
Stop Chasing Breaches: Build a Resilient Security Architecture
You assume your security architecture is secure, it’s not always the case
Cyber security vendors play a critical role in protecting the digital landscape. However, security products, too, are not immune from targeted exploits by bad actors. Cyberattacks can happen to anyone, anytime with a vulnerability in hardware and software. It’s important for your security partners to adopt secure coding practices and thorough security testing throughout the development lifecycle.
It doesn’t always happen that way.
This blog highlights a pattern of several vendors suffering from critical breaches, and the importance of your vendors to immediately respond with a patch or an effective alternative solution. Following are several incidents where state-backed or major hacking groups exploited critical flaws within large security systems. Unfortunately, patches were delayed exposing customer systems for long periods of time.
Palo Alto Networks
On April 12, 2024, Volexity, a memory forensics firm, identified a zero-day exploitation found within the GlobalProtect feature of the Palo Alto Networks PAN-OS. Their investigation determined the device had been compromised, with a maximum possible severity of 10/10.[1] Palo Alto assigned it CVE-2024-3400[2]
According to Volexity, they identified and tracked this critical vulnerability actively exploited several customers by a threat actor called UTA0218.
This Exploitation was observed through on course of several days and active exploit was active on several customers with Palo Alto Networks GWs running GlobalProtect.
Fortinet 2023
The chart below describes a CISA advisory with documented breaches rated critical or high with Fortinet products.
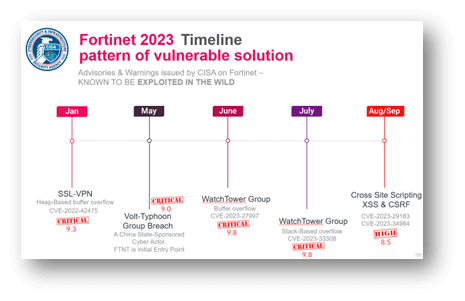
https://labs.watchtowr.com/xortigate-or-cve-2023-27997/
https://thehackernews.com/2023/07/new-vulnerabilities-disclosed-in.html
https://www.cisa.gov/known-exploited-vulnerabilities-catalog
CISCO
‘ArcaneDoor’ Cyberspies Hacked Cisco Firewalls to Access Government Networks. sources suspect China is behind the targeted exploitation of two zero-day vulnerabilities in Cisco’s security appliances. Critical Vulnerabilities CVE-2024-20353 with high severity of 8.6 and CVE-2024-20359 were used by the attacker in this campaign.[1]
Cyberattacks are seldom isolated
The impact of a cyberattack can extend far beyond the initial breach. A case in point is when the Palo Alto Networks breach (CVE-2024-3400) went public, the news was used by the hacker community to make a tough situation worse. The bad actors jumped on the bandwagon to exploit the vulnerability in the wild.
The below image describes the additional global exploitation of the vulnerability after it had already become public knowledge.
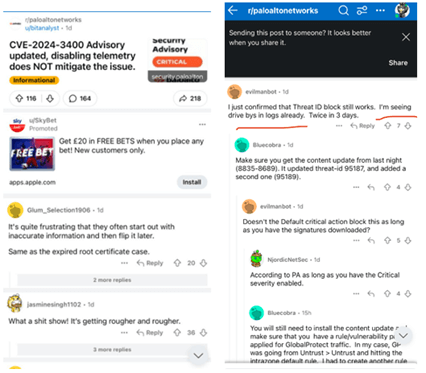
The same vendors faced more critical vulnerabilities that were actively exploited in the real world according to CISA’s known exploited vulnerabilities list. Despite the severity, patching remained sluggish.
Looking into CISA (Cyber Security & Infrastructure Security Agency), that publishes actively exploited in the wild vulnerabilities and issues security bulletins and advisories as published in known exploited vulnerabilities catalog is alarming as there are many more where those came from.


Choose your vendors with the right track record
As highlighted in these incidents, your security vendor must have your back. They should be ready to take every action necessary to provide quality security. Check out your vendors’ track record. How consistent have they been in providing proactive and rapid responses versus the delays of remediating compromised systems.
