
Amazon Prime Day: This Year Already Started for Cybercriminals. Check Point Research calls online shoppers to be wary
Highlights:
-
Amazon prime related phishing campaigns grew 16- folds higher in June, compared to May. The overall increase in all Amazon related phishing was 8%
-
During this period, there were almost 1,500 new domains related to the term “Amazon” of which 92% were found to be either malicious or suspicious
-
One out of every 68 “Amazon” related new domains, was also related to “Amazon Prime”. About 93% of those domains were found to be risky
-
Check Point Research provides phishing related examples, calls online shoppers to remain alerted, and provides safer online shopping tips
A shopping extravaganza can turn sour
Amazon Prime Day is a highly anticipated shopping extravaganza that brings joy and excitement to countless shoppers worldwide. With its incredible deals and exclusive offers, it has become a festive occasion for those seeking great bargains.
The Amazon Prime Day which this year falls on 11th and 12th of July, grew in volume to new peaks in 2022, according to Amazon , as Prime members in the U.S. purchased more than 60,000 items per minute during the 2022 event, with global members purchasing more than 300 million items worldwide during Prime Day 2022.
However, amidst the excitement, there is an underlying risk that cannot be ignored. Cybercriminals leverage this occasion to carry out phishing attacks, preying on unsuspecting shoppers. These attackers employ deceptive tactics, such as sending fake emails or creating fraudulent websites, aiming to steal personal information or financial credentials. While Prime Day offers incredible savings, it is crucial for shoppers to remain vigilant, exercise caution while clicking on links or providing sensitive information, and ensure they are navigating legitimate platforms.
Alarming findings on domain registration and phishing attacks
This year, Check Point Research (CPR) found 16 times more malicious Amazon prime related phishing attacks during the month of June compared to May, and the overall increase in all Amazon related phishing was 8%. During this period, there were almost 1,500 new domains related to the term “Amazon” of which 92% were found to be risky – either malicious or suspicious.
1 out of every 68 “Amazon” related new domains, was also related to “Amazon Prime”. About 93% of those domains were found to be risky.
How Phishing Works
The basic element of a phishing attack is a message, sent by email, social media, or other electronic communication means.
A phisher may use public resources, especially social networks, to collect background information about the personal and work experience of their victim. These sources are used to gather information such as the potential victim’s name, job title, and email address, as well as interests and activities. The phisher can then use this information to create a reliable fake message.
Typically, the emails the victim receives appear to come from a known contact or organization. Attacks are carried out through malicious attachments or links to malicious websites. Attackers often set up fake websites, which appear to be owned by a trusted entity like the victim’s bank, workplace, or university. Via these websites, attackers attempt to collect private information like usernames and passwords, or payment information.
Some phishing emails can be identified due to poor copywriting and improper use of fonts, logos, and layouts. However, many cybercriminals are becoming more sophisticated at creating authentic-looking messages, and are using professional marketing techniques to test and improve the effectiveness of their emails.
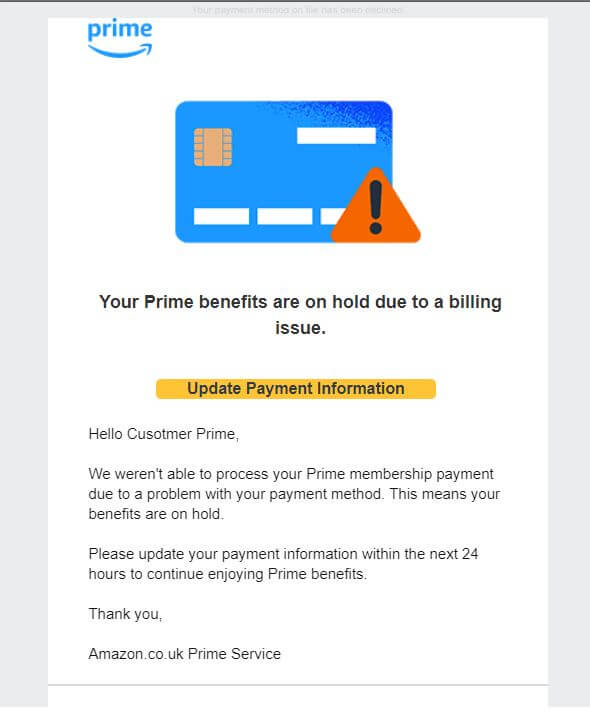
Prime Credit Card Theft Example:
Below is an example of a phishing mail that seems like it was sent from “Amazon[.]co[.]uk”. The attacker was trying to lure the victim to click on a malicious link, which redirects the user to http://www[.]betoncire[.]es/updating/32080592480922000 – The link is currently inactive.
