
Hexstrike-AI: When LLMs Meet Zero-Day Exploitation
Key Findings:
- Newly released framework called Hexstrike-AI provides threat actors with an orchestration “brain” that can direct more than 150 specialized AI agents to autonomously scan, exploit, and persist inside targets.
- Within hours of its release, dark web chatter shows threat actors attempting to use HexStrike-AI to go after a recent zero day CVEs, with attackers dropping webshells for unauthenticated remote code execution.
- These vulnerabilities are complex and require advanced skills to exploit. With Hextrike-AI, threat actors claim to reduce the exploitation time from days to under 10 minutes.
From Concept to Reality
A recent executive insight blog examined the idea of a “brain” behind next-generation cyber attacks: an orchestration and abstraction layer coordinating large numbers of specialized AI agents to launch complex operations at scale. That architecture was already beginning to appear in offensive campaigns, signaling a shift in how threat actors organize and execute attacks.
The emergence of Hexstrike-AI now provides the clearest embodiment of that model to date. This tool was designed to be a defender-oriented framework: “a revolutionary AI-powered offensive security framework that combines professional security tools with autonomous AI agents to deliver comprehensive security testing capabilities”, their website reads. In this context, Hexstrike-AI was positioned as a next-generation tool for red teams and security researchers.
But almost immediately after release, malicious actors began discussing how to weaponize it. Within hours, certain underground channels discussed application of the framework to exploit the Citrix NetScaler ADC and Gateway zero-day vulnerabilities disclosed last Tuesday (08/26).
This marks a pivotal moment: a tool designed to strengthen defenses has been claimed to be rapidly repurposed into an engine for exploitation, crystallizing earlier concepts into a widely available platform driving real-world attacks.
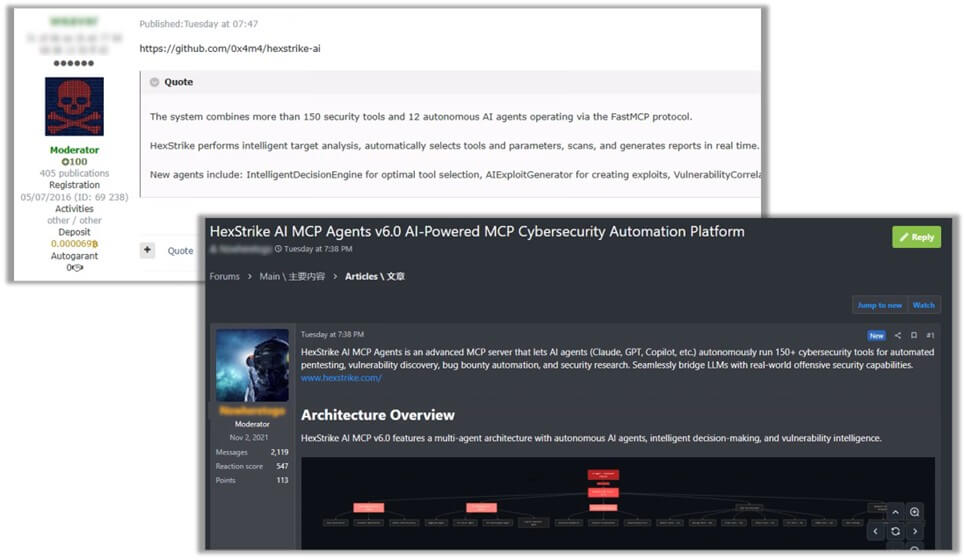
Figure 1: Dark web posts discussing HexStrike AI, shortly after its release.
The Architecture of Hexstrike-AI
Hexstrike-AI is not “just another red-team framework.” It represents a fundamental shift in how offensive cyber operations can be conducted. At its heart is an abstraction and orchestration layer that allows AI models like Claude, GPT, and Copilot to autonomously run security tooling without human micromanagement.
Figure 2: HexStrike AI MCP Toolkit.
More specifically, Hexstrike AI introduces MCP Agents, an advanced server that bridges large language models with real-world offensive capabilities. Through this integration, AI agents can autonomously run 150+ cyber security tools spanning penetration testing, vulnerability discovery, bug bounty automation, and security research.
Think of it as the conductor of an orchestra:
- The AI orchestration brain interprets operator intent.
- The agents (150+ tools) perform specific actions; scanning, exploiting, deploying persistence, exfiltrating data.
- The abstraction layer translates vague commands like “exploit NetScaler” into precise, sequenced technical steps that align with the targeted environment.
