
Playing Offside: How Threat Actors Are Warming Up for FIFA 2026
Introduction
Every four years, the World Cup captures the attention of billions. With that attention comes opportunity – not only for sponsors, broadcasters, and legitimate merchants, but also for adversaries who see in this spectacle a marketplace of deception.
As the 2026 FIFA World Cup approaches, the outlines of this parallel economy are already visible. In the span of two months since 1 August 2025, more than 4,300 newly registered domains bearing the language of FIFA, the World Cup, or its host cities have surfaced across the internet. On the surface, many of these domains appear innocuous. Yet, when examined collectively, they reveal something far more deliberate. They arrive in synchronized bursts rather than at random, they cluster around a handful of retail registrars instead of dispersing widely, and they echo each other in naming conventions and DNS infrastructure as if generated from a shared script.
These domains represent fragments of infrastructure laid down in anticipation of a harvest to come. Some are poised to advertise counterfeit tickets that will never materialize, others promise streams that will collapse into malware, and still others offer merchandise destined to be counterfeit. More troubling is the evidence of systemic attacks – botnets positioned to overwhelm ticket queues, pricing models manipulated by artificial demand, and underground markets supplying tools and methods. What is being observed at this stage is not the fraud itself, but its infrastructure being assembled quietly in the shadows of the tournament.
Findings
Domain Registration Dynamics
One of the clearest signals of coordination is temporal. The dataset revealed that nearly 1500 domains were registered in the short window between 8 and 12 August 2025, with another peak observed in early September. This pattern is incompatible with organic fan activity and instead suggests automated bulk procurement. The tactic of domain aging was also evident. Several domains have been registered not only for 2026 but also for future World Cups such as 2030 and 2034. These registrations, left dormant for years, are intended to accrue passive legitimacy before activation, a common strategy in brand-targeted fraud campaigns.
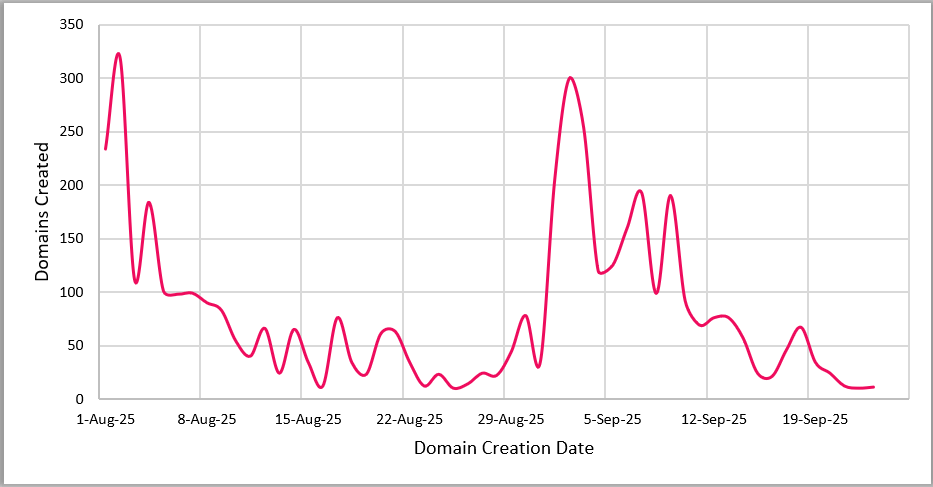
Figure 1: Monthly suspicious domain registrations (Aug–Sep 2025).
Registrar and TLD Concentration
Fraudulent registrations are not spread evenly across the registrar ecosystem. The majority of domains were concentrated at a handful of retail registrars, mainly GoDaddy, Namecheap, Gname, Dynadot, and Porkbun. These providers are favored because of their scale, pricing promotions, and ease of bulk automation. The top-level domain distribution tells a similar story. .com dominates, accounting for more than half of the sample, while a long tail of low-barrier TLDs such as .online, .shop, .store, and .football provide inexpensive alternatives for attackers looking to scale.