Subject: Your Prime Membership: Payment declined: Payment method has been declined, please update your payment method so that your order is not canceled and your account is not suspended
From: Amazon.co.uk (prime-update[.]74715579-59050019[.]24219850@amazon[.]co[.]uk)
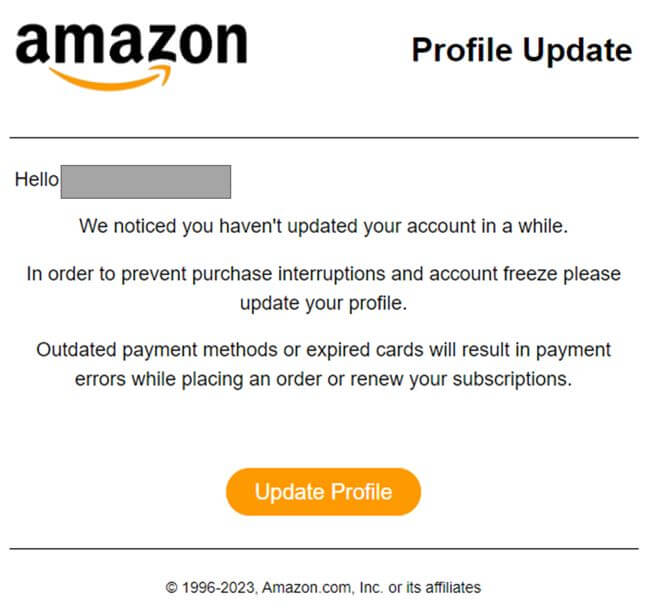
Credentials Theft Example:
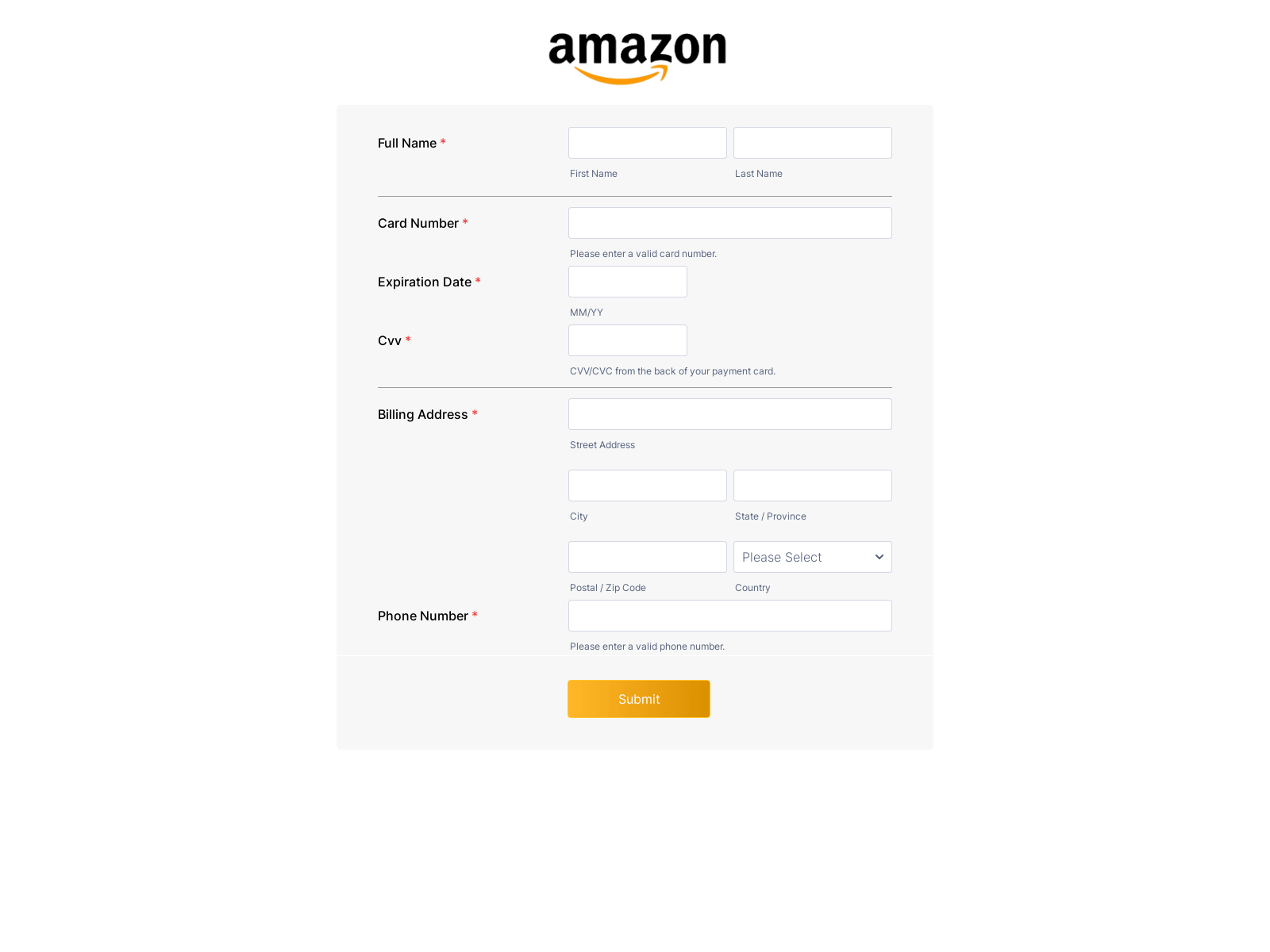
CPR noticed a malicious phishing email that was allegedly sent by Amazon and which was trying to steal users’ credit