Following Pope Francis’ death, as is common with global events of this nature, cyber criminals have launched a variety of malicious campaigns. This tactic isn’t new—cyber attackers have long exploited major world events, from the passing of Queen Elizabeth II to natural disasters and global crises like COVID-19, to drive scams, disinformation, and malware infections. Public curiosity and emotional reactions make these moments prime opportunities for attackers to strike.
They typically begin with disinformation campaigns on social media platforms like Instagram, TikTok, or Facebook, uploading fake images generated by AI. These campaigns are designed to capture user attention, prompting them to search for more information via search engines or click on links embedded within the images or posts. Once engaged, users may be redirected to fraudulent websites that serve various malicious purposes, from data theft to financial scams.
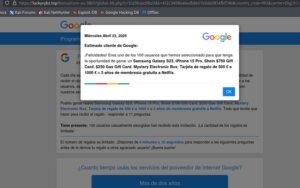
In the example observed, the link was hidden in a website promoting potential fake news about Pope Francis. Once a user clicked on one of the links, it redirected them to a fake Google page promoting a gift card scam—a common tactic used to trick individuals into handing over sensitive information or making payments.
On other fraudulent websites, background commands are launched and executed without user interaction. This form of malware collects information such as the machine name, operating system, country, language, and more. The purpose is to gather detailed data on users to later launch highly targeted phishing campaigns or to sell this information on the Dark Web. Such data could include login credentials, financial details, or technical device specs.
Another significant threat tied to these types of events is SEO poisoning (search engine optimization poisoning). Here, cyber criminals pay to position their malicious sites among legitimate search results, deceiving users into thinking they’re accessing trustworthy information. This method helps distribute malware, steal credentials, or hijack session cookies—ultimately monetizing the traffic generated through such sites. For instance, someone searching for updates on Pope Francis might unknowingly click on a malicious link ranked high in search results.
This problem is exacerbated by the fact that many of these domains do not appear in reputation intelligence tools. The domains may have been recently registered or held dormant for months without showing any malicious behavior, allowing them to bypass detection by most cyber security systems. Attackers are adept at using clean domains with no historical ties to malicious activity, making their campaigns harder to flag.
Broader Trend & Expert Insights
This approach fits a broader pattern known as “cyber threat opportunism”, where attackers exploit high-interest global events to spread malware or misinformation. Research from organizations like Check Point Research consistently highlights spikes in phishing and malware campaigns tied to such events. During the COVID-19 pandemic, for example, Google reported over 18 million daily malware and phishing emails related to coronavirus scams.
Cyber criminals thrive on chaos and curiosity. Whenever a major news event occurs, we see a sharp rise in scams designed to exploit public interest. The best defense is a combination of user awareness and layered security protection.
How to Stay Safe – Security Tips:
- Keep your browser and operating system updated to the latest versions. Security patches often fix vulnerabilities that attackers exploit.
- Use browsing protection tools like Check Point Harmony Browse or other web security extensions that verify websites in real-time, blocking malicious links before they load.
- Be cautious with sensational headlines or viral content, especially on social media. If the news seems shocking, cross-check it through reputable media outlets.
- Don’t click on links from unfamiliar sources, especially in emails or social posts related to breaking news. Instead, type official news website URLs directly into your browser.
- Use threat intelligence services like VirusTotal or Check Point ThreatCloud to verify suspicious domains or files before engaging with them.
- Consider advanced security software that includes phishing protection, malware detection, and threat intelligence updates to keep your devices secure.
By following these steps, users can significantly reduce their risk of falling victim to disinformation campaigns or cyber attacks that capitalize on global events.

Video screenshot from TikTok mentioning that the death is a hoax. Currently circulating

Image extracted from thousands of Instagram posts, generated with AI, containing various links to fraudulent websites.

Fake image generated by AI, initially distributed in February 2025, now resurfacing on different websites and social media posts linking to supposed news sites.




