
Implement a Continuous Threat Exposure Management (CTEM) Program with Check Point IGS Consulting Services
In today’s constantly evolving threat landscape, it is more important than ever to have a strong security posture in place. Threat actors are becoming more sophisticated and are increasing their rate of attacks – according to Check Point Research, cyber attacks increased 28% in Q1’2024. Many organizations rely on their CISOs to understand the risks and threats which they could be exposed to – but this is becoming an increasingly challenging task as they are also tasked with enabling the business. This means that having an easy way to view and analyze cyber security metrics is essential for CISOs to evaluate their organization’s cyber defenses and cyber security posture.

Challenges of a CISO
But accessing cyber security metrics can be a challenge for CISOs. The metrics are not always readily available in a single dashboard and may not be real-time.
Thus, a CISO needs a proactive program that allows them to predict, project, evaluate and measure business damage caused by possible future attacks as a result of existing unknown vulnerabilities. With new NIST CSFv2, NIS2, and DORA regulations, it’s also important that the CISO has validation of their current cyber defense technologies and incident response process of post-attack remediation.
Continuous Threat Exposure Management (CTEM) is an evolving framework and strategic program, part of a general cyber security strategy developed by CISOs, that focuses on the continuous identification, assessment, and mitigation of cyber threats and vulnerabilities within an organization’s digital environment.
According to the Garner report “By 2026, organizations prioritizing their security investments based on a CTEM program will realize a two-thirds reduction in breaches.”
Implementing CTEM effectively requires a structured approach that can adapt to the dynamic nature of cyber threats and the IT landscape.
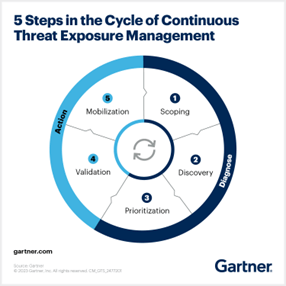
Five Phases of CTEM Program
There are five phases that outline how CTEM can be delivered, from initial scoping to taking action:
- Scoping and Planning: This initial phase involves identifying critical assets, systems, and data that need protection, understanding the organization’s risk tolerance, and setting priorities for threat management.
- Vulnerability Management and Threat Intelligence Gathering: In this phase, organizations collect and analyze information about emerging threats, vulnerabilities, and exploits that could potentially impact their digital environment.
- Risk Analysis and Prioritization: Once vulnerabilities and threats have been identified, the next step is to assess the risk they pose to the organization. This involves evaluating the likelihood of a threat being realized and the potential impact on the organization’s operations, reputation, and finances.
- Validation: With a clear understanding of the priority threats and vulnerabilities, organizations can now focus on remediating or mitigating these risks. Remediation may involve patching software, implementing security controls, or making configuration changes.
- Continuous Improvement and Adaptation: The final phase focuses on learning from the CTEM process and making continuous improvements. This involves reviewing the effectiveness of the remediation efforts, updating the threat intelligence and risk analysis processes based on new information, and refining the overall CTEM strategy.
CTEM with IGS
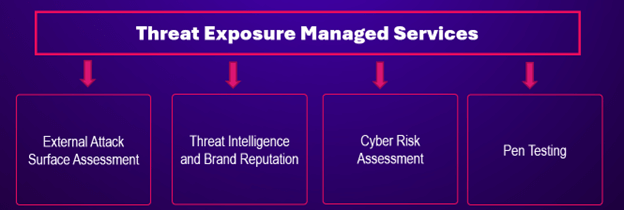
Check Point Infinity Global Services offers multiple services to assist CISOs in implementing and managing an effective and robust CTEM program within their organization:
- External Attack Surface Assessment Managed Service: Systematically identifies and evaluates vulnerabilities and risks present in an organization’s publicly accessible digital assets.
- Cyber Risk Assessment: Perform thorough risk analysis and gap assessment based on industry standard frameworks such as NIST CFS / 800-52, CIS, ISO and NIS2.
- Threat Intelligence: Offers a visibility to the latest threats and vulnerabilities, providing deep insights (e.g. Darweb search) for proactive measures.
- Penetration Testing: Red Team will perform targeted pen testing using Red Team experts and advanced tools.
Implementing CTEM with Check Point IGS Consulting Services will enable CISOs and organizations to proactively manage their cyber threat exposure, reducing the likelihood and impact of any possible security incidents in the future.
Contact a Check Point Security Expert today for more information on how to get started on your CTEM program.
Infinity Global Services:
Check Point offers comprehensive managed security services through its Infinity Global Services. These services include threat research, MDR, risk assessment, proactive monitoring, professional services, and top-notch training. Our suite of cyber security services provides end-to-end protection – from initial assessment and design to ongoing training and optimization to rapid response – ensuring the highest level of security. Backed by world-class experts and real-time threat intelligence, our extensive range of services helps safeguard organizations of all sizes.