information. The email which was sent from the spoofed address Amazon (amazon@blackoutthelimit[.]com) contained socially engineered subject which could pressure the victim into clicking on the malicious link http://kolives[.]com/profile/
The website redirected the user to a fraudulent Amazon payment page that looks like the real site with minor changes (For example “Cvv” instead of “CVV”).In the malicious link, the user needed to enter credit information. The link is currently inactive.
Subject: Account locked
From: Amazon (amazon@blackoutthelimit[.]com)
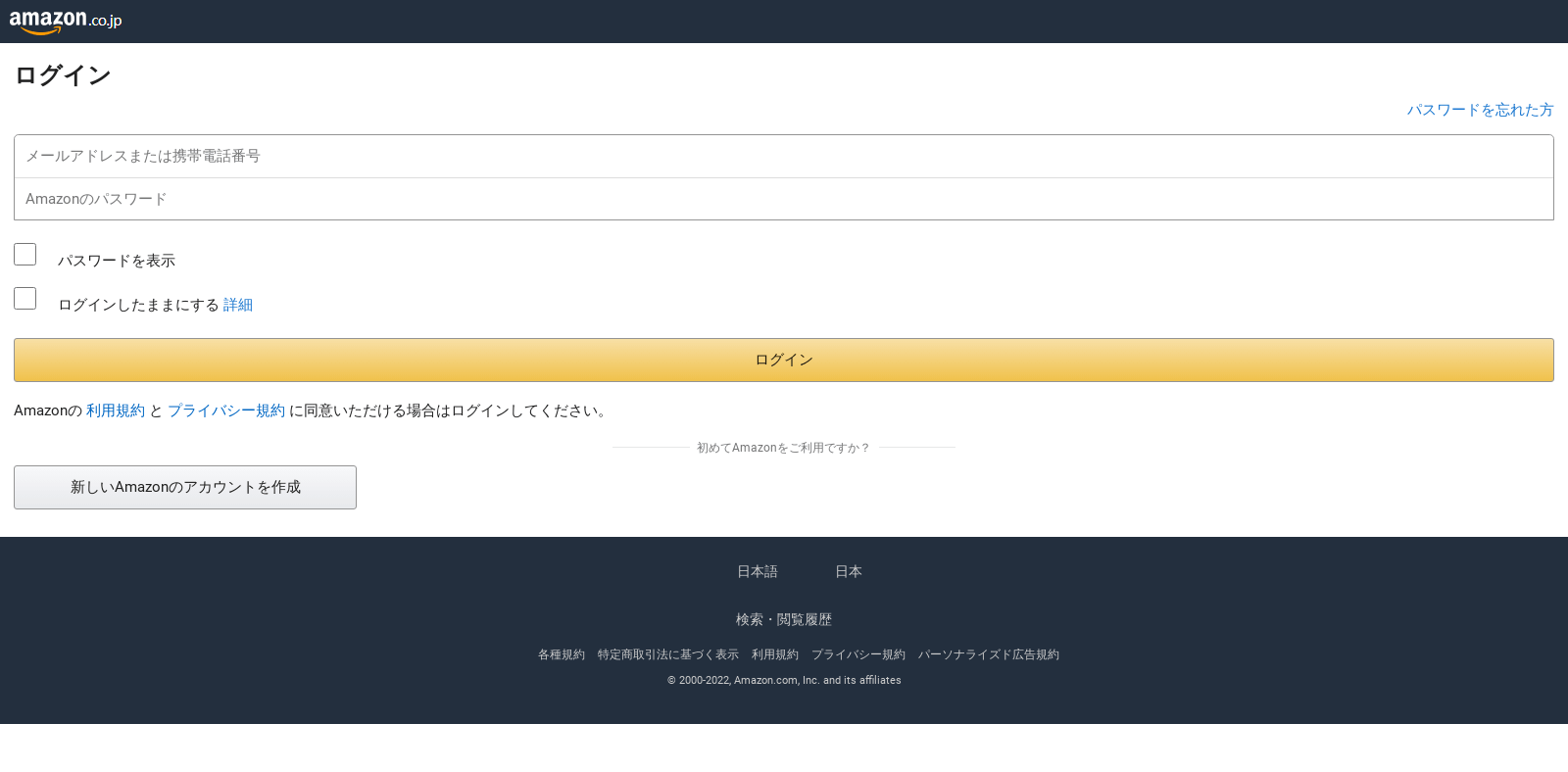
Account Theft Example:
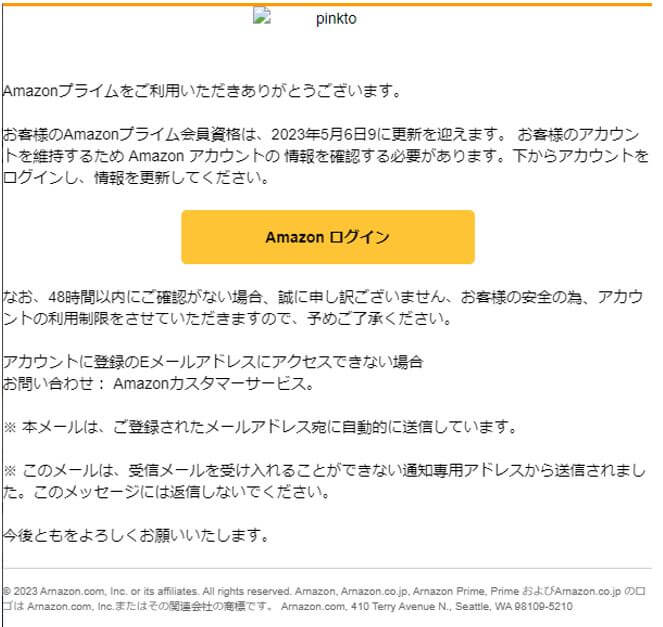
In this phishing mail, there is an attempt to steal a user’s Amazon Prime account information. The email seems like it was sent from “Amazon.co.jp”, but from looking at the email address it is clearly understood that it is phishing (changeid@sfsbupah[.]com). Also, at the bottom of the email, it is written Arnazon instead of Amazon.
