January’s Most Wanted Malware: Cryptomining Malware Continues to Cripple Enterprise CPU Power
Check Point’s latest Global Threat Index reveals continued increase in the use of cryptomining malware among hackers
In January, cryptomining malware continued to be the most prevalent with Coinhive retaining its most wanted spot impacting 23 percent of organizations, followed by Fireball in second and Rig Exploit Kit in third impacting 17 percent of organizations. The Fireball malware impacted one-in-five organizations across the world, according to Check Point’s Global Threat Index’s Top 10 most prevalent malware.
Check Point researchers discovered that 21 percent of organizations have still failed to remove the Fireball malware from infected machines. Fireball, which can be used as a full-functioning malware downloader capable of executing any code on victims’ machines, was first discovered in May 2017 and severely impacted organizations during the summer of 2017.
Check Point researchers also discovered three different variants of cryptomining malware in its top 10 most prevalent ranking, with Coinhive ranking first, impacting more than one-in-five organizations. Coinhive implants a Javascript on unsuspecting website visitors that uses the computational resources of the end user’s machines to mine “Monero” coins, impacting system performance.
Over the past three months, cryptomining malware has steadily become an increasing threat to organizations, as criminals have found it to be a lucrative revenue stream. It is particularly challenging to protect against, as it is often hidden in popular websites, enabling hackers to use their victims’ machines as their own massive enterprise-sized CPU resource.
The current threat landscape is defined by large-scale and fast-moving Gen V (Fifth Generation) cyber-attacks. It is therefore more important than ever for enterprises to protect themselves using Gen V level cybersecurity technologies.
January 2018’s Top 3 ‘Most Wanted’ Malware:
*The arrows relate to the change in rank compared to the previous month.
- ↔Coinhive – Crypto-Miner designed to perform online mining of Monero cryptocurrency when a user visits a web page without the user’s approval.
- ↑ Fireball – Browser-hijacker that can be turned into a full-functioning malware downloader.
- ↔ Rig ek – Rig delivers Exploits for Flash, Java, Silverlight and Internet Explorer
- ↔ Roughted – Large scale Malvertising used to deliver various malicious websites and payloads such as scams, adware, exploit kits and ransomware.
- ↑JSEcoin – JavaScript miner that can be embedded in websites.
- ↔ Globeimposter – Ransomware disguised as a variant of the Globe ransomware. Upon encryption, the ransomware appends the .crypt extension to each encrypted file.
- ↑ Andromeda – Modular bot used mainly as a backdoor to deliver additional malware on infected hosts.
- ↓ Cryptoloot – Crypto-Miner that uses the victim’s CPU or GPU power and existing resources for crypto mining – adding transactions to the blockchain and releasing new currency.
- ↓ Ramnit – Banking Trojan that steals banking credentials, FTP passwords, session cookies and personal data.
- ↑ Nivdort – Multipurpose bot used to collect passwords, modify system settings and download additional malware.
Lokibot, an Android banking Trojan, was the most popular malware used to attack organizations’ mobile estates followed by the Triada and Hiddad.
January’s Top 3 ‘Most Wanted’ mobile malware:
- Lokibot – Android banking Trojan and info-stealer, which can also turn into a ransomware that locks the phone.
- Triada – Modular Backdoor for Android which grants superuser privileges to downloaded malware.
- Hiddad – Android malware which repackages legitimate apps then releases them to a third-party store.
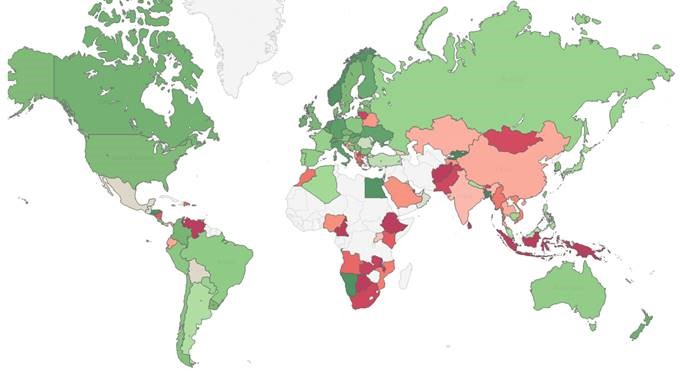
The map below displays the risk index globally (green – low risk, red- high risk, white – insufficient data), demonstrating the main risk areas and malware hot-spots around the world.
Check Point’s Global Threat Impact Index and its ThreatCloud Map are powered by Check Point’s ThreatCloud intelligence, the largest collaborative network to fight cybercrime which delivers threat data and attack trends from a global network of threat sensors. The ThreatCloud database holds over 250 million addresses analyzed for bot discovery, more than 11 million malware signatures, over 5.5 million infected websites, while also identifying millions of malware types daily.
* The complete list of the top 10 malware families in December can be found on the Check Point Blog.
Check Point’s Threat Prevention Resources are available at: http://www.checkpoint.com/threat-prevention-resources/index.html
Follow Check Point via:
Twitter: http://www.twitter.com/checkpointsw
Facebook: https://www.facebook.com/checkpointsoftware
Blog: http://blog.checkpoint.com
YouTube: http://www.youtube.com/user/CPGlobal
LinkedIn: https://www.linkedin.com/company/check-point-software-technologies
About Check Point Software Technologies Ltd.
Check Point Software Technologies Ltd. (www.checkpoint.com) is a leading provider of cyber security solutions to governments and corporate enterprises globally. Its solutions protect customers from cyber-attacks with an industry leading catch rate of malware, ransomware and other types of attacks. Check Point offers a multilevel security architecture that defends enterprises’ cloud, network and mobile device held information, plus the most comprehensive and intuitive one point of control security management system. Check Point protects over 100,000 organizations of all sizes.