Over 39,000 new vacation-related domains registered in May 2025, with 1 in 21 flagged as malicious or suspicious—cyber criminals target travel enthusiasts and property owners through phishing scams mimicking popular platforms like Airbnb and Booking.com.
As summer travel season kicks into high gear, cybercriminals are following the crowds online. Check Point Research (CPR) has uncovered a sharp spike in cyber threats tied to the hospitality and travel sector, with a 55% increase in newly created domains related to holidays and vacations in May 2025 compared to the same period last year. Of over 39,000 domains registered, one in every 21 was flagged as either malicious or suspicious.
This surge in deceptive web domains is no coincidence. Cyber criminals are capitalizing on the seasonal uptick in travel planning to craft convincing phishing scams, targeting consumers looking to book accommodations, secure travel deals, or respond to messages from seemingly legitimate platforms like Airbnb and Booking.com. From fake login pages with brand logos to manipulated email headers, the tactics are designed to mimic trusted services and steal credentials or payment details.
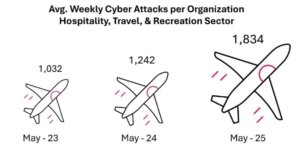
Simultaneously, the hospitality industry is facing an unprecedented wave of cyber attacks. In May alone, the average number of weekly attacks per organization in this sector hit 1,834, a staggering 48% increase from May 2024, and a 78% spike over two years. These coordinated campaigns not only threaten individual travelers but also pose risks to hotel chains, booking platforms, and other critical players in the global tourism ecosystem.
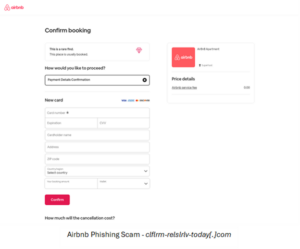
Airbnb Phishing Scam – Attempts to Steal Payment Details
Check Point Research has identified a phishing website operating under the domain clflrm-relslrlv-today[.]com, designed to impersonate the Airbnb brand. This fraudulent site mimics Airbnb’s payment page, including the official Airbnb logo attempting to deceive users. By creating a false sense of legitimacy, it lures victims into entering their payment details, ultimately stealing sensitive information such as card numbers, CVV and expiration date. The site is currently inactive.
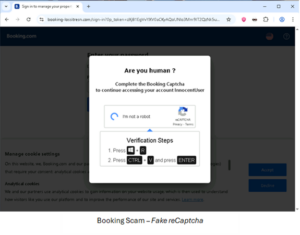
ClickFix Fake ReCAPTCHA Scam Targeting Booking.com Property Owners
Check Point Research has identified a malicious phishing domain site using ClickFix fake ReCaptcha method, operating under the domain booking-lossitresn[.]com, which was registered in the beginning of May and designed to impersonate the booking.com brand. This fraudulent site mimics the booking.com login page from the property owner side. After the user enters their username, a pop-up window appears with a fake ReCAPTCHA asking the user to “verify” they are human. Once the user confirms they aren’t a robot, the site prompts them to perform additional actions ofpressing Winkey + R, Ctrl + V and Enter. This pastes and runs a malicious command, triggering a PowerShell script that downloads a RAT payload (AsyncRAT) from a C2 server and installs it on the victim’s machine.


Booking.com Phishing Email Campaign
An additional phishing email campaign targeting booking.com property owners was recently found by Check Point Research. The campaign included several nearly identical emails, with the subject line stating that a guest had sent a message to the host regarding a possibly lost item from a past visit. The email senders were spoofed to appear as a reservation number, but were actually email addresses which seem to belong to corporate users whose emails might have been compromised or faked.
Each email requested the same action – review the guest’s request regarding a possibly lost item – which led to the same phishing link (https://knoji[.]digidip[.]net/visit?url=https://resrv-id89149[.]com). This redirected to the website resrv-id89149[.]com, and eventually to the subdomain booking[.]resrv-id89149[.]com. This website was registered on May 26th and is currently inactive. Based on the name of the final page, it is likely that this page also mimicked the booking.com login page.
A closer look at the phishing emails shows a wide variety of subjects and content, while keeping the same theme very clear. Even the text on the button differs from email to email. This might point to the usage of generative AI tools by the attackers to improve their efficiency and boost the social engineering aspects of the attacks. This may also help them in avoiding detection by some email security tools, by making each message different and elaborate.
Examples from the booking.com email phishing campaign:

The spike in phishing domains and targeted attacks is a reminder that cyber criminals don’t take holidays—if anything, they double down when user behavior becomes more predictable. For consumers eager to book that long-awaited getaway, vigilance is more important than ever.
Check Point Research recommends the following travel-season cyber hygiene tips:
- Book directly from official sources. Always type the website address manually or use trusted apps—avoid clicking links in emails or messages.
- Double-check URLs. Look for subtle misspellings or unusual domain endings (e.g., .today, .info) which are often used in scam sites.
- Enable multi-factor authentication (MFA). This adds an extra layer of security even if login credentials are compromised.
- Be cautious with public Wi-Fi. Use a VPN when accessing sensitive information like bank accounts or booking portals.
- Install endpoint security. Comprehensive mobile and desktop protection can detect phishing attempts and block malicious downloads in real-time.
Whether you’re a traveler planning your next adventure or a business securing customer data, proactive security measures are essential. As phishing scams grow more sophisticated and opportunistic, understanding the threat landscape—and knowing how to respond—can make all the difference between a safe holiday and a compromised one.
Stay informed. Stay secure. And don’t let cyber criminals turn your summer break into a security incident.