Geographic and Linguistic Targeting
Geographic cues indicate deliberate targeting of both global audiences and local markets. Domains referencing host nations (USA, Mexico, Canada) and host cities (Dallas, Miami, Toronto, Vancouver, Mexico City) were prominent, designed to boost SEO relevance and appear credible to travelers. Linguistic segmentation further illustrates this tailoring: English dominates streaming scams intended for worldwide reach, Spanish and Portuguese are heavily used in ticketing and merchandise fraud targeting Latin American fans, and French appears in smaller clusters likely aimed at European supporters.
Thematic Lures
The domains align with three primary lures: counterfeit tickets, illicit streaming, and fake merchandise. Some clusters were devoted to a single theme, such as fifa2026ticketsmiami.com, while others combined multiple hooks into a single domain, for example fifa2026tickets-streamlive.com. The latter suggests the use of template-driven generation kits, where operators can vary themes while maintaining a consistent structure. Streaming terms (“HD,” “watch live,” “gratis”) were common, while ticket-related domains were less frequent but more financially damaging, given the high-value loss per victim. Merchandise domains marketed jerseys, kits, and apparel in multiple languages, particularly Spanish and Portuguese.

Figure 2: Examples of fraudulent FIFA 2026–themed websites used as lures.
Infrastructure Overlap
The analysis of DNS records uncovered repeated use of identical nameservers across clusters of domains, suggesting not dozens of independent actors but a small number of semi-professional operators managing large portfolios. This overlap, combined with synchronized registrations and similar lexical patterns, supports the hypothesis of campaign-based activity.
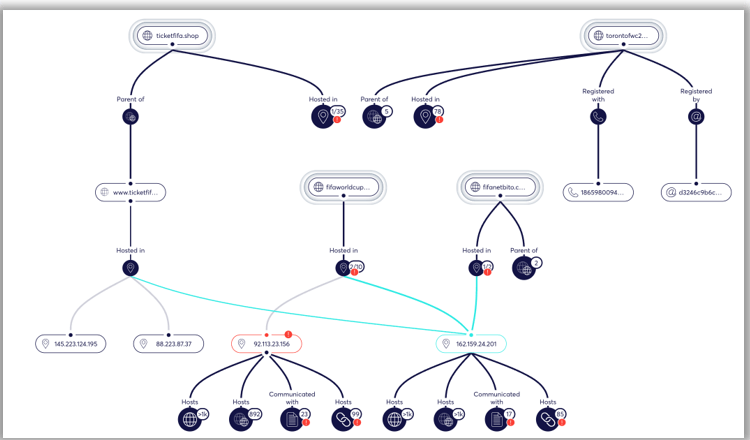
Figure 3: Several impersonating domains analyzed using ERM’s Forensic Canvas tool, indicating that many domains are hosted on clusters of IP addresses.
Multi-Platform Campaigns
Domains alone are insufficient to explain the risk. Their real power emerges when amplified across platforms. Telegram channels have already been observed advertising “exclusive tickets” and counterfeit jerseys. Dark-web forums continue to host threads offering both fraudulent tickets and the toolkits to conduct phishing or payment fraud under the FIFA trademark. Social media pages, often masquerading as “official” outlets, are expected to drive traffic toward these domains, while malicious ads in search results have the potential to out-rank FIFA’s own websites. What emerges is not a set of standalone scams but an ecosystem of fraud distribution, stretching from domain registrations to underground marketplaces to mainstream social channels.
Ticketing Abuse and Advanced Tactics
Perhaps most concerning are the systemic threats to FIFA’s ticketing infrastructure itself. Evidence suggests that botnets are already being prepared to flood ticket queues, acquire inventory at scale, and resell at inflated prices. These bot-driven demand surges also interfere with dynamic pricing algorithms, causing legitimate fans to face higher prices. Parallel to this, dark-web vendors are openly selling bot kits, proxy farms, and account bypass playbooks tailored to FIFA’s systems. The FTC’s September 2025 lawsuit against Live Nation/Ticketmaster illustrates how scalper automation has already destabilized major ticketing platforms and highlights the vulnerability of high-demand events like the World Cup to similar abuse.