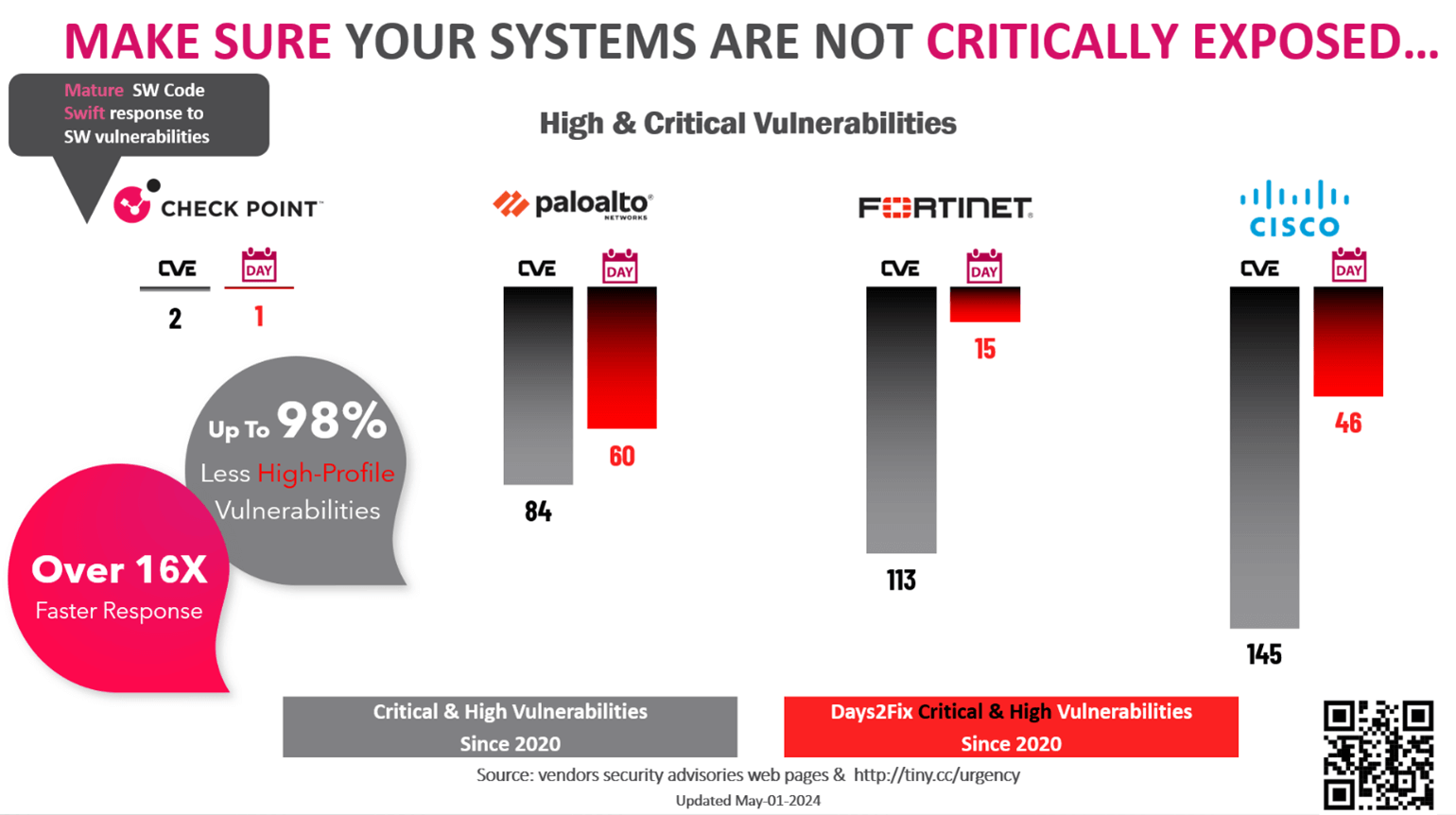
When it comes to high severity vulnerabilities, the security vendor you do business with can become a make-or-break situation to protect your organization. The following chart’s identity that not all security vendors respond effectively to critical and high severity vulnerabilities.
