
8 Million Dollars Stolen in a Uniswap Phishing Attack
By : Oded Vanunu, Dikla Barda & Roman Zaikin
Uniswap is a leading decentralized crypto exchange that runs on the Ethereum blockchain, which uses a decentralized network protocol. The protocol facilitates automated transactions between cryptocurrency tokens on the Ethereum blockchain using smart contracts. Yesterday, the Binance CEO @cz_binance triggered an alarm when he tweeted about a potential exploit on Uniswap:
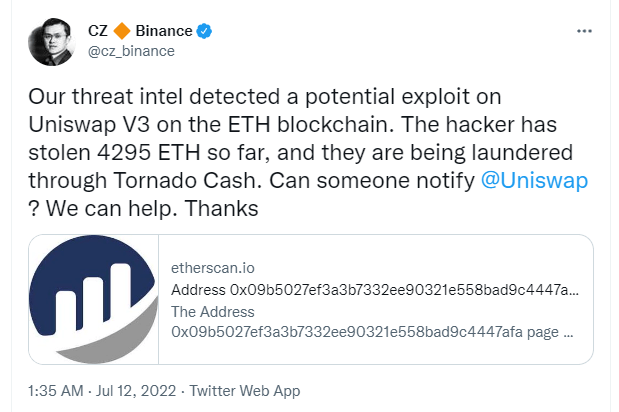
Blockchain explorers such as etherscan.io are commonly used as archives for transactions and give the users information about tokens before they decide to invest in them or not. Many hackers use these blockchain explorers to mislead the users and give false information, making them believe that the token/contract is legitimate. In this case, attackers created a simple ERC20 token and airdropped (sent it for free) it to users that hold UNI tokens. The goal of this airdrop was to lure the victims to the attacker’s scam website. The phishing campaign is successfully as that the transaction of the airdrop seems legitimate at etherscan.io
as can be seen in the following screenshot:
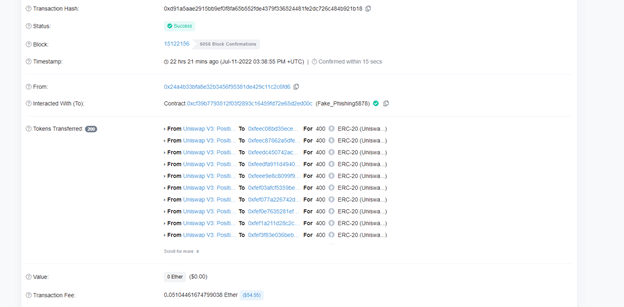
