
CISA’s 2021 Top-15 routinely exploited Vulnerabilities – Check Point customers remain fully protected
03/05/2022
Background
In a joint advisory published On April 27, the Cybersecurity & Infrastructure Security Agency (CISA)- in collaboration with CSA/NSA/FBI/ACSC and other cybersecurity authorities provided details on the top 15 Common Vulnerabilities and Exposures (CVEs) routinely exploited by malicious cyber actors in 2021, as well as other CVEs frequently exploited.
Security researchers at Check Point are constantly monitoring such vulnerabilities, and have been reporting exploitation attempts during the past year, such in the cases of Spring4Shell and the Log4j vulnerability.
The following graph shows the highest monthly volume of impacted organizations worldwide seen during 2021, by attacks attempting to exploit these published vulnerabilities.
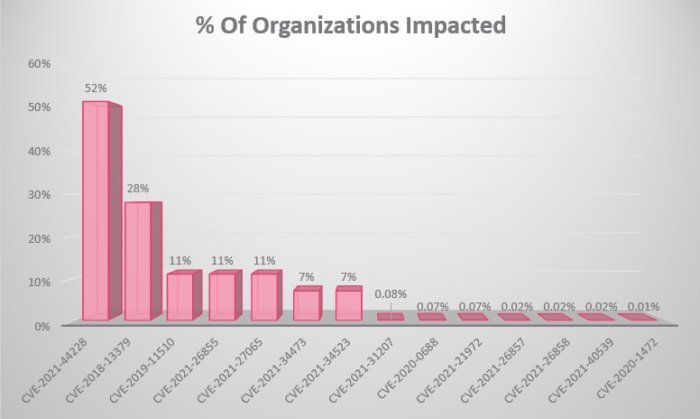
Check Point’s assessment is based on ThreatCloud, our real-time threat intelligence derived from hundreds of millions of sensors worldwide.
Threat actors targeting internet facing systems such as email servers and virtual private networks (VPN)
The top vulnerabilities outlined in the CISA Alert detailing how threat actors exploited newly disclosed vulnerabilities in popular services, aiming to create as massive and extended impact on organizations.
Nine of the top 15 routinely exploited flaws were remote code execution(RCE) vulnerabilities, followed by two privilege escalation weaknesses.
Top vulnerabilities include:
- CVE-2021-44228. This vulnerability, known as Log4Shell, affects Apache’s Log4j library, an open-source logging framework. Apache Log4j is the most popular java logging library with over 400,000 downloads from its GitHub project. It used by a vast number of companies worldwide, enabling logging in a wide set of popular applications. Exploiting this vulnerability is simple and allows threat actors to control java-based web servers and launch remote code execution attacks.
- CVE-2021-26855, CVE-2021-26858, CVE-2021-26857, CVE-2021-27065. These vulnerabilities, known as ProxyLogon, affect Microsoft Exchange email servers. Successful exploitation of these vulnerabilities in combination (i.e., “vulnerability chaining”) allows an unauthenticated cyber actor to execute arbitrary code on vulnerable Exchange Servers, which, in turn, enables the actor to gain persistent access to files and mailboxes on the servers, as well as to credentials stored on the servers.
- CVE-2021-34523, CVE-2021-34473, CVE-2021-31207. These vulnerabilities, known as ProxyShell, also affect Microsoft Exchange email servers. Successful exploitation of these vulnerabilities in combination enables a remote actor to execute arbitrary code. In September 2021 it was reported that The Conti ransomware gang has been hacking into Microsoft Exchange servers using the Proxyshell exploits that allow remote code execution on unpatched servers.
- CVE-2021-26084. This vulnerability, affecting Atlassian Confluence Server and Data Center, could enable an unauthenticated actor to execute arbitrary code on vulnerable systems. This vulnerability quickly became one of the most routinely exploited vulnerabilities. Attempted mass exploitation of this vulnerability was observed in September 2021, with threat actors were actively seeking ways to exploit in order to install crypto miners.
Check Point Customers are fully protected against all published exploited vulnerabilities
Check Point’s Quantum Intrusion Prevention System (IPS) prevented attempts to exploit weaknesses in vulnerable systems and applications, protecting in the race to exploit these vulnerabilities.
Check Point IPS protections in our Next Generation Firewall are updated automatically and does not require actions from the users.
Check Point’s Harmony Endpoint prevented log4j related attacks and accelerated detection and investigation of related breaches. Check Point’s teams created several detection and prevention signatures to protect endpoints from the log4j vulnerability. These signatures apply to both Windows and Linux endpoints. The signatures have been added to the Harmony Endpoint behavioral guard engine.
The engine adds a protection layer against advanced attacks by detecting suspicious operations in the behavior of processes.
Check Point’s Infinity Platform is the only security platform that offered pre-emptive protection for customers against recent Log4j exploits(Log4Shell). Leveraging contextual AI, the platform provides precise prevention of even the most sophisticated attacks, without generating false positives. Customer web applications remain safe as the security auto updates without the need for human intervention or CloudGuard AppSec provides zero-day protection from exploiting the Log4j vulnerability using Check Point Web Application Best Practice in Prevent mode.