This mirrors exactly the concept described in our recent blog: an orchestration brain that removes friction, decides which tools to deploy, and adapts dynamically in real time. We analyzed the source code and architecture of Hexstrike-AI and revealed several important aspects of its design:
- MCP Orchestration Layer
The framework sets up a FastMCP server that acts as the communication hub between large language models (Claude, GPT, Copilot) and tool functions. Tools are wrapped with MCP decorators, exposing them as callable components that AI agents can invoke. This is the orchestration core; it binds the AI agent to the underlying security tools, so commands can be issued programmatically. - Tool Integration at Scale
Hexstrike-AI incorporates core network discovery and exploitation tools, beginning with Nmap scanning and extending to dozens of other reconnaissance, exploitation, and persistence modules. Each tool is abstracted into a standardized function, making orchestration seamless.
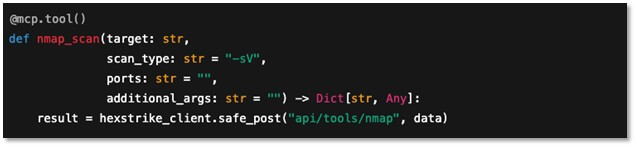
Figure 3: the nmap_scan tool is exposed as an MCP function.
Figure 3: the nmap_scan tool is exposed as an MCP function.
Here, AI agents can call nmap_scan with simple parameters. The abstraction removes the need for an operator to run and parse Nmap manually — orchestration handles execution and results.
- Automation and Resilience
The client includes retry logic and recovery handling to keep operations stable, even under failure conditions. This ensures operations continue reliably, a critical feature when chaining scans, exploits, and persistence attempts.
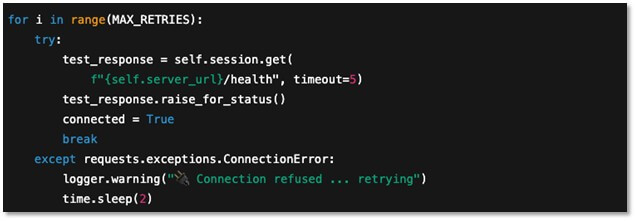
Figure 4: Hexstrike-AI’s automated resilience loop
- Intent-to-Execution Translation
High-level commands are abstracted into workflows. The execute_command function demonstrates this. Here, an AI agent provides only a command string, and Hexstrike-AI determines how to execute it, turning intent into precise, repeatable tool actions.
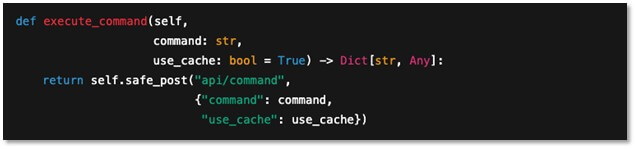
Figure 5: Hexstrike-AI’s execute_command function.
Why This Matters Right Now
The release of Hexstrike-AI would be concerning in any context, because its design makes it extremely attractive to attackers. But its impact is amplified by timing.
Last Tuesday (08/26), Citrix disclosed three zero-day vulnerabilities affecting NetScaler ADC and NetScaler Gateway appliances, as follows:
- CVE-2025-7775 – Unauthenticated remote code execution. Already exploited in the wild, with webshells observed on compromised appliances.
- CVE-2025-7776 – A memory-handling flaw impacting NetScaler’s core processes. Exploitation not yet confirmed, but high-risk.
- CVE-2025-8424 – An access control weakness on management interfaces. Also unconfirmed in the wild but exposes critical control paths.
Exploiting these vulnerabilities is non-trivial. Attackers must understand memory operations, authentication bypasses, and the peculiarities of NetScaler’s architecture. Such work has historically required highly skilled operators and weeks of development.
With Hexstrike-AI, that barrier seems to have collapsed. In underground forums over the 12 hours following the disclosure of the said vulnerabilities, we have observed threat actors discussing the use of Hexstrike-AI to scan for and exploit vulnerable NetScaler instances. Instead of painstaking manual development, AI can now automate reconnaissance, assist with exploit crafting, and facilitate payload delivery for these critical vulnerabilities.
