
November Shopping Schemes: Check Point Research Unveiling Cybercriminal Tactics as Luxury Brands Become Pawns in Email Scams
Highlights:
- Delivery service and shipping sectors are the focus of cybercriminals during this shopping period.
- October 2023 saw a 13% increase in the number of malicious files related to orders and delivery/shipping compared to October 2022.
- Check Point Research Exposes the Exploitation of Luxury Brands to Deceptively Lure Clicks on Malicious Links—A Wake-Up Call for Shoppers to Stay Vigilant Online.
Protecting your November Shopping Experience
As the holiday season kicks into gear, the online shopping landscape becomes a bustling hub of activity. However, amid the excitement of finding the perfect deals, there’s a lurking danger that shoppers need to be aware of—cybercrimes targeting unsuspecting victims. In this blog, we delve into the alarming tactics uncovered by Check Point Research (CPR), where luxury brands are exploited as bait to lead users into clicking on malicious links. Join us on a journey through the virtual marketplace as we unravel the schemes and offer essential insights to help you shop securely in November and beyond.
A luxurious click that might cost even more than you realize.
As the November shopping frenzy approaches, Check Point Research has unearthed a concerning email pattern employed by hackers. This deceptive tactic involves the spoofing of renowned brands, such as Louis Vuitton, Rolex, and Ray-Ban. The hackers craft enticing emails promising steep discounts on these luxury products, with the email addresses cleverly manipulated to mimic the authenticity of the brands. Despite the appearance of legitimacy, a closer look reveals that the email origins have no connection to the actual luxury companies.
Upon clicking the tempting links within these emails, unsuspecting victims are led to websites meticulously designed to replicate the official sites of the targeted brands. These fraudulent sites then peddle luxury goods at unbelievably discounted prices, creating an alluring trap for potential shoppers. However, the real danger lies in the malicious intent behind these sites, as they prompt users to input their account details. This sensitive information becomes vulnerable to theft by the attackers, highlighting the urgent need for heightened awareness and caution as we navigate the enticing realm of November shopping.
| Rolex | Ray Ban | Louis Vuitton | |
| Subject | [Black Friday Special Offer] Rolex Watches Start at $250 Today! Shop Online Now! | Ray Ban Sunglasses 90% Off. 2023 Style. Free Shipping All Order! Shop Online Now! | [Black Friday] Louis Vuitton Bags Up To 90% Off! Top Quality Low Cost! Shop Online Now!
|
| From | Rolex Watches (hxdvd@a[.]mtcyfizfdu[.]ru) | Ray Ban (tts@a[.]ljacmbpjo[.]ru) | Louis Vuitton (fzcypmsta@a[.]htaegewg[.]ru) |
| Link | www[.]hotwatch[.]su | https://www[.]85offrb[.]su | www[.]85off-lvbags[.]com |
| Screenshot of the mail |  |
 |
 |
| Screenshot of the link | 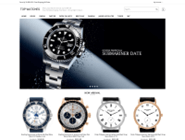 |
inactive | 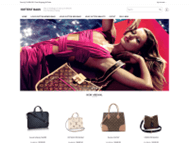 |
Delivery and Shipping sectors:
Check Point Researchers have noticed how cybercriminals are using the delivery and shipping sectors during this traditional shopping period. In October 2023, their findings revealed a staggering 13% increase in the number of malicious files associated with orders and delivery/shipping compared to October 2022. The escalating threat in these sectors underscores the evolving tactics of cyber adversaries, urging heightened vigilance and proactive cybersecurity measures.
As mentioned in October 2023’s most wanted malware, CPR found a campaign of AgentTesla with Archive files delivered as attachments to emails using subjects related to orders and shipments, such as – po-######.gz / shipping documents.gz, luring the victim to download the malicious file.
Below is another example of a campaign of emails impersonating delivery company DHL.
The emails were sent from a webmail address “DHL Express ([email protected])” and spoofed to appear as if they had been sent from “DHL” (see figure 1) and contained the subject “DHL Delivery Invoice #############”. The content asked to download a malicious executable file “Invoice #############”.pdf.exe”, that would drop other malicious files using powershell.
