Protecting IoT Devices from Within – Why IoT Devices Need A Different Security Approach?
By Gili Yankovitch, Technology Leader, IoT Embedded, Check Point
IoT cyberattacks are increasing by the day, and unfortunately are becoming more sophisticated, widespread, and destructive for any business. We’ve seen a large number of examples in which hundreds of thousands of connected devices were attacked by malware that spread over the entire network; Infecting PCs, servers, and internal assets with ransomware, crypto-miners, Trojan, botnets, and more.
In this article we will discuss the reasons why these vulnerabilities exist, how cybercriminals achieve access, and how you can implement some best practices to keep your organization from cyberattacks.
How do these attacks happen?
In the cybersecurity world, your cyber protection is only as strong as its weakest link. This is true for a single device as it is for an entire network.
When we talk about the weakest link in a network, we are talking about perimeter-network-facing devices that are accessible through the Internet. These include many different device types from IP cameras, routers, and sensors on a corporate campus on the low end, to field-deployed devices such as gas pumps, EV chargers, and ATMs on the high end. All of these devices are connected to the internet and meant to be accessed remotely.
The perimeter
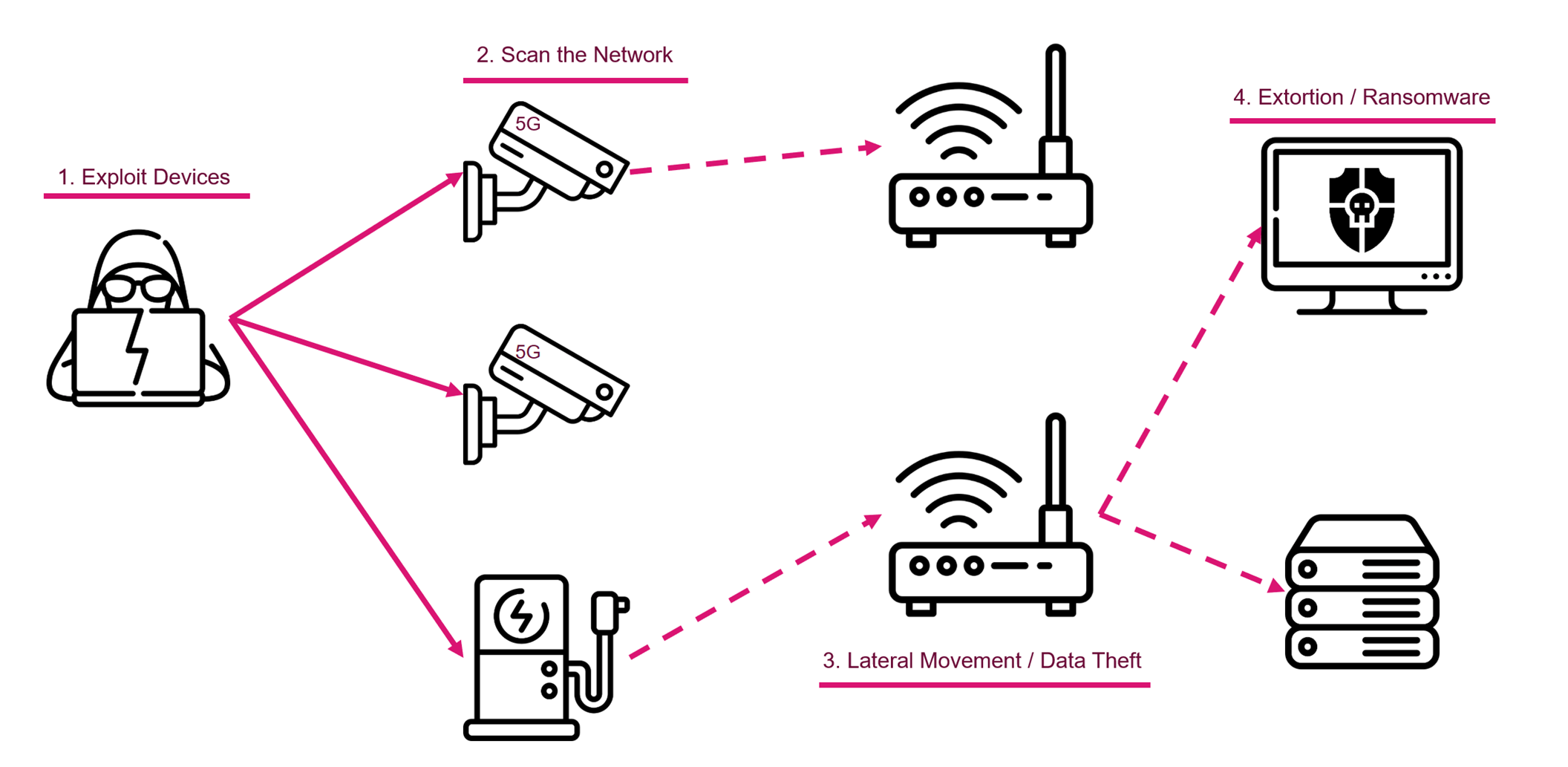
When attackers attempt to breach a network, they usually scan the network for these connected devices to potentially use as an entry points to the network.
