
Connect the Security Dots by CloudGuard Effective Risk Management
Countless of services we use in our daily life are backed by Cloud computing, thanks to its agility and global presence from many cloud service providers nowadays. Although we tend not to realize about their cloud dependency until such services stop functioning or involve in an “unfortunate” event where a cybersecurity breach result in data leak.
I said “unfortunate” as one of the first misconception is any services deployed on Cloud should have been already “secured”, when it is a continuous education that Cloud Security is a Shared Responsibility between cloud customer and cloud service provider. Another challenge is an organization may have to let Cloud Security takes a back seat while prioritizing to migrate/deployment of service to cloud.
Fire Fighting
Having a comprehensive monitoring, detection & response no doubt is an important part of overall Cloud Security. Although solely focus on security alerts may mislead to react to whatever cause the latest security incident and less on what is a suitable strategic approach. Let’s say a high-profile vulnerability in the news may trigger an organization to urgently scan all cloud assets for the related Common Vulnerability and Exposure (CVE). Then if a security incident result in a sensitive data leak occurs, the focus likely shifts to do data classification and encryption at rest.
Cloud and Security together leave a vast knowledge gap
It is rare to have every team member with a similar expertise in both cybersecurity and cloud, let alone knowledge in multiple cloud service providers. This leaves room of interpretation of each security personal what to response first: a vulnerability scan alert, a cloud security posture finding, a sensitive data found in storage expose to public internet? What if they are all critical level severity and come in a same time?
“I’d rather NOT KNOW, what I DON’T WANT TO KNOW.”
Despite 76% of organizations are extremely or very concern about Cloud Security according to 2023 Cloud Security report, do not be surprised a push back for taking on Cloud Security responsibility. First scenario is either security and/or cloud operation teams are in an alert fatigue from their existing security monitoring. Another push back could cause by endless fixing because of security auditing cycle occupying team’s personal and priority.
Connect the Security Dots by Effective Risk
Instead of driven by number of alerts from multiple sources, consider a risk base approach (likelihood x impact = risk). This connects the “security dots” into a holistic easy-to-understand indicator regardless of individual’s level of cloud knowledge.
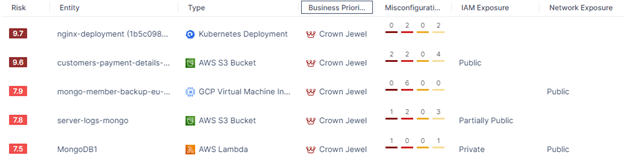
Leverage your team familiarity of each cloud
A team member with extensive experience would know which of sometimes hundreds of cloud accounts and/or subscriptions are crucial, which specific names of virtual machine, storage or database fleets are super important and impactful to business operation, or any workload with sandbox tagged can tolerate certain security settings for experimental. However, such insightfulness is not necessarily common in your team especially among newly joined individuals. Why not embed these non-technical indicators directly into the risk calculation by defining business priority rules, then the effective risk score would adjust accordingly.
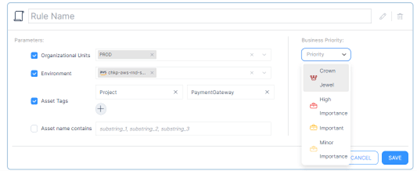
Conclusion
With CloudGuard Effective Risk Management, the security risk score is automatically calculated for individual cloud asset as well as for each cloud account/subscription. A further optimization to make it even more relevant to your organization is simple.
- Structure your cloud accounts and subscriptions into organizational units within CloudGuard portal. This could base on the business unit, production and non-production, or any other combination meaningful to your cloud estate.
- Label a business priority for each cloud account/subscription or OU defined in CloudGuard in the earlier step. The priority label is based on its relevant to business, service, revenue or others non-technical significant.
- Add more fine grain business priority rules based on cloud asset name, or key/value tag where needed.
Simple as that! Start a regular review of CloudGuard ERM Dashboard, where you will find a list of cloud assets with the highest security risk score. Then structurally prepare an action plan to focus on addressing each security findings of these high-risk assets.
CloudGuard Effective Risk Management is available on CloudGuard CNAPP.