The attacker was trying to lure the victim to click on a malicious link, which redirects the user to a fraudulent Amazon login page. In the malicious link https://sftvrepair[.]com the user needed to enter their username and their password.
Subject:【重要なお知らせ】Amazonプライムの自動更新設定を解除いたしました
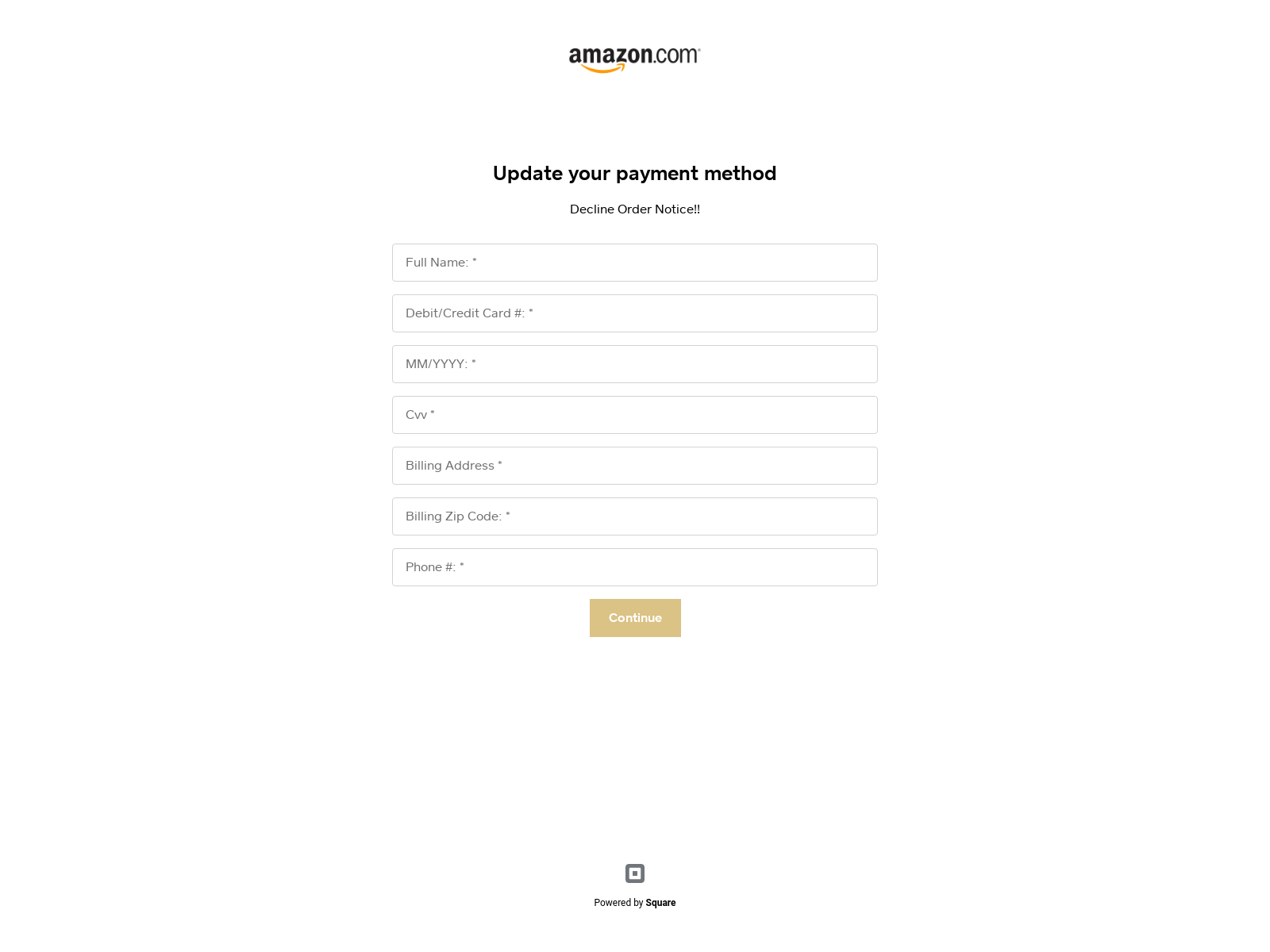
Fake Amazon Payment Page:
CPR found a fraudulent website that was trying to imitate Amazon payment page, using an almost identical replica. The fraudulent website is listed under the address http://amazon-prime-unitsexrctvy4e5rf6gyu[.]square[.]site.
