Highlights:
- Check Point Research (CPR) reveals a growing industry selling credentials to stolen hotel and airline accounts.
- End goal is to get access to accounts with reward points and sell it.
- CPR provides examples including dedicated brute forcing tool used to steal accounts, stolen credentials on sale and “travel agents” selling discounted flights retrieved using stolen airline / hotel accounts.
Background
With airline prices skyrocketing these days, amidst the global inflation, people are always seeking last minute sales, special offers and will usually be tempted to follow any lucrative offer that will decrease the heavy prices we all need to pay towards our next vacation.
It seems that hackers and cybercriminals leverage this, as always, in their quest to maximize profits and leverage a need that requires a resolution.
In this report, Check Point Research turns a spotlight into what seems like a growing phenomenon, in which cybercriminals are offering a variety of deals for those who seek to cut back on their expenses, while trying to get to their vacation’s destination.
Leverage your reward points, even if they are not your own!
Our researchers present examples to what seems to be a growing market on alternative pathways in which threat actors and cybercriminals offer their “goods”, using stolen credentials to airline and hotel personal accounts, or accumulated rewards that can be used to buy tickets or hotel nights.
One method cybercriminals use is offering stolen credentials of hotel and airline accounts that have accumulated reward or flight points. These stolen credentials are offered for free or for sale on hacking Darknet forums. Examples of such accounts include hotels like Marriott, Delta, and AA. Cybercriminals also use a dedicated brute forcing tool to steal accounts from Radisson Hotel with the end goal of accessing accounts with reward points or linked payment cards.
Another tactic is the creation of “travel agencies” in Russian hacking underground markets. These agencies offer flight tickets and hotel bookings at 45-50% discounted prices. However, these deals are ordered using stolen accounts from hotels, airlines, and other travel-related websites.We also present two examples of phishing (Vietnam Airlines) and mal spam (SouthWest) examples impersonating airlines.
In this visual below, you can see that the market platform offers tickets of leading global airlines.
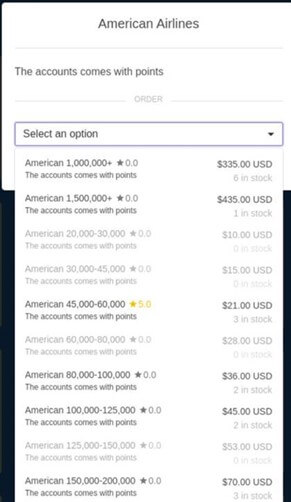
 Trade of stolen accounts with reward/flight points
Trade of stolen accounts with reward/flight points
Here we show what is being offered, when requesting to purchase accounts which includes points in them. As the screenshot shows, an American Airlines account holding 1,500,000+ points is sold for $435.
Interested in Hotel reward point? Free nights in Marriot? We got what you need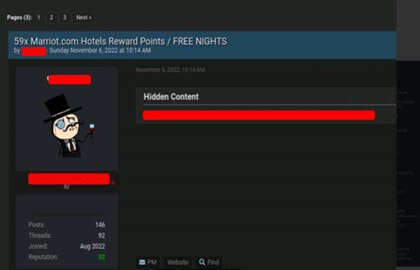
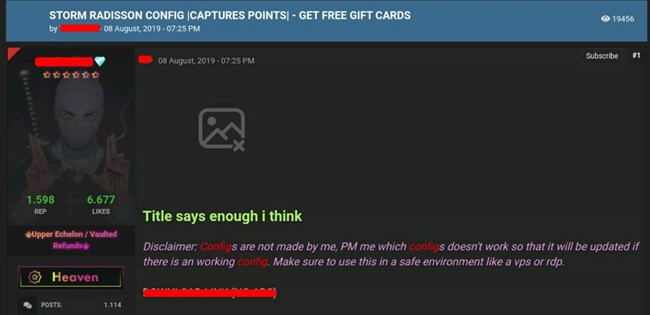
Specifically interested in Radisson account rewards? Don’t worry, these guys will sell you the tool to brute force any account and get its captured points!