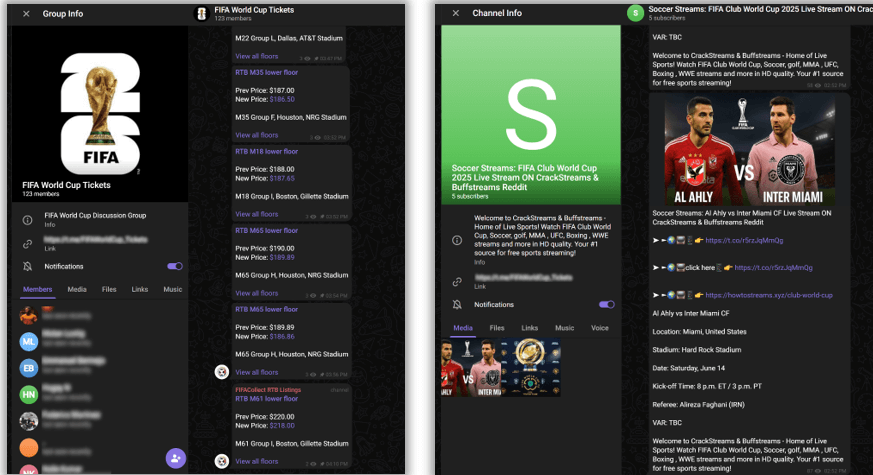
Figure 4: Telegram channels offering for sale fraudulent FIFA 26’ tickets (right), or fraudulent streaming services (left).
Risk Landscape
The implications of these findings extend across multiple stakeholders. Fans are exposed to high-value fraud in the form of counterfeit tickets, credential phishing during presales, and malware-laced streams. FIFA and its sponsors face brand dilution, counterfeit commerce leakage, and reputational damage that could undermine official channels. Host cities and venues are drawn into the threat landscape as geo-anchored scams target travelers with fraudulent offers tied to accommodation, transport, and hospitality. Finally, the broader internet ecosystem – registrars, ad networks, messaging platforms – risks being exploited as amplifiers for campaign distribution.
Recommendations
The evidence points to a pre-activation fraud ecosystem that is already functional and awaiting the moment of exploitation. Mitigation must therefore begin now rather than in 2026. Continuous monitoring of FIFA + year + city combinations in multiple languages should be prioritized, with registrar partnerships enabling rapid takedowns of synchronized domain bursts. Registrars most frequently exploited, such as GoDaddy and Namecheap, must be pressed to enforce stricter verification and abuse-response processes. Cross-channel intelligence gathering across Telegram, dark-web forums, and advertising platforms is equally essential to detect distribution nodes.
Ticketing systems require immediate reinforcement against automation. Behavioral detection and anti-bot measures should be embedded at presale and lottery phases, ensuring that surges are treated as adversarial signals rather than legitimate demand. FIFA and its partners should also engage in proactive search and advertising hygiene, seeding verified domains and ads well ahead of presales to out-compete fraudulent listings.
Finally, fans themselves must be armed with awareness, as the human factor is often the most vulnerable link. Practical steps include:
- Only buy tickets from official sources: FIFA will publish authorized sales channels. When in doubt, verify directly on FIFA’s official site.
- Be cautious with links: Fake “Fan ID” emails or “schedule updates” are common phishing tricks. Avoid clicking on suspicious links or attachments.
- Check the domain name carefully: Fraudulent sites often use subtle misspellings (e.g., com). Always scrutinize the URL.
- Avoid deals that seem too good to be true: Promises of guaranteed tickets, early access, or steep discounts are almost always red flags.
- Use security tools: Keep browsers, antivirus, and security software updated to block malicious domains, phishing attempts, and fraudulent ads.
By combining systemic interventions with user awareness, the ecosystem of fraud can be disrupted before it matures.
Conclusion
The World Cup of 2026 has not yet begun, but its counterfeit shadow is already taking shape. In the digital margins of the tournament, a parallel economy is being constructed: domains registered in synchronized waves, anchored by shared infrastructure, and awaiting amplification through Telegram channels, dark-web markets, social media campaigns, and paid advertising.
Fraud in this context is not spontaneous opportunism, it is designed and engineered with the same precision and scale as the legitimate tournament itself. For FIFA, sponsors, and host cities, the challenge is to secure the digital perimeter before the world arrives. For fans, the responsibility is to tread carefully, to recognize that the glittering promise of a cheap ticket or a free stream may hide a trap. The 2026 tournament should be remembered for its goals and spectacle – not as the event where millions found themselves locked out by scams they never saw coming.



