
Who’s Zooming Who? Guidelines on How to Use Zoom Safely
By Omri Herscovici, Vulnerability Research Team Lead
In recent weeks, the COVID-19 crisis has meant that millions of people are staying at home instead of going to work or meeting up with people. Estimates vary but up to 50% of employees globally may now be working remotely. Online communications platforms have become essential for personal and business interactions with the rest of the world, and with a near 20% global market share, Zoom is one of the most popular platforms.
As with any popular technology, along with the obvious benefits there are also risks. We have heard about the misuse of the app, with external parties being able to eavesdrop on private meetings and conversations, as reported by Check Point Research earlier this year, potentially leading to personal data breaches or business espionage.
So how can we enjoy the benefits of Zoom without making ourselves vulnerable on the key threats? Here are some tips to consider.
1. Keep up to date
In order to maintain effective security, the Zoom software must be updated frequently. The updates that tech companies offer for their products not only add new options and features, but also address “bugs” and security breaches found – such as the ability to discover and eavesdrop on meetings that we mentioned above. It is important to understand that, contrary to popular belief, attackers’ window of opportunity does not close after the security breach has been repaired, but only after users run a software update and receive the company’s product patches to address the threats. This means users who have not updated the software remain vulnerable.
2. Using a login password
Our investigation into Zoom conference security showed how an attacker could guess random numbers allocated to Zoom conference URLs and penetrate them without alerting the hosts. The breach happened with conversations where no passwords were set. Zoom fixed the security breach and adopted our recommendations, with all scheduled meetings automatically protected by a password.
The requirement to present a password before entering the conference, in addition to displaying the call number, provides sufficient security. But in order to be fully protected, attention must be paid to how we invite the various participants into the call.
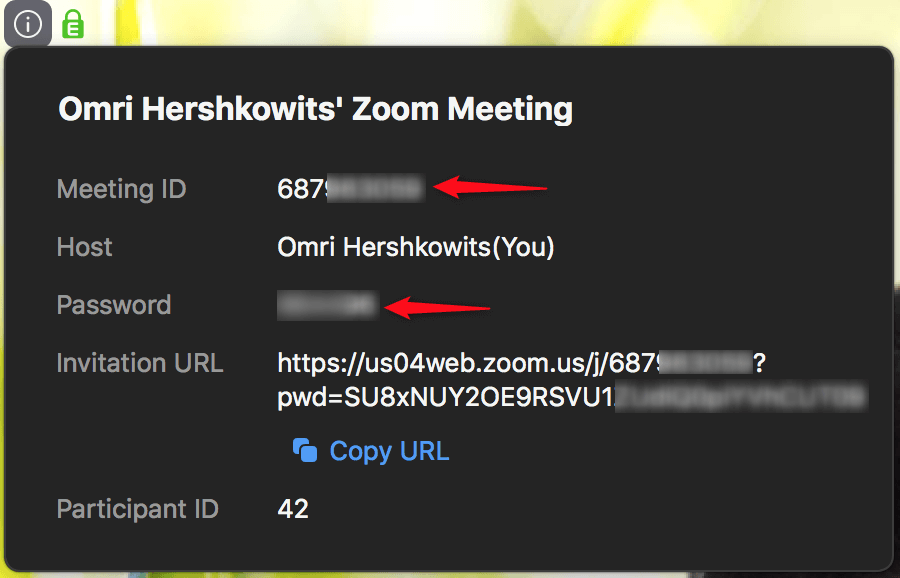
Alongside the secure method, which includes sending the caller ID and password for the call, there is a less secure option. This option allows you to click on the “Invite” button at the bottom of the screen, then “Copy URL” or “Copy Invite” to send to anyone you wish to join the call. Since this link does not require a password entry, pay close attention to who and how it is shared since anyone with the link can enter the call without having to show a call ID number or password. Also, we recommend connecting to Zoom via SSO (single sign on) if your company has the option for you to do so.
Another way to control who enters the call is the “Waiting Room” option, in which a call manager creates a “Waiting Room” through which the participants can connect, but only if the call manager confirms the participants one by one or as a group. You can do this in the “Advanced Options” drop-down menu when you want to schedule a call.
3. During the call – manage your participants
Even if we have decided to use the less secure link-sharing option, we may prevent instances of participants displaying inappropriate content by restricting the use of camera by participants. The conversation manager can decide who can use their camera and microphone by clicking “Manage Participants”.
4. Assume what happens in Zoom does not stay in Zoom
Zoom allows you to record video calls and export them as video files as soon as the call ends. This is a very useful tool when you want to update those who were not present at the meeting. The security problem that comes with using this tool is almost self-explanatory: since conversation participants can export the recorded file, the file can actually find its way into malicious hands.
To reduce the possible dangers from using the recording tool, the call manager can decide which of the participants may record the call through the participant management window and click “Allow Record”.
Do also take note that the participant can always record the conversation using external software for recording the screen. Therefore, always assume that you may be recorded and act accordingly.
After the call, if you have recorded it, ensure you don’t upload it to a shared platform like an information sharing cloud that is open to other parties.
The Zoom platform offers a myriad of benefits to those who have to work from home during this period of time. As with any tool, it is important to be aware of the possible risks, and use the functions available to you on the platform to communicate safely.