How to Stay Safe Shopping Online on Amazon Prime Day
To help online shoppers stay safe this year, Check Point researchers have outlined practical security and safety tips:
- Watch for misspellings of Amazon.com. Beware of misspellings or sites using a different top-level domain other than Amazon.com. For example, a .co instead of .com. Deals on these copy-cat sites may look just as attractive as on the real site, but this is how hackers fool consumers into giving up their data.
- Before Prime Day, create a strong password for Amazon.com. Once a hacker is inside your account, it is game over. Make sure your password for Amazon.com is uncrackable, well before July 11th .
- Look for the lock. Avoid buying something online using your payment details from a website that does not have secure sockets layer (SSL) encryption installed. To know if the site has SSL, look for the “S” in HTTPS, instead of HTTP. An icon of a locked padlock will appear, typically to the left of the URL in the address bar or the status bar down below. No lock is a major red flag.
- Share the bare minimum. No online shopping retailer needs your birthday or social security number to do business. The more hackers know, the more they can hijack your identity. Always maintain the discipline of sharing the bare minimum when it comes to your personal information.
- Always note the language in the email. Social engineering techniques are designed to take advantage of human nature. This includes the fact that people are more likely to make mistakes when they are in a hurry and are inclined to follow the orders of people in positions of authority. Phishing attacks commonly use these techniques to convince their targets to ignore their potential suspicions about an email and click on a link or open an attachment.
- Beware of “too good to be true” bargains. This will be tough to do, as Prime Day is all about great offers. But, if it seems WAY too good to be true, it probably is. Go with your gut: an 80% discount on the new iPad is usually not a reliable or trustworthy purchase opportunity.
- Stick to credit cards. During Prime Day, it is best to stick to your credit card. Because debit cards are linked to our bank accounts, we are at much higher risk if someone is able to hack our information. If a card number gets stolen, credit cards offer more protection and less liability.
How to protect against phishing emails
Check Point safeguards against the pervasive menace of phishing with its comprehensive 360° Anti-Phishing solutions, which provide all-encompassing security across various platforms such as email accounts, browsers, endpoints, mobile devices, and networks. It employs the revolutionary Check Point ThreatCloud AI, which, equipped with Zero-day phishing protection, scrutinizes hundreds of indicators of compromise in real time, efficiently distinguishing and blocking new and familiar phishing sites. The system meticulously inspects every attribute of incoming emails, including attachments, links, and textual content, substantially reducing risks before the messages even reach the mailbox. Check Point’s solutions, underpinned by ThreatCloud AI’s Zero-Day phishing engine, block 4X more attacks compared to signature based technologies. For organizations grappling with the ceaseless evolution and ingenuity of phishing attacks, Check Point Harmony Email & Office provides much-needed visibility and defense against diverse phishing strategies. Therefore, it’s crucial that organizations harness the power of advanced anti-phishing solutions such as these to counteract the cyber threats that exploit human nature as their weakest link.