The list of vulnerabilities can be obtained on a vendor’s security advisory public web sites.
Critical and High Severity Vulnerabilities In Critical & High Severity, Check Point Software fixes major vulnerabilities up to 16X faster than the competition with up to 98 percent less high-profile vulnerabilities on its own security solutions.
Overall Security
Ideally, all security vendors should develop secure products and openly communicate documented security vulnerabilities and the time it takes to patch, regardless of severity.
Overall, Check Point Software fixes vulnerabilities up to 16X faster than the competition and has up to 98 percent less vulnerabilities with its own security solutions.

Check Point provides a true cyber security architecture with the Infinity Platform, AI-powered, cloud-delivered. It encompasses more than 70 security & ML engines and provides services including AI Co-Pilot. Experts can respond to requests in real-time or in under 24 hours.
Be ready to protect against sophisticated attacks
History tells us that every new innovative service loses ground to a “good enough” competitor. As we have seen an increase in attacks like:
- Toronto Public Library Data Breach (November 2023): A sophisticated ransomware attack targeted the Toronto Public Library, compromising employee, volunteer, and customer data.
- Costa Rican Government Data Breach (May 2024): The Conti ransomware gang hacked the Costa Rican government, demanding a ransom and leaking stolen data.
- Additional breaches with Twitter, SAP, 23andMe, MOVEit, DarkBeam indicate a pattern – organizations taking the “good enough” security approach, lost the cyber battle. While “good enough” or “2nd best” may be fitting for smartphones or TV’s, it’s a dangerous proposition when it comes to cyber security.
Why it’s time to demand more from cyber security
A “good enough” approach to cyber security can often be pushed by vendors that prioritize short-term cost-savings over long-term security effectiveness. This can leave an organization dangerously exposed to evolving cyber threats.
To avoid this trap, security leaders need to ask critical questions during their cyber security strategy evaluation:
- Can we afford “Good Enough” security? Consider the full cost of a breach. Damaged reputation, lost data, and regulatory fines can far outweigh the initial investment in robust security solutions.
- What are the risks specific to my organization?
This question is the cornerstone of building a successful cybersecurity strategy. A “one-size-fits-all” approach simply will not cut it - Going beyond “Good Enough:” Are you truly maximizing your security posture? Is your current approach a comprehensive shield against modern cyberattacks?
- Security investments: Demanding transparency: Ask tough questions about what your security investments are actually buying. Do not settle for vague promises – demand clear explanations about how your chosen solution actively protects your organization.
Check Point’s Infinity Platform: Best-in-class collaborative cyber security
For three decades, Check Point has established itself as a leader in the security industry. Our commitment to delivering real-world protection is reflected in the trust we have earned from customers, partners, and independent evaluation bodies like Gartner, Forrester, CyberRatings, and Miercom.
Check Point offers several customer benefits, including:
- Unwavering Protection: Security is our core focus. We prioritize real-world effectiveness in every product and service we offer.
- Uncompromising Consistency: We reject the “gear up for tests” approach. Every day, we strive to deliver best-in-class solutions and support for our customers and partners.
- Proven Reliability: From firewalls and IPS solutions to Next-Generation Firewalls, Advanced Threat Prevention, and comprehensive Threat Intelligence, Check Point Software delivers a holistic security platform with a history of innovation and leadership.
- Unrelenting Pursuit of Excellence: We continuously push boundaries to provide industry-leading products, services, and support across the board.
To learn more about the AI-powered, cloud-delivered Infinity Platform and how Infinity Platform Services can help you build a resilient cyber security architecture, please visit this page.
[1] https://www.volexity.com/blog/2024/04/12/zero-day-exploitation-of-unauthenticated-remote-code-execution-vulnerability-in-globalprotect-cve-2024-3400/
[2] https://labs.watchtowr.com/palo-alto-putting-the-protecc-in-globalprotect-cve-2024-3400/
[3] https://www.wired.com/story/arcanedoor-cyberspies-hacked-cisco-firewalls-to-access-government-networks/https://sec.cloudapps.cisco.com/security/center/resources/asa_ftd_attacks_event_response