As illustrated, it seems like Uniswap V3 indeed sent the tokens. When the victim pressing on the token, it connects them to the phishing website which was UniswapLP.com (the website is currently down):
On the website, the victim saw could swap the LP token he received via the airdrop for UNI tokens:
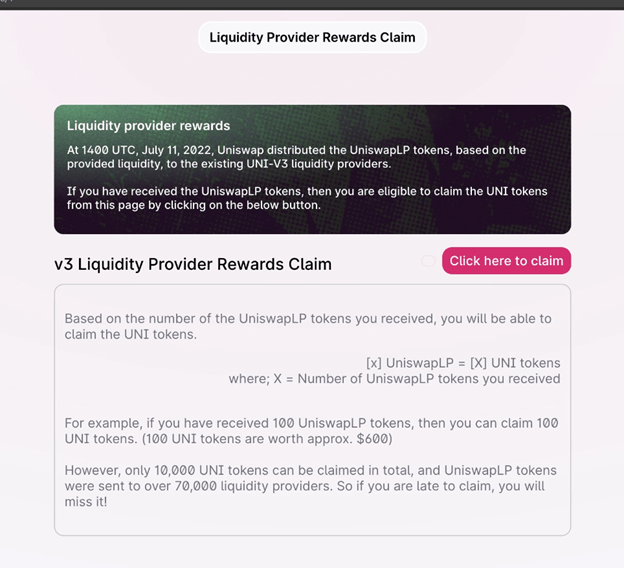
By pressing on the “Click here to claim” button, the victim granted the attacker full access to his account. This allows the attacker to access all the victim USDT:
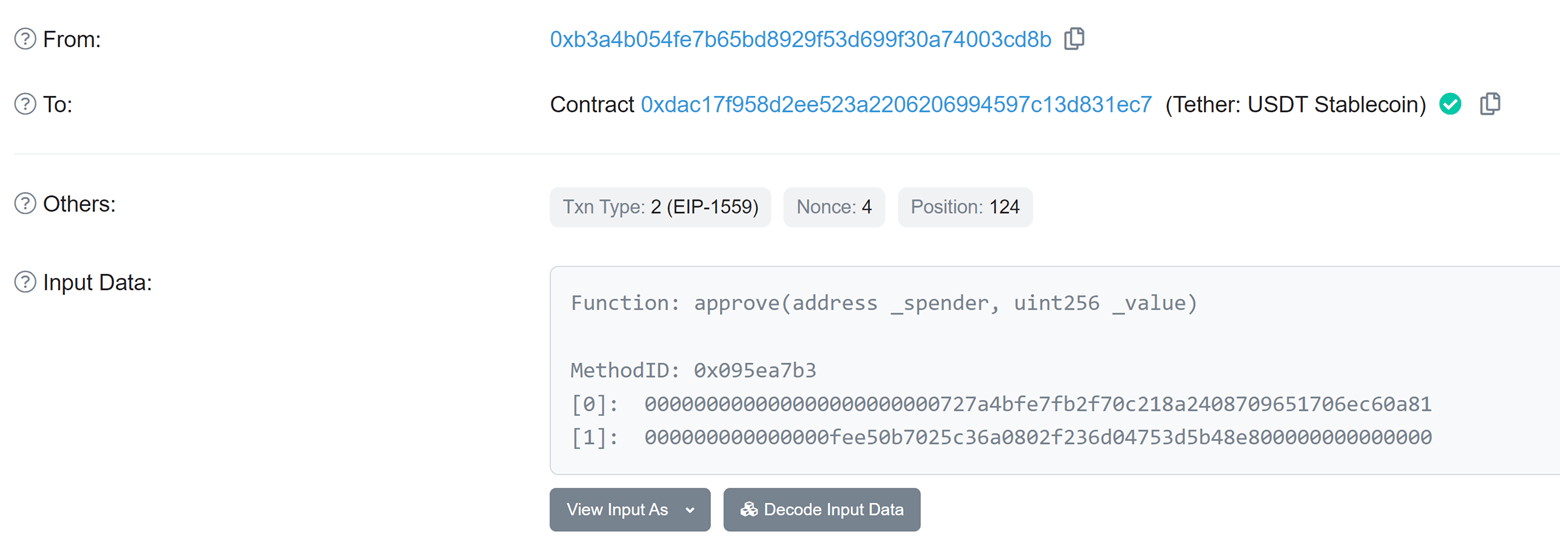
Followed by a transfer as seen below:
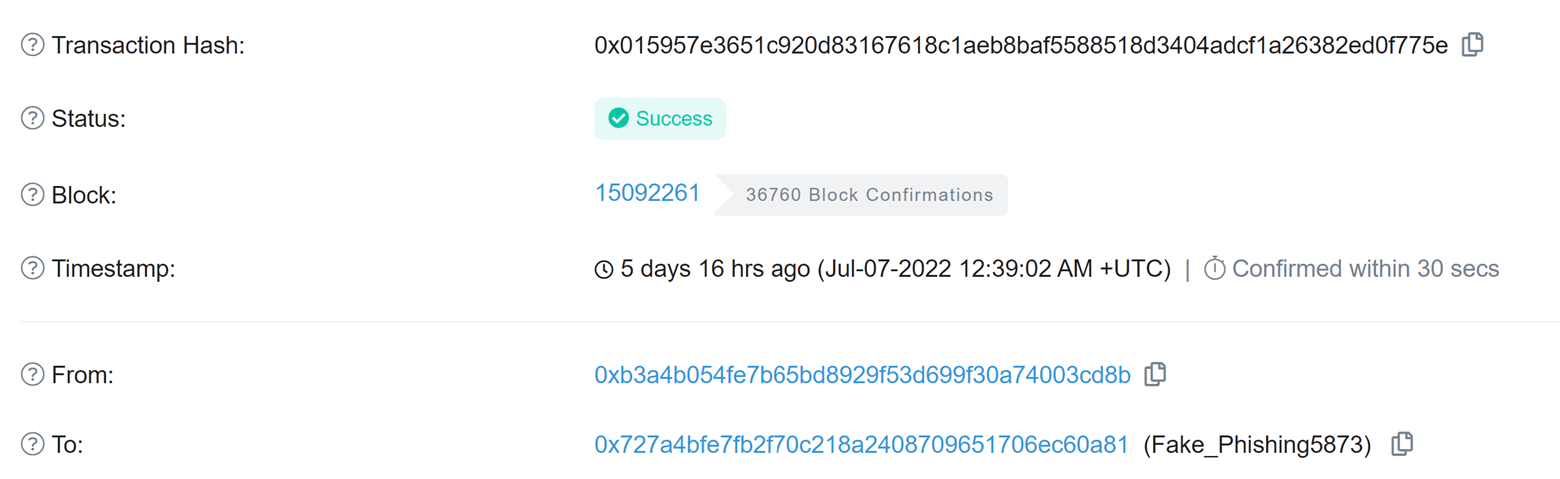
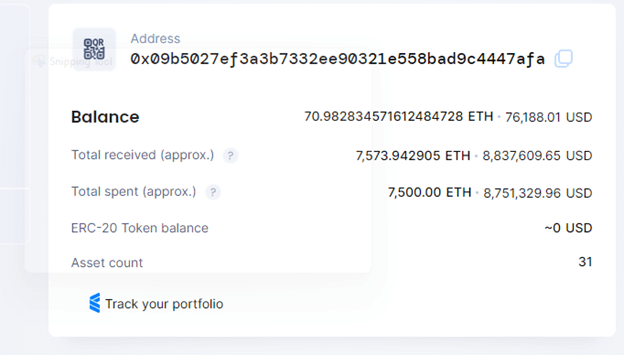
Through this new phishing scam, the attacker stole 8 million dollars’ worth of ETH, as can be seen in the
following screenshot:
Etherescan address spoofing technique
As previously mentioned, the attacker spoofed the sender to Uniswap. That happened because block explorers such as etherscan can take the data from the emit functionality of the contract, which is just a transaction log. These logs are stored on the blockchain and are accessible. But the emit function does not necessarily have to be the actual address. A code example of such behavior can be simulated as follows:
