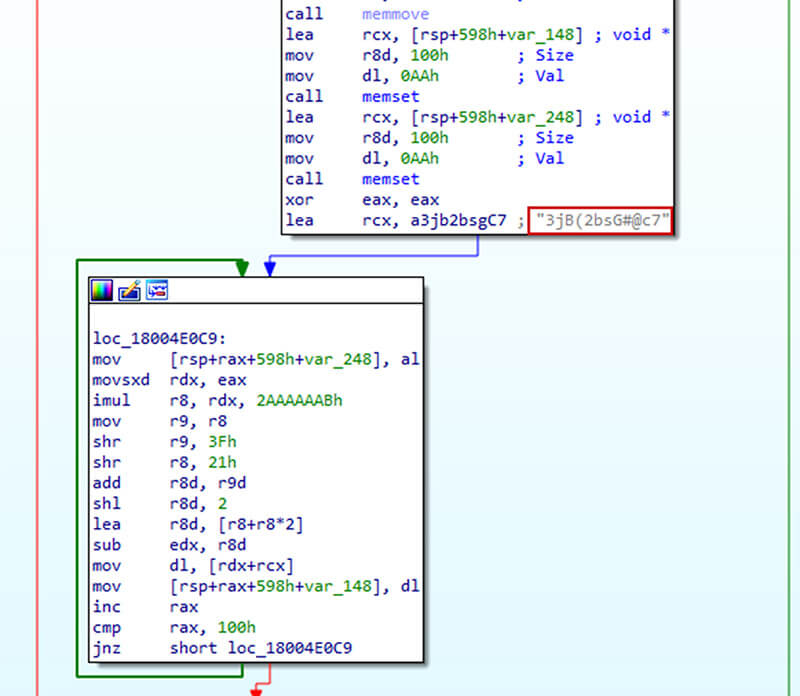
This data is then decrypted with the help of RC4 key embedded into ffmpeg.dll
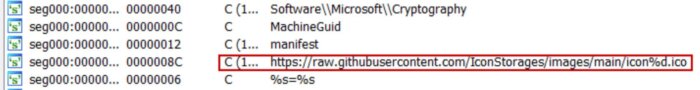
The decrypted data is then executed and this code accesses one of the icons stored
in GitHub:
All in all, there are 16 possible icons to be accessed inside:
Each of the icons has Base64 strings appended at the end of the file, for example:
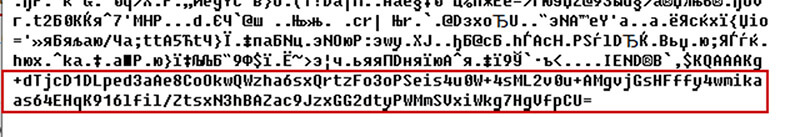
After decryption, these Base64-encoded strings transform each to one URL. The subsequent payload is downloaded from one of these URLs and executed to deal
further damage.
Protection- Check Point Customers remain protected
ThreatCloud provides the following protections:
| File | Protection Name |
| 82187ad3f0c6c225e2fba0c867280cc9 | Trojan.Win32.SmoothOperator.TC.1664FvwX |
| 9833a4779b69b38e3e51f04e395674c6 | Trojan.Win32.SmoothOperator.TC.e56edIyY |
| bb915073385dd16a846dfa318afa3c19 | Trojan.Win32.SmoothOperator.TC.7f81rhaT |
| 74bc2d0b6680faa1a5a76b27e5479cbc | Trojan.Win32.SmoothOperator.TC.ee03fhBl |
| ca8c0385ce2b8bdd19423c8b98a5924b | Trojan.OSX.SmoothOperator.TC.b5a4Aeic |
| 3703770e32820397c6e7e1e1221e6d0d | Trojan.OSX.SmoothOperator.TC.58e2DYEQ |
| Domain/URL | Protection Name |
| zacharryblogs.com | SmoothOperator.TC.dad8kOCb |
| github.com/IconStorages/images | SmoothOperator.TC.6058exvh |
| msstorageboxes.com | SmoothOperator.TC.a746WOcK |
| azureonlinestorage.com | SmoothOperator.TC.2e10lUBE |
| pbxcloudeservices.com | SmoothOperator.TC.7b01aAnN |
| msedgepackageinfo.com | SmoothOperator.TC.a382hItW |
| akamaitechcloudservices.com | SmoothOperator.TC.ccd7zlFc |
| qwepoi123098.com | SmoothOperator.TC.b1a3WZNp |
| officeaddons.com | SmoothOperator.TC.dbbcftbt |
| azuredeploystore.com | SmoothOperator.TC.927ewDuz |
| officestoragebox.com | SmoothOperator.TC.8bc4RYXH |
| pbxphonenetwork.com | SmoothOperator.TC.82a0vgKA |
| sourceslabs.com | SmoothOperator.TC.241cupgW |
| dunamistrd.com | SmoothOperator.TC.0c58eEmI |
| visualstudiofactory.com | SmoothOperator.TC.21a5jwyg |
| glcloudservice.com | SmoothOperator.TC.f2eagzaQ |
| sbmsa.wiki | SmoothOperator.TC.b47dNqPH |
| pbxsources.com | SmoothOperator.TC.02e7vSSr |
| azureonlinecloud.com | SmoothOperator.TC.08bauAZD |
| journalide.org | SmoothOperator.TC.84ebTBBw |
| msstorageazure.com | SmoothOperator.TC.fcbekAxf |
| akamaicontainer.com | SmoothOperator.TC.e9a6vHxH |
***We have removed soyoungjun[.]com as it was linked to the event based on an a possibly inaccurate information from a WHOIS data provider***
Supply chain attacks are one of the most complex attack forms. Security vendors cannot rely solely on reputation based or single layered solutions. They need to question activity as seen in the network, endpoints, servers and to connect the dots.
Check Point Horizon XDR/XPR is designed to provide comprehensive threat prevention across the enire security estate, with Check Point’s Infinity architecture.
The platform immediately blocks cyber threats originating in any part of the environment and prevents them from impacting the org and propagating across additional entities. XDR/XPR represents your last line of cyber defense; an additional layer of security across your consolidated security estate. Check Point Horizon XDR/XPR prevents complex attacks where seemingly benign events across different parts of the security estate, add up to a critical threat to your organization. The platform can automatically stop threats from propagating and spreading within your organization, and provides clear forensics as extra validation for the SecOps user.
All software vulnerabilities and attack signatures that are found by CPR or seen in the wild, such as the Trojanized version of the original 3CXDesktopApp
are immediately fed to ThreatCloud, the brain behind all of Check Point’s products, which propagates the appropriate protections throughout Check Point’s products, so that all Check Point customers are instantly protected with no patching needed. That is exactly what happened in this case.
As soon as the Trojanized version of the 3CXDesktopApp client was reported, all relevant protections were propagated through all of Check Point products.
ThreatCloud updates newly revealed threats and protections in real-time across Check Point’s entire portfolio









