Highlights:
- 58% of local governments are facing ransomware attacks.
- $2.07 million is the average ransom demand.
- Save the Date – May 30th: Protect local government services & data.
At a Royal Mail distribution office in Ireland, on Wednesday the 11th of January 2023, employees were met with the sudden whirr of printers. Extruded from every printer in tandem were copies of one message: “Lockbit Black Ransomware. Your data are [sic] stolen and encrypted”. What followed was major disruption to international shipments as Royal Mail struggled to support global customers and prop up failing internal IT systems.
Unknown to Royal Mail staff and customers, ransomware had scrambled large swathes of the international shipping database. Tense negotiations soon began, as attackers demanded $80 million in return for the data decryption key. Though initially pinned on the organized crime group Lockbit, researchers established that the actual attack had originated from an affiliate of its Ransomware as a Service (RaaS) program. Royal Mail made no official declaration on the payment of its ransom. Instead, the organization claimed to have set up ‘operational workarounds’ for some affected systems to be bypassed.
This Russian-linked attack targeting a major logistical institution – responsible for handling billions of parcels a year – is only one of dozens of recent governmental victims. Cyber attacks have exploded throughout the last few years, a complex mix of institutional weaknesses and freely-available attack methods.
Local Governmental Institutions are Most at Risk
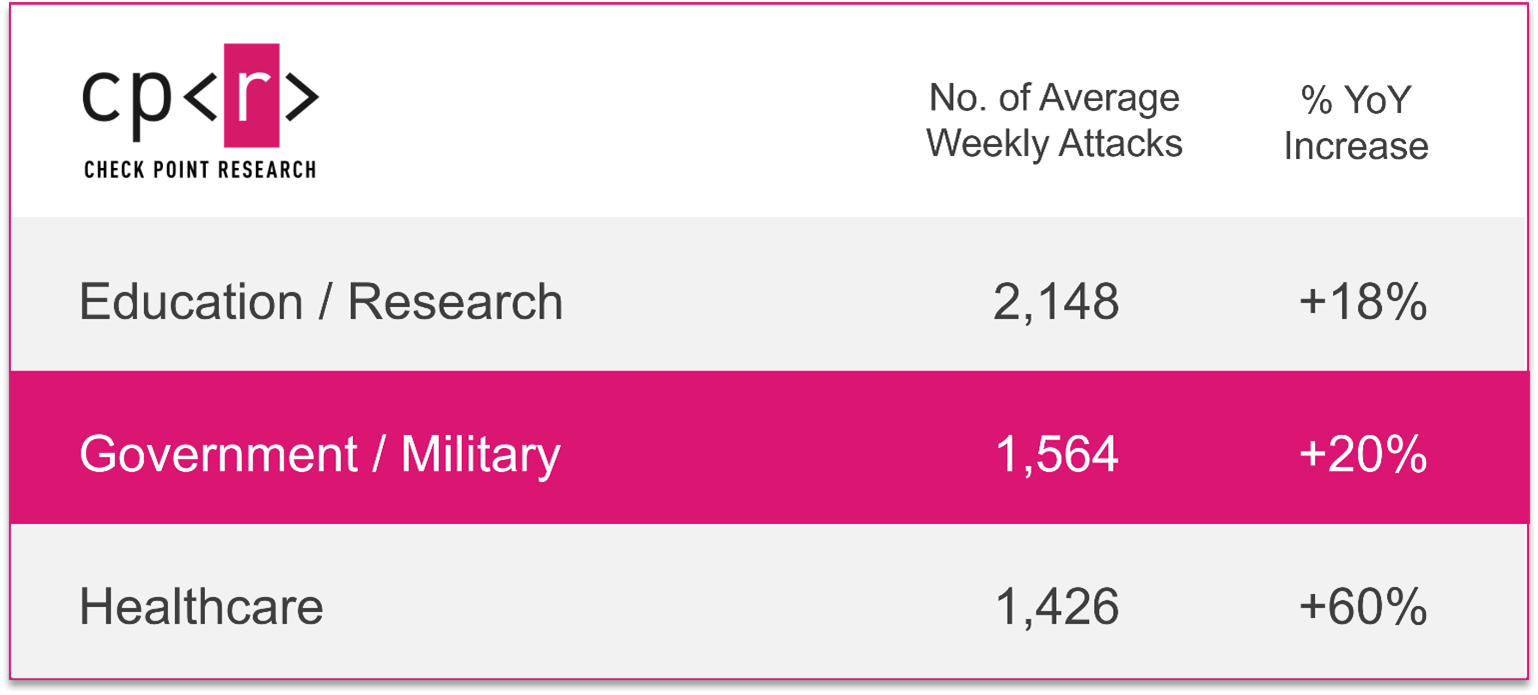
Governmental institutions are responsible for the wellbeing of entire populations. The sheer complexity facing each group – from tax compliance to social service management – is often a side-effect of the numerous systems and contractors running through each department.
