
DeepDLL– A New Approach to Detect Malicious DLLs
Cyber attackers are increasingly using DLL (Dynamic Link Library) files to spread malware. Modern attack chains have complex multi-stage flows and DLL is a common step in all major malware families. Methods like DLL hijacking, sideloading, and reflective DLL injection allow the malware to hide as part of trusted software. Attackers, often use DLLs that look innocent but trigger an attack chain. To combat these evasive threats, Check Point developed a new AI engine for DLL files – detecting malicious patterns in content and context.
What are DLLs?
DLLs are a type of file in Windows Operating Systems that contain code and data used by multiple programs simultaneously. These files help programs use resources efficiently and reduce the overall size of the software. Their utility makes them a tempting target for attackers. Abusing DLL files has become a popular way for hackers to stay hidden and gain control over targeted systems.
How do attackers exploit DLLs?
Attackers manipulate DLLs to inject malicious code into legitimate processes. Here’s a breakdown of common techniques used:
- DLL Hijacking: This occurs when an attacker places a malicious DLL with the same name as a legitimate one in a location that the system searches before the legitimate DLL’s location. When the system runs, it loads the malicious DLL, thinking it’s the legitimate one.
- DLL Side-Loading: Similar to hijacking, this technique involves tricking an application into loading a malicious DLL by placing it in its path, often exploiting the trust that the application has in its own directory.
- DLL Injection: This is a direct approach where malicious code is injected into a running process via a DLL, allowing the attacker to run their code within the context of another application.
Introducing DeepDLL: an AI engine that prevents malicious DLLs by analyzing their content and context
DeepDLLis a new, first-of-its-kind AI model designed to prevent zero-day DLL threats. The engine, trained on millions of malicious samples, leverages ThreatCloud AI big data and detects unique set of malicious features of DLLs. The new model is now integrated into ThreatCloud AI and integrated into all Check Point’s products.
DeepDLL’s extracted features indicate potential malicious activity, as identified by our researchers. For example, file metadata and compiled structure (communication, encryption, code structure etc.). Moreover, The engine learns the attack chain of the DLL and whether the DLL arrives via email, ZIP file, or is dropped by an executable. Finally, all the features are sent to our new AI model, trained on millions of malicious samples, that analyze the data and detect patterns of malicious features.
By leveraging information from ThreatCloud AI, we have achieved a 99.7% accuracy rate with minimal false positives in Dalale’s results.
Case in Point – a DLL Contains Raspberry Payload
In this use case, a DLL file was uniquely detected by DeepDLLat one of Check Point’s customers located in the Netherlands. The malicious DLL, included in an MSI installer downloaded to a customer’s machine, was blocked upon execution.
The MSI files contained several elements, and a related sample was found among them. However, it did not have a DLL extension, but was identified as a DLL by the Threat Emulation classifier.
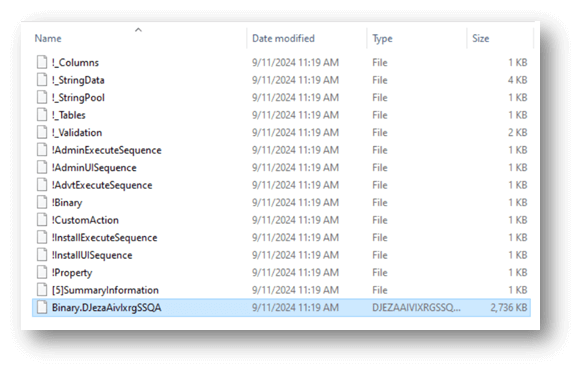
Figure 1 – MSI installer content
We can see the sample is being executed by its parent MSI
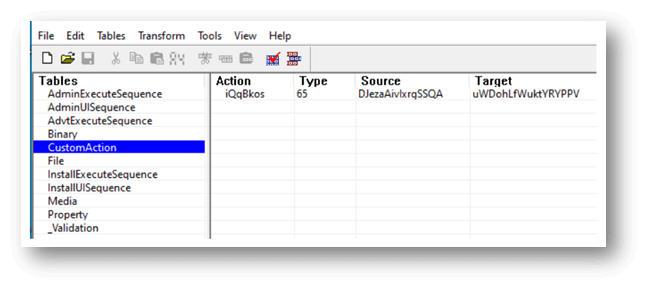
Figure 2 – Actions being called by parent MSI (Microsoft’s Orca Tool)
The DLL is highly suspicious since even though it is a DLL, it has no exported functions at all, and all the strings it contains are highly obfuscated:
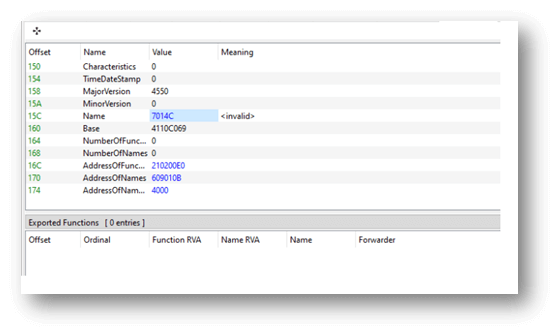
Figure 3 – List of exported functions
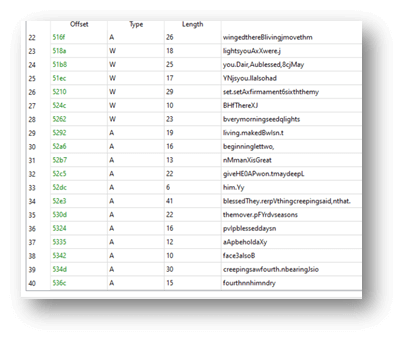
Figure 4 – Obfuscated string found in the DLL
The payload code verifies it doesn’t run under virtual emulation and only then continues with unpacking the payload.
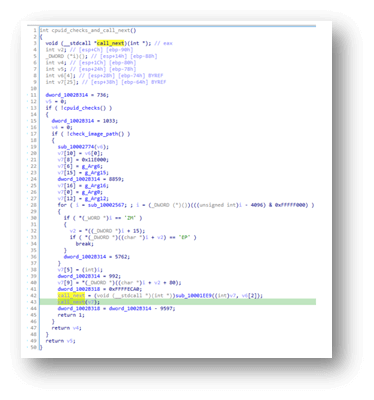
Figure 5 – Call for unpacking
Then it allocates a new memory region and redirects its current execution to this address. We were able to dump this section and found result of the dump of the file matched a rule of the notorious Raspberry robin.
DeepDLLwas able to prevent this sample before it reaches customer’s environment by finding this unique set of malicious features. Check Point customers using Quantum and Harmony products with Threat Emulation activated are protected against the campaigns detailed in this report.
To learn about Check Point threat prevention, schedule a demo or a free security checkup to assess your security posture.



