
Cyber Criminals Using URL Tricks to Deceive Users
Overview:
In a newly observed scam, Check Point researchers found 200,000 phishing emails that abused URL information to obfuscate phishing links. The scam was first observed on January 21st, and remains ongoing, although the daily threat volume is decreasing.
Geographically, 75% of these emails have been distributed in the US, while 17% were distributed in the EMEA region, and 5% were distributed in Canada.
Why it matters:
The cyber criminals behind this campaign aim to compromise as many organizations and individuals as possible. The hackers do not appear to target specific industries, rendering a wide spectrum of enterprises vulnerable to this threat, unless they have an advanced email security solution.
Because the operational mechanisms involved in this campaign are quite sophisticated, despite security awareness training, most email users will not be able to identify the danger. As a result, organizations are at-risk of account-based credential theft.
How it works:
Cyber criminals deploy sophisticated URL manipulation techniques within standard phishing emails like fake invoices, tickets, payment receipts, renewal or account activation notices.

Example 1
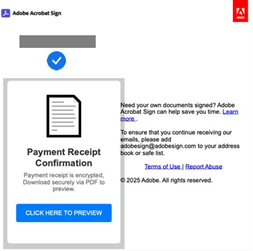
Example 2
Their primary deception method exploits the “userinfo” portion of web addresses – the segment between “http://” and the “@” symbol (e.g., https://username:[email protected]).
Since most websites disregard this field, attackers can insert misleading information before the “@” symbol to disguise malicious links. To further enhance their deception, attackers may employ multiple techniques in combination:
- URL-encoding with multiple characters.
- Routing through seemingly legitimate redirects.
- Placing the actual malicious URL immediately after the “@” symbol.
- Encoding victims’ email addresses to auto-populate fake login forms.
The final payload delivers a meticulously crafted Microsoft 365 phishing page, complete with CAPTCHA implementation – a social engineering touch that exploits users’ learned trust in security mechanisms.
This sophisticated interplay of technical deception and psychological manipulation demonstrates why traditional URL inspection training is becoming increasingly inadequate against modern phishing campaigns.
Mitigating this threat:
- Consider updating redirection rules. In the event that a site or application allows for redirection, ensure that your enterprise maintains strict rules around where redirects can lead to. Adopt current best practices.
- Regularly update and patch systems. Keep all software, including email clients and web browsers, up-to-date with the latest security patches. In so doing, you’ll prevent cyber criminals from exploiting vulnerabilities through which phishing attacks can be executed.
- Implement advanced email security. Utilize comprehensive and advanced email security solutions, like Harmony Email & Collaboration, to detect and block the most sophisticated of phishing attempts, including those using deceptive obfuscation techniques.Because obfuscation techniques evolve daily, static rules are insufficient for full protection. Machine learning (ML), however, can detect emerging patterns.
Looking ahead:
Security leaders may wish to consider this campaign a warning sign regarding future attack evolution. As phishing attack techniques become more sophisticated, organizations need to shift from user-dependent security controls to more automated, AI and ML-driven threat prevention systems.
Organizations may need to rethink email authentication frameworks, potentially moving beyond SPF, DKIM and DMARC protocols alone.