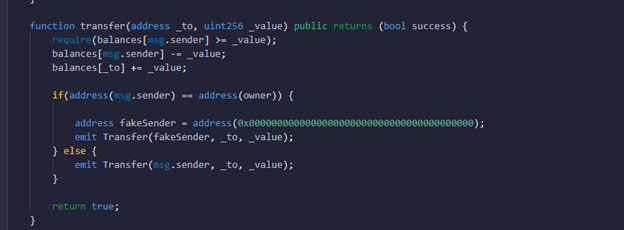
As you can see, we set the address that will be shown in the block explorer to ‘0x0000000000000000000000000000000000000000’
And the block explorer will think the transaction come from address ‘0x0000000000000000000000000000000000000000’:
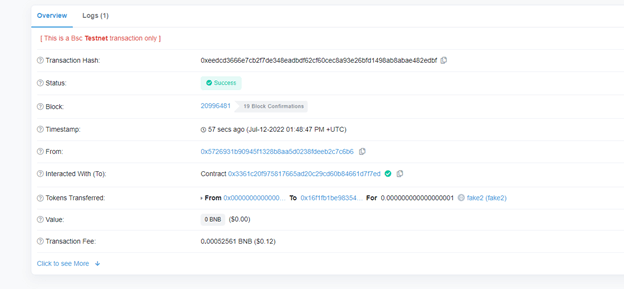 Proving it is possible to set the address to uniswap or anything else.
Proving it is possible to set the address to uniswap or anything else.
Tips for Crypto users:
We understand that it is very confusing for a novice crypto user and often they fall into such scams because they are not familiar with the applications they are using. However, they need to understand that even the major platforms like etherscan may have bugs. We suggest crypto users keep in mind some of the following important rules:
1. Always read the official twitter and website of the platform.
2. Look closely at the official source when someone sends an airdrop or anything else pretending to be
Uniswap or any other big platform.
3. When looking for wallets or crypto trading and swapping platforms, always look at the website of
the platform. If you cannot find the links in their platform it is a scam.
4. Finally – always double-check the URLs!