Technology-enabled resources are a double-edged sword: on one hand, they lend citizens constant access to governmental aid and information. On the other hand, mismanaged systems afford attacks with increasingly-higher blast radii. The World Economic Forum, in its 2023 Global Risks report, identified the danger of this intertwining of technology and governmental services. Cyber threats on critical infrastructure are predicted to grow to the same scale as today’s energy, living cost, and food supply crisis this year.
The last few years have seen the rise of one form of cyberattack in particular. The rise of politically motivated hacktivism groups has spread from Iran’s ‘Hackers of Savior’ to the ‘IT Army of Ukraine’. Cyberspace has become a vital component of modern conflict, superseding the geographic constraints of international disputes. While the 350,000 global members of Ukraine’s IT Army fight to disrupt Russian communications and uncover intel, Russia’s well-established Killnet group has spent January 2023 launching espionage phishing attacks at the Latvian Ministry of Defense.
The state of modern cybercrime has given not just state-funded actors an opening to commit serious damage – irate individuals are now also provided the chance to unleash havoc, with attack kits purchasable on the dark web. Local governments represent one of the most vulnerable victims, largely thanks to the infrastructure they’re defending and the limited budget they have to do so. The high volume of confidential information being handled by local governments span the width of criminal records, confidential communications, and citizen contact information. Each of these represents highly lucrative opportunities for the aspiring cybercriminal: contact info can help execute highly-specific phishing campaigns, while data breaches lend more ammunition to malicious international regimes. The importance of such data and systems to ordinary working citizens also lends significant weight to database-disrupting ransomware attacks.
As the federal government dictates each state’s budget via grants and aid programs, local governments are placed at the vulnerable end of each attacker’s scope. Flexibility surrounding funding is one of the largest components to attack recoverability, and local governments are simply not afforded the same defense agility. Small budgets and scant resources mean that local governors have traditionally dedicated the majority of funding to more palpable programs, aimed at benefiting the local community. While understandable, public transport cannot protect against Russian-funded espionage campaigns – and the cost of prevention is far lower than that of cyber attack recovery.
With the average ransom demand skyrocketing to $2.07 million in 2022. 2023 looks to be defined by a new understanding of cybersecurity for governments.
What Can Local Governments Do to Protect Themselves?
Governmental cybersecurity requires modernization in two fields: strategy and solution. The Federal US government is already laser-focusing on the first, with a very recent announcement made by the Biden-Harris administration detailing two key focal points. First, the balance of responsibility is changing: individuals and small businesses should be able to turn to dedicated organizations that can help reduce risk for all. Even in its infancy, this is proving beneficial: Royal Mail turned to the UK’s National Cyber Security Centre for help with its ransom negotiations, and the UK government is building on this with the establishment of a Government Cyber Coordination Centre (GCCC). This process demonstrably sets the foundation for higher cyberattack resilience throughout local and federal levels.
From there, Biden emphasizes a focus on long-term investment. A tightrope between urgent threats and future-proof architecture needs to be walked. Facilitating this is a strategic solution that provides and maintains cybersecurity for governments. Currently, many security architectures are built out of a hodgepodge assortment of different products. While this approach targets individual vulnerabilities, the constant management necessary to create a cohesive security stance far exceeds the time and financial budget accessible to local governments.
Leverage Advanced Capabilities with Check Point
Check Point Infinity recognizes that the whole is greater than the sum of its parts. Consolidating all architecture under one security platform, organizations are afforded far greater visibility, faster threat intel, and easier management.
Check Point provides uniform protection throughout local government by focusing on comprehensive, consolidated, and collaborative security.
A security platform designed to guard against today’s critical zero-day and fifth-generation threats across the network, cloud, IoT, and endpoints. Check Point Infinity architecture leverages Check Point’s ThreatCloud AI, a real-time global threat intelligence platform that monitors networks around the world for emerging threats and vulnerabilities.
Our comprehensive defense makes us the security choice of multiple counties, municipalities, and the European Space Agency (ESA).
To begin your journey toward security consolidation, an Infinity expert is happy to guide you through your threat posture, and determine which tailor-made offering can bring your security architecture in line with the demands of 2023.
Join us on May 30th to discover how to protect local government services and data
Hosted by Check Point’s Growth Evangelist with a panel of leading Heads of Engineering











