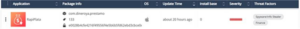
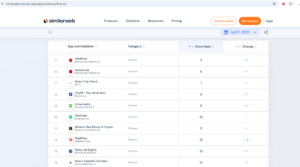
In February 2025, our detection engines identified a SpyLoan application on a victim’s device. The detected sample belonging to the “RapiPlata” application, which was available on Google Play (GP) and downloaded by over 100K victims. We estimate that around 150K victims have downloaded the app from both the Google Play Store and the Apple App Store, further highlighting the scale of the threat. This detection was made possible by Harmony Mobile’s machine learning model, which flagged the app as malicious. Notably, “RapiPlata” achieved a Top 20 ranking in the finance category on SimilarWeb’s platform in Colombia, indicating significant user engagement. Our analysis revealed that the app had extensive access to sensitive user data—including SMS messages, call logs, calendar events, and installed applications—even going so far as to upload this data to its servers. Although the app has since been removed from both Google Play and the Apple App Store, it remains accessible through third-party websites that deceptively present it as an official download from Google Play. Its prior availability and continued distribution underscore the risks posed by malicious financial applications. Given the severity of the situation, we immediately launched an investigation.
App Store Users Exploited by Fraudulent Loan Scheme
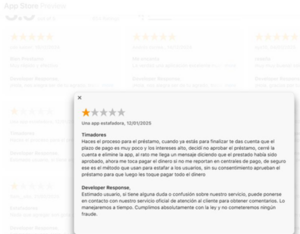
The app in question posed significant risks to users, and its malicious behavior has been well-documented. Victims reported being subjected to harassing messages and emails, including threats of being labeled as delinquent debtors and having their personal information accessed and released. These tactics, combined with misleading claims related to low-interest rates, indicate a fraudulent scheme designed to pressure victims into repaying loans they never consented to. Its prolonged presence on official app marketplaces underscores the scale of its impact. The Android version of the app compounded the problem, with severe data theft vulnerabilities that jeopardized victims’ privacy even further. With unauthorized loan approvals, fabricated fees, and data theft, this app was a clear threat to both financial security and personal data integrity.
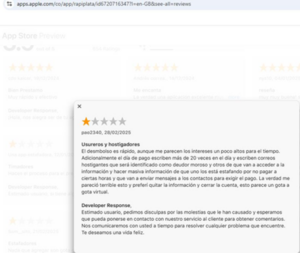
“It’s a scam. I downloaded the app and didn’t even complete the registration. Hours later, I received threatening emails saying I had to pay back a loan I never received.”
“They stole my contacts and started messaging people saying I owed money. This is criminal.”
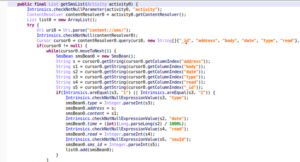
Code Analysis and Threat Correlation
Our initial research confirmed that RapiPlata exhibits characteristics typical of SpyLoan applications, including the abuse of permissions under the guise of “credit assessment,” keyword-based SMS scanning and exfiltration, and auto-downloads of malicious payloads from fake Google Play buttons. We then conducted a broader search across our internal databases and external sources for related samples. This investigation confirmed that RapiPlata is part of a larger SpyLoan malware operation, with other applications displaying the same malicious behaviors, including redirect chains leading to off-store APK delivery platforms. Alarmingly, RapiPlata has minimal to zero detection coverage on VirusTotal (VT), with some variants appearing on the platform without any detections.
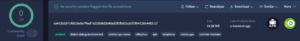
Connection to Previous SpyLoan Campaigns
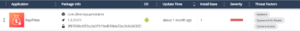
Further analysis uncovered strong similarities between RapiPlata and a previously identified SpyLoan app, “Préstamo Rápido,” which was removed from Google Play within the past year. The core data-exfiltrating functions remain nearly identical, with only minor syntax modifications and a new command-and-control (C2) server. These changes suggest an attempt to evade detection and re-enter Google Play under a different name.
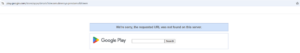
Preliminary investigations indicate that RapiPlata’s domain and Prestamo Rápido’s domain were both purchased from the same registrar. While this alone is not definitive proof of a direct link between the two apps, it adds to the growing number of similarities between them. Prestamo Rápido was active on Google Play from August 2022 and has long since been removed. RapiPlata was active on Google Play from October 2024 until its removal in March 2025. However, its website remains operational, deceiving victims into believing they are downloading the app from Google Play when, in reality, they are obtaining it from an unauthorized source.