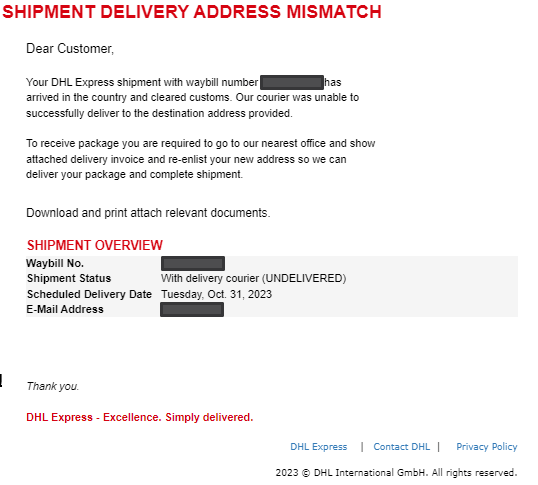
The malicious email which contained the subject “DHL Delivery Invoice #############”
Phishing websites:
CPR also found examples of phishing websites, which have similar registered information and look similar to each other – offering well-known shoe brands at ridiculous prices.
www[.]reebokblackfridayoffers[.]com
www[.]oncloudblackfridaysale[.]com
www[.]hokablackfridaysale[.]com
www[.]salomonblackfridaysales[.]com
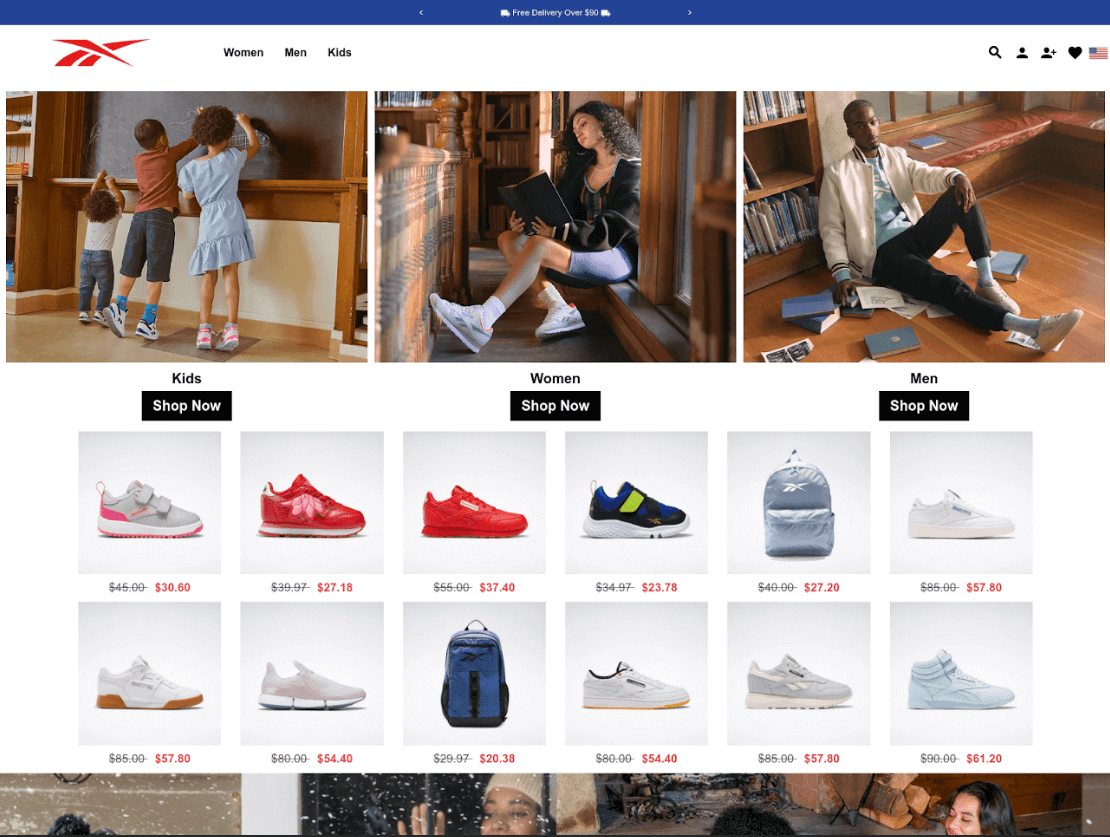
Figure 1: reebokblackfridayoffers[.]com
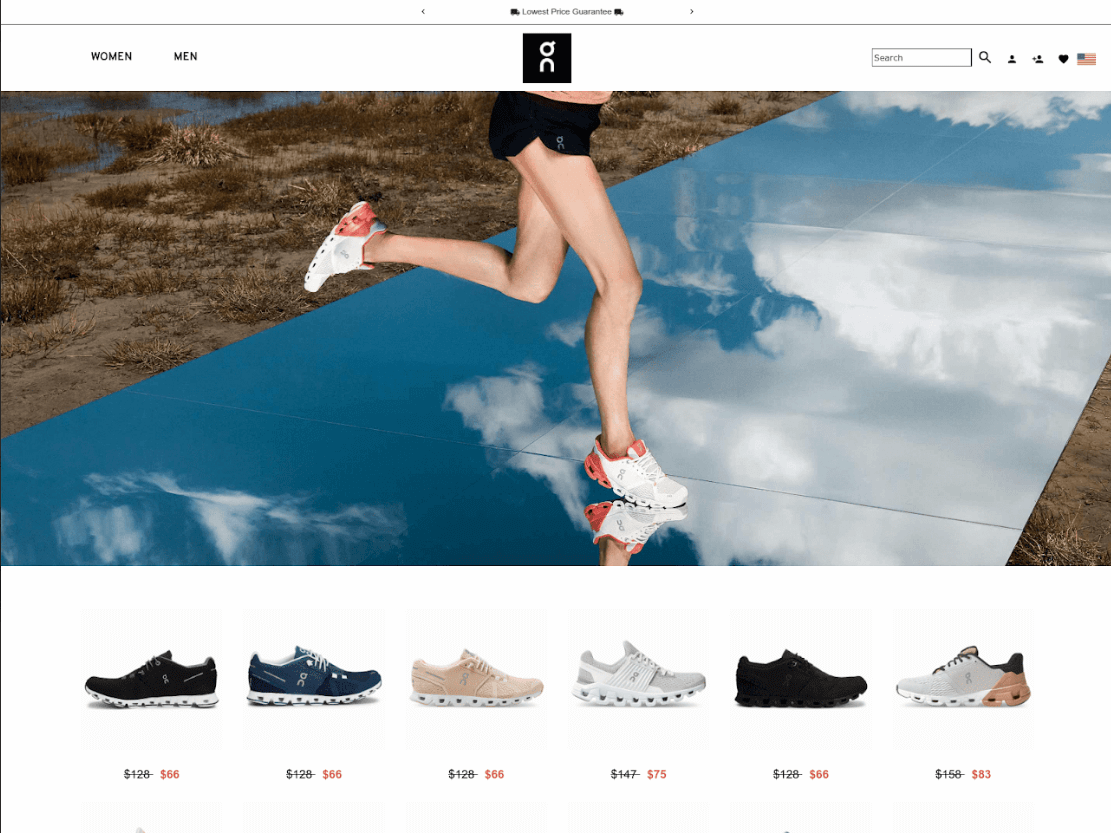
Figure 2: oncloudblackfridaysale[.]com
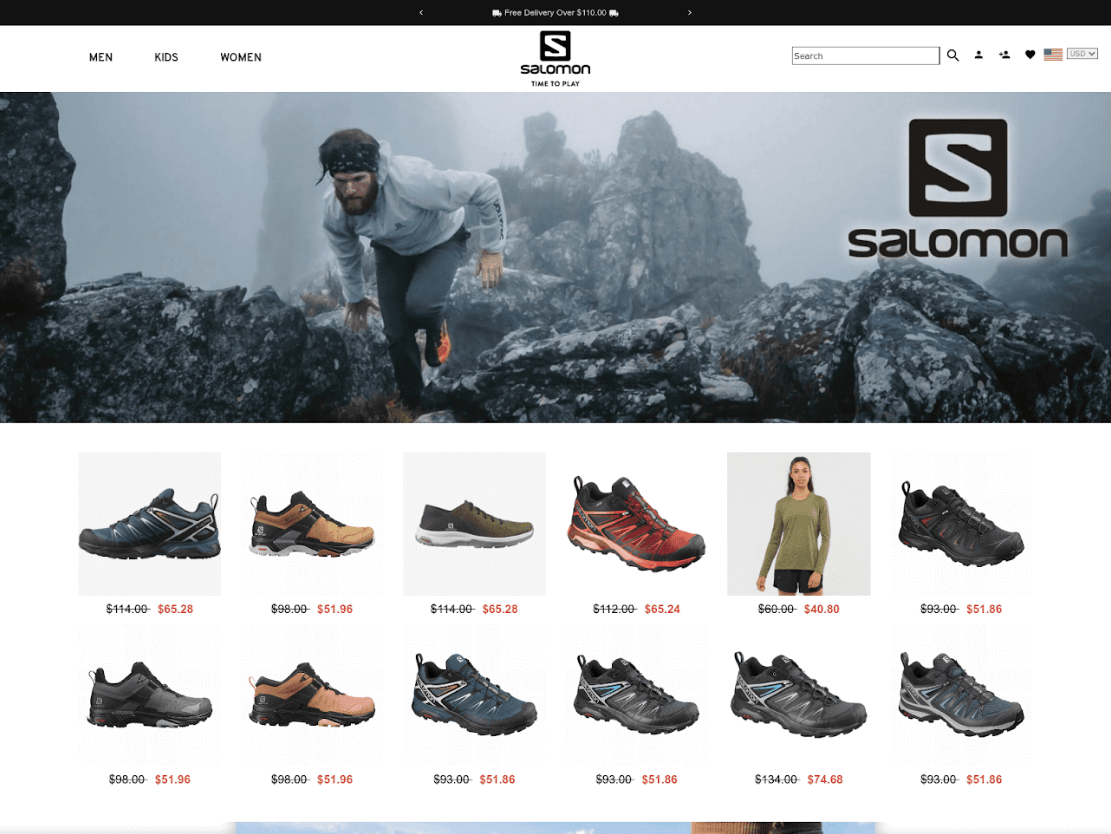
Figure 3: salomonblackfridaysales[.]com
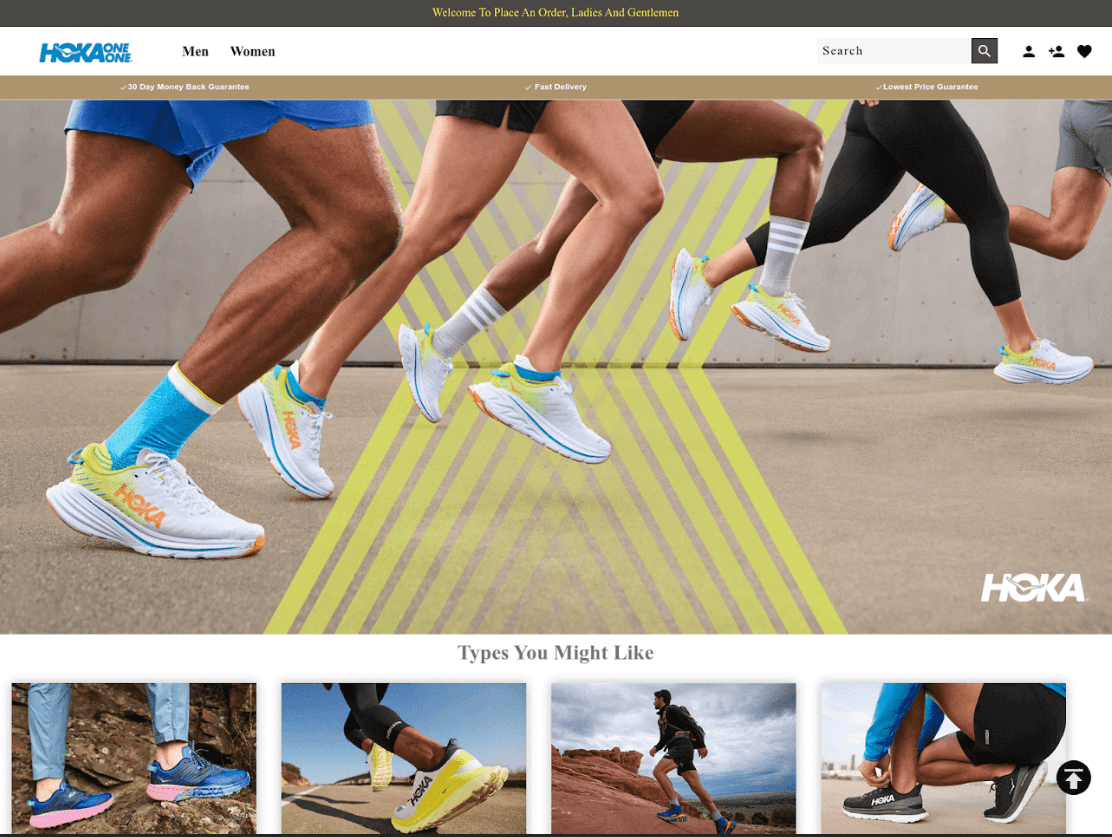
Figure 4: hokablackfridaysale[.]com
How To Identify URL Phishing
URL phishing attacks use trickery to convince the target that they are legitimate. Some of the ways to detect a URL phishing attack is to:
- Ignore Display Names: Phishing emails can be configured to show anything in the display name. Instead of looking at the display name, check the sender’s email address to verify that it comes from a trusted source.
- Verify the Domain: Phishers will commonly use domains with minor misspellings or that seem plausible. For example, company.com may be replaced with cormpany.com or an email may be from company-service.com. Look for these misspellings, they are a good indicator.
- Check the Links: URL phishing attacks are designed to trick recipients into clicking on a malicious link. Hover over the links within an email and see if they actually go where they claim. Enter suspicious links into a phishing verification tool like phishtank.com, which will tell you if they are known phishing links. If possible, don’t click on a link at all; visit the company’s site directly and navigate to the indicated page.
URL Phishing Protection With Check Point
Check Point developed an anti-phishing solution that provides improved URL phishing protection compared to common techniques. This includes post-delivery protection, endpoint protection to defend against zero-day threats, and the use of contextual and business data to identify sophisticated phishing emails.
Expanding our zero-phishing offering, we’ve also introduced our innovative AI-powered engine to prevent local and global brand impersonation employed in phishing attacks, Collaboratory protecting across networks, emails, mobile devices, and endpoints.