IoT devices make a useful stepping stone to launch cyber attacks from, as they usually run outdated software or are not monitored for security events. Due to the high scale and large variety of these devices (for example, a single university campus can accommodate dozens of different devices), traditional incident-response measures might not be as effective as usual. When so many assets are breached within a network all at once, it is hard to keep tabs on where the vulnerabilities are coming from. It is also important to note that there is never just one single point of failure.
What happens next?
An attack campaign is not comparable to a hit-and-run scenario. Sometimes attackers hide in plain sight for a long time, waiting for the right moment to strike while conducting reconnaissance missions to familiarize themselves with their would-be victim’s network before going all-in.
When an attack occurs, one of the attacker’s goals is to gain lateral movement throughout the targeted network. They wish to move freely throughout the entire network, attacking other internal assets and entities. By exploiting servers, PCs, and common office machines, like printers and routers, the attackers improve their ability to gain a wider control over the network. A very common theme we see are attackers leveraging this control for various purposes such as data theft, extortion, ransomware infection, and more. What began as just a simple breach in a line of perimeter devices can quickly transform into a full-blown attack campaign with potentially devastating consequences.
How does an attack usually carry out?
Once a ransomware infection invades your network, it can attach itself to so many assets that it becomes nearly impossible to eliminate.
An infamous example of such a case, in which an IoT network of devices was hijacked to run a host of malicious software, cryptominers, and more, is presented in the R4IoT research paper published by Vedere Labs. The “attack” started with exploiting vulnerabilities found in Axis cameras (CVE-2018-10660, CVE-2018-10661) and a Zyxel NAS (CVE-2020-9054). Using these network footholds to spread laterally and exploit other internal network entities, the malware was able to gain hold over numerous network entities, steal information, and infect other devices with ransomware. In this case, the researchers were able to exploit (relatively) old vulnerabilities (from 2018 and 2020), just to demonstrate the effect of malware on devices with unpatched firmware. These vulnerabilities allow attackers to gain full access through an unauthenticated interface on the device.
Another example of an attack scenario (CVE-2022-29499)was discovered recently in Mitel IP phones. This vulnerability allowed attackers to run arbitrary commands on these devices, essentially providing attackers the ability to do whatever they pleased. Unlike the vulnerabilities highlighted within the R4IoT research paper, which can be addressed using traditional signature-based products, any attackers exploiting this Mitel vulnerability could continue their rampage virtually unimpeded.
We also cannot neglect to mention the ZuoRAT attack that happened very recently. This was an extremely widespread attack campaign that infected at least 80 types of various devices, as well as , Netgear, Asus, and DrayTek home routers. This Trojan malware, which allows remote access to the attackers, has been around for several years and continues to spread like wildfire. This is a critical risk in today’s world where many of us continue to work from home, leaving the potential infection of home devices to have a devastating impact on an organization’s assets and overall business.
It is becoming hard to believe how simple it is for these malware attacks to initiate. Often, attacks like those mentioned earlier can be purchased inexpensively through unregulated markets. A few weeks ago, the U.S. Department of Justice seized a website called RSOCKS. This was a Russian-based web service that sold proxies that attackers often used to carry out crypto-mining activities, DDOS attacks, and much more. Most of the attackers were able to gain control over network-connected devices and assets just by using their default credentials or guessing weak passwords. Unbelievably, this method of guessing credentials or attempting default usernames and passwords amassed a malicious network consisting of more than 350,000 consumer, office, and home devices.

Future-proofing
IoT device vendors are exceptional in their field for making sure their products work as intended. However, these same device manufacturers aren’t security experts by any means.
In today’s cyber landscape, it is critical that your organization network connected devices and assets are safe and secure for the next attack. It is impractical to implement patch after patch for every vulnerability and exploit seen in the wild. And even when software vendors release frequent updates to the devices, research shows that operators and end-users often do not maintain their devices and keep them up to date. What is needed in this case is a future-proof solution that can solve for these obstacles.
Check Point Quantum IoT Embedded introduces an innovative approach in IoT security with focus on detection and prevention; and not just detection like most of the solutions on the market today. The Check Point Nano-Agent® provides on-device runtime protection and runs on every IoT device, securing it in an online environment, as well as offline, or in an air-gapped network. The solution monitors the device’s software to ensure the device behavior matches what is expected. If a cyberattack were to attempt to exploit vulnerabilities, either known or unknown, our zero-day protection would detect any deviation and prevent the attack dead in its tracks.
The cybersecurity battle is one that will be waged for a long time, with ever increasing innovations on both sides. Basic monitoring and detection security solutions are not enough in today’s modern cyber landscape. We cannot hope to win without a cyber security solution that both detects AND prevents cyber-attacks in real time. To learn more about how Check Point can help protect your devices, we strongly recommend Signing Up for A Demo or talking with a cyber security expert from our team.