A brute force tool is a type of software or program used to crack or guess a password or encryption key by attempting every possible combination of characters until the correct one is found. Brute force tools are often used by hackers to gain unauthorized access to computer systems, networks, and online accounts.

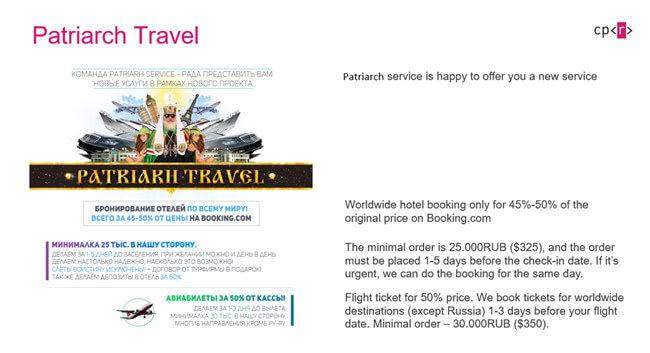
Underground alternative “travel agents” selling reduced prices tickets!
Patriarch service is offering buyers 45-50% reduced prices off an original booking that can be found on legitimate booking outlets around the net.
These reduced prices are received using stolen accounts of airlines and hotels obtained by the operating cybercriminals who offer these services.
The ad which appears on the Darknet (originally in Russian, here also translated to English by CPR) offering tickets for worldwide destinations, except Russia and has a minimal order of $325.
Phishing a better deal
Phishing scams remain a major technique used by cybercriminals to lure users to provide their details, financial details preferable, and by that, steal funds and generate fraudulent transactions.
In this, travel scams aren’t exceptional and in this report we provide examples of 2 cases where cybercriminals impersonate legitimate firms to lure their victims.
In this case, we see a phishing website for the Vietnam Airline website. It offers deals and information, inviting buyers to book trips. This was presented under a lookalike domain https://vietnam-airline\.org
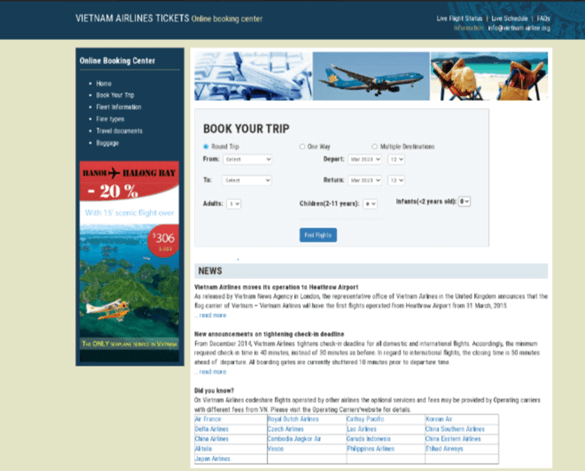
Phishing Vietnam Airlines website
On our second example we show a malspam campaign sent to victims claiming they won a reward in the name of SouthWest Airline company (similar campaigns seen in other airlines companies as well).
The mail was sent from different senders, with name headers such as ‘Southwest Airlines Feedback’ or ‘You’re Approved’.
An example of the mail:

How to protect yourself from travel scams online:
- Be wary of deals that seem too good to be true: Scammers often use enticing deals to lure in unsuspecting travelers. If a deal seems too good to be true, it probably is. Nobody will sell you a 50% off ticket price
- Use secure payment methods: When booking a trip online, use a secure payment method such as a credit card or PayPal. These methods offer protection against fraudulent charges and make it easier to dispute any unauthorized transactions.
- Check for HTTPS: When making any online transaction, including booking a trip, make sure the website has HTTPS in the URL. This indicates that the website has an SSL certificate, which means the data you enter is encrypted and secure.
- Prior to booking with a company online, make sure you know who are you buying from. Check its website, accumulate others’ reviews and research if someone has heard of this company before
- Check web addresses– Another easy way to identify potential phishing attacks is to look for mismatched email addresses, links, and domain names. Recipients should always hover over a link in an email before clicking it, to see the actual link destination. If the email is believed to be sent by American Airlines, but the domain of the email address does not contain “americanairlines.com”, that is a sign of a phishing email.