As soon as the Log4j vulnerability was reported on December 9, all relevant protections were propagated through all of Check Point products (sk176884).
Enclosed is a detailed list of our IPS protections against all the published vulnerabilities by CISA:
| CVE | Vulnerability Name | Vendor and Product | Type | IPS Protection |
| CVE-2021-44228 | Log4Shell | Apache Log4j | Remote code execution (RCE) | Apache Log4j Remote Code Execution (CVE-2021-44228; CVE-2021-45046) |
| CVE-2021-40539 | Zoho ManageEngine AD SelfService Plus | RCE | Zoho ManageEngine ADSelfService Plus Authentication Bypass (CVE-2021-40539) | |
| CVE-2021-34523 | ProxyShell | Microsoft Exchange Server | Elevation of privilege | Microsoft Exchange Server Remote Code Execution (CVE-2021-34473; CVE-2021-34523) |
| CVE-2021-34473 | ProxyShell | Microsoft Exchange Server | RCE | Microsoft Exchange Server Remote Code Execution (CVE-2021-34473; CVE-2021-34523) |
| CVE-2021-31207 | ProxyShell | Microsoft Exchange Server | Security feature bypass | Microsoft Exchange Server Security Feature Authentication Bypass (CVE-2021-31207) |
| CVE-2021-27065 | ProxyLogon | Microsoft Exchange Server | RCE | Microsoft Exchange Server Remote Code Execution (CVE-2021-26855; CVE-2021-27065) |
| CVE-2021-26858 | ProxyLogon | Microsoft Exchange Server | RCE | Microsoft Exchange Server Remote Code Execution (CVE-2021-26857; CVE-2021-26858) |
| CVE-2021-26857 | ProxyLogon | Microsoft Exchange Server | RCE | Microsoft Exchange Server Remote Code Execution (CVE-2021-26857; CVE-2021-26858) |
| CVE-2021-26855 | ProxyLogon | Microsoft Exchange Server | RCE | Microsoft Exchange Server Remote Code Execution (CVE-2021-26855; CVE-2021-27065) |
| CVE-2021-26084 | Atlassian Confluence Server and Data Center | Arbitrary code execution | Atlassian Confluence Remote Code Execution (CVE-2021-26084) | |
| CVE-2021-21972 | VMware vSphere Client | RCE | VMware vSphere Client Remote Code Execution (CVE-2021-21972; CVE-2021-21973) | |
| CVE-2020-1472 | ZeroLogon | Microsoft Netlogon Remote Protocol (MS-NRPC) | Elevation of privilege | Microsoft Netlogon Elevation of Privilege (CVE-2020-1472) |
| CVE-2020-0688 | Microsoft Exchange Server | RCE | Microsoft Exchange Server Remote Code Execution (CVE-2020-0688) | |
| CVE-2019-11510 | Pulse Secure Pulse Connect Secure | Arbitrary file reading | Pulse Connect Secure File Disclosure (CVE-2019-11510) | |
| CVE-2018-13379 | Fortinet FortiOS and FortiProxy | Path traversal | Fortinet FortiOS SSL VPN Directory Traversal (CVE-2018-13379) |
From SolarWinds to Log4j: The global impact of today’s cybersecurity vulnerabilities
If the past year has taught businesses anything, it’s that the impact of targeted cyberattacks and security vulnerabilities is now, without doubt, universal. From the fallout of the SolarWinds software supply-chain attack to the exposed Apache Log4j vulnerability, the case for organizations of all shapes and sizes to have a comprehensive and robust security infrastructure in place has never been stronger, even if they themselves aren’t necessarily in the cross-hairs. These zero-day vulnerabilities earn their name from their ability to completely blindside businesses, giving them virtually no time to react before they become potential victims. It then becomes a race between threat actors and their ability to exploit the vulnerability, and how quickly businesses can close the gap in their defenses.
Keeping Your Organization Safe
- We strongly recommend users to patch their servers, operating systems(including mobile OS) and apps in order to prevent exploitations of such vulnerabilities
- Intrusion Prevention System (IPS) prevents attempts to exploit weaknesses in vulnerable systems or applications, protecting you in the race to exploit the latest breaking threat. Updated IPS helps your organization stay protected.
- Endpoint protections: Conventional signature-based Anti-Virus is a highly efficient solution for preventing known attacks and should definitely be implemented in any organization, as it protects against a majority of the malware attacks that an organization faces. In addition, comprehensive endpoint protection at the highest security level is crucial in order to avoid security breaches and data compromises
- By implementing network segmentation, access management, and a zero trust security strategy, an organization can limit an attacker’s ability to move through the network and take advantage of their initial access to corporate systems. This significantly decreased RCE attack threats.
- If you need help addressing an RCE or any other cyberattack, contact our Incident Response teams. You do not have to be a Check Point customer to do so.









