
With the Right Tools, You Can Prevent This Healthcare Scam from Hurting Employees
In 2024, ninety-two percent of healthcare organizations contended with at least one cyber attack. As a result, over 276 million patient records were compromised, translating to the compromise of roughly 758,000 records every single day.
Victims of medical identity theft will spend an average of 210 hours and $2,500 (out-of-pocket) to reclaim their identities and resolve breach fallout.
Overview:
The Check Point Research team has recently uncovered a sophisticated phishing campaign that impersonates medical service providers, such as Zocdoc, and that involves allusions to fabricated medical clinics.
The campaign can be traced back to March 20th, and has been blocked successfully by Check Point’s Harmony Email & Collaboration product.
Harmony Email & Collaboration has stopped over 7,000 emails that were sent to private email services and that targeted nearly 300 different organizations.
Why it Matters:
The cyber criminals behind these healthcare-focused attacks aim to steal sensitive employee/consumer data. Here’s why:
- Healthcare data can independently command premium prices on the dark web, making this pursuit extremely lucrative for cyber criminals.
- Personal health data can be processed and packaged with additional illicitly obtained private data. In turn, cyber criminals can create “identity kits” that can be sold and used to support a variety of criminal exploits.
- Cyber criminals can leverage sensitive healthcare data in order to conduct psychological warfare. They can threaten to expose peoples’ personal information to extort them financially, to blackmail them, and more.
- Exposed data may enable cyber criminals or data buyers to obtain medical services or prescriptions that are in the victim’s name. Nefarious persons may attempt to resell prescription medications for profit, for example.
- In the event that a clinic’s medical records are altered by cyber criminals, victims may receive incorrect treatments and suffer through dangerous medical errors.
Technical Details:
In some versions of these phishing emails, cyber criminals deploy images of real, practicing doctors who are listed with fake names.
Emails tell recipients to contact the listed health services provider and to use a specific phone number in so doing.
When people call the number, cyber criminals attempt to extract information, luring people into revealing sensitive personal details.
Campaign Examples:
One particularly notable campaign example involved the impersonation of a Zocdoc. Attackers used an image of a real doctor paired with a fake name.
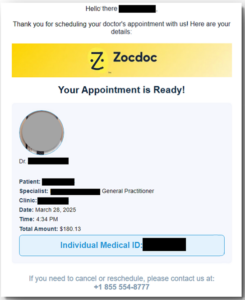
Example 1: Impersonation of Zocdoc
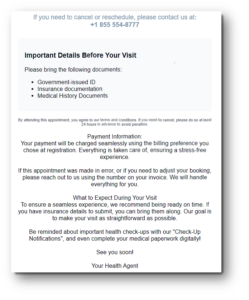
Example 2: Fake pre-appointment message
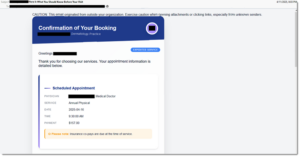
Example 3: Confirmation of booking image
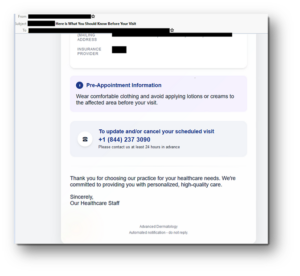
Example 4: Additional pre-appointment information
More Information:
More than 95% of the campaign’s targets are based in the United States. Check Point’s cyber researchers were unable to identify a specific group or entity behind the campaign.
Actionable Steps for Organizations:
- Organizations are advised to implement advanced email filtering solutions, like Check Point’s SmartPhish, which automatically blocks phishing attempts and adds additional layers of cyber protection.
- Employee education also plays a role in stopping these types of attacks. Inform employees about healthcare organization impersonation attempts. In addition, conduct phishing simulations to test employees’ knowledge and level of awareness.
- Establish phishing monitoring and response protocols. Have a clear process for reporting suspicious emails. Ensure that IT support or a cyber security team is ready and available to handle potential threats.
- Ensure that employees’ mobile devices are protected with cyber security software that can block phishing attempts.
For more information about advanced email security solutions, like Check Point’s Harmony Email & Collaboration, please reach out to your local representative or get a demo here.