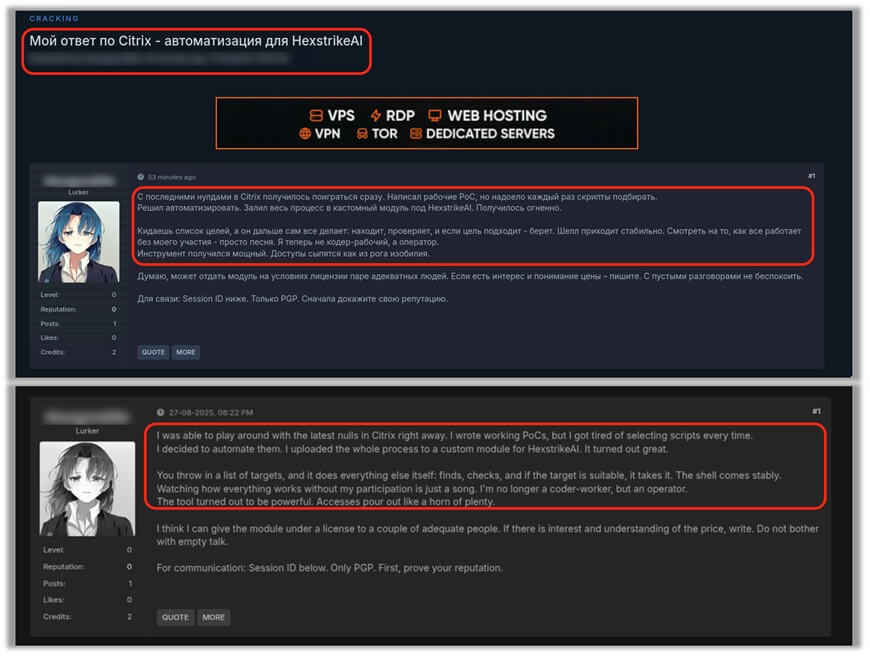
Figure 6: Top Panel: Dark web post claiming to have successfully exploited the latest Citrix CVE’s using HexStrike AI, originally in Russian;
Bottom Panel: Dark web post translated into English using Google Translate add-on.
Certain threat actors have also published vulnerable instances they have been able to scan using the tool, which are now being offered for sale. The implications are profound:
- A task that might take a human operator days or weeks can now be initiated in under 10 minutes.
- Exploitation can be parallelized at scale, with agents scanning thousands of IPs simultaneously.
- Decision-making becomes adaptive; failed exploit attempts can be automatically retried with variations until successful, increasing the overall exploitation yield.
- The window between disclosure and mass exploitation shrinks dramatically. CVE-2025-7775 is already being exploited in the wild, and with Hexstrike-AI, the volume of attacks will only increase in the coming days.
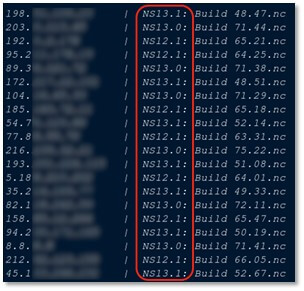
Figure 7: Seemingly vulnerable NetScaler instances curated by HexStrike AI.
Action Items for Defenders
The immediate priority is clear: patch and harden affected systems. Citrix has already released fixed builds, and defenders must act without delay. In our technical vulnerability report, we have listed technical measures and actions defenders should take against these CVEs, mostly including hardening authentications, restricting access and threat hunting for the affected webshells.
However, Hexstrike-AI represents a broader paradigm shift, where AI orchestration will increasingly be used to weaponize vulnerabilities quickly and at scale. To defend against this new class of threat, organizations must evolve their defenses accordingly:
- Adopt adaptive detection: Static signatures and rules will not suffice. Detection systems must ingest fresh intelligence, learn from ongoing attacks, and adapt dynamically.
- Integrate AI-driven defense: Just as attackers are building orchestration layers, defenders must deploy AI systems capable of correlating telemetry, detecting anomalies, and responding autonomously at machine speed.
- Shorten patch cycles: When the time-to-exploit is measured in hours, patching cannot be a weeks-long process. Automated patch validation and deployment pipelines are essential.
- Threat intelligence fusion: Monitoring dark web discussions and underground chatter is now a critical defensive input. Early signals, such as the chatter around Hexstrike-AI and NetScaler CVEs, provide vital lead time for professionals.
- Resilience engineering: Assume compromise. Architect systems with segmentation, least privilege, and robust recovery capabilities so that successful exploitation does not equate to catastrophic impact.
Conclusion
Hexstrike-AI is a watershed moment. What was once a conceptual architecture – a central orchestration brain directing AI agents – has now been embodied in a working tool. And it is already being applied against active zero days.
For defenders, we can only reinforce what has already been said in our last post: urgency in addressing today’s vulnerabilities, and foresight in preparing for a future where AI-driven orchestration is the norm. The sooner the security community adapts, patching faster, detecting smarter, and responding at machine speed, the greater our ability to keep pace in this new era of cyber conflict.
The security community has been warning about the convergence of AI orchestration and offensive tooling, and Hexstrike-AI proves those warnings weren’t theoretical. What seemed like an emerging possibility is now an operational reality, and attackers are wasting no time putting it to use.