Malicious Functionality and Privacy Violations
Despite its removal from Google Play, the official RapiPlata website misleads victims by displaying a Google Play download button. Clicking on it redirects to an external site (https[:]//t[.]copii[.]co/9YEPe) that automatically downloads an external version of the app instead of a Google Play Store certified app. This version retains all the data leakage vulnerabilities of its predecessors, allowing the developers to continue their operations outside of official app stores. We have identified multiple websites associated with the RapiPlata app.
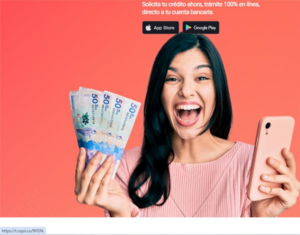
RapiPlata primarily targets Colombian users by promising quick loans. Beyond its predatory lending practices, the app engages in extensive data theft. Upon its first launch, it exfiltrates all SMS messages, call logs, and calendar data to its servers. The app claims these permissions are necessary for payment reminders (calendar access) and creditworthiness analysis (SMS, call logs, installed apps). However, there is no legitimate justification for such broad data collection, making this a clear violation of Google Play’s privacy policies.
| Function | Claimed Purpose | Actual Use |
| SMS Access | Creditworthiness scoring | Keyword scanning and full upload of inbox |
| Calendar Access | Payment reminders | Timeline profiling |
| Installed Apps | Loan eligibility check | Reconnaissance |
| Call Logs | Account validation | Behavioral data harvesting |
| Contacts | Assess creditworthiness based on references, and provide a contact as a guarantor for the loan | Contacts received coercive messages falsely claiming the victim was in default |

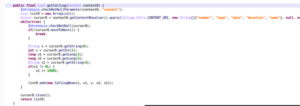
The application scans all SMS messages for specific keywords and uploads any message containing them to its server. While this may appear to focus on finance- and banking-related communications, the keyword list includes generic words such as “día” (day), “hasta” (until), “para” (for), “esta” (this), “por” (by/for), and “sido” (been) — terms that have little or no direct connection to financial transactions.

Even when keyword filtering is applied, it seems to function more as an illusion of selectivity rather than a genuine attempt to limit data collection. In some versions of the app, all SMS messages are uploaded indiscriminately. This process constitutes unauthorized data exfiltration under the guise of financial assessment.
Turning iOS Personal Data into Corporate Breach Vectors
On the surface, the theft of personal information such as SMS messages, call logs, calendar entries, and lists of installed applications from an iPhone might appear insignificant. However, even iOS, despite its robust security reputation, is vulnerable in such scenarios. Hackers targeting highly secure organizations protected by robust over-the-air (OTA) and advanced security frameworks can leverage these personal data points as essential links in a chain of sophisticated cyber attacks.
SMS and Call Logs: SMS messages and call logs can reveal authentication codes, internal organizational communications, or sensitive personal interactions. Attackers exploit intercepted authentication messages to bypass two-factor authentication (2FA), effectively compromising critical business accounts. Additionally, analyzing call logs allows adversaries to map social and professional relationships, making targeted spear-phishing or impersonation attacks significantly more credible and effective.
Calendar Data: Access to calendar entries offers attackers visibility into a victim’s daily activities, meetings, business travel, and sensitive corporate engagements. Calendar entries often contain attached Zoom links or presentations, providing attackers direct access to confidential discussions, company strategy, sensitive business data, or intellectual property. Since the Zoom links are exposed, attackers can not only be aware of meetings but also potentially join them. Most meetings include descriptive titles (e.g., “Quarterly Financial Review” or “R&D Strategy Update”), making it easy for an attacker to choose which meetings to target based on relevance.
While Zoom offers a security feature that requires the host to manually approve each participant joining the meeting, this is rarely enforced in practice. As a result, an attacker joining from an unrecognized email or generic name can eavesdrop on highly sensitive corporate discussions, including earnings results, strategic roadmaps, or product announcements—without detection.
Installed Applications: Information about installed apps reveals the technological ecosystem of the targeted individual and potentially the entire organization. Attackers utilize this knowledge to exploit known vulnerabilities within specific apps or craft tailored malware disguised as familiar software updates. Such targeted app-based attacks bypass generic security defenses, significantly raising the likelihood of successful infiltration, even on iOS devices.
Collectively, these seemingly innocuous personal data types provide a comprehensive intelligence profile. This profile empowers attackers to design sophisticated, targeted attacks—ranging from advanced social engineering attempts to highly personalized zero-day exploits—ultimately allowing attackers to circumvent even the most robust security measures.
How to Stay Protected Against SpyLoan Threats
Even the most trusted platforms, including the Apple App Store, are not immune to malicious applications. As seen with threats like RapiPlata, cyber criminals find ways to bypass security measures, disguising fraudulent apps as legitimate financial services. This case underscores the strength of Check Point’s solutions, which benefit from the deep integration and cooperation between products. The machine learning model that detected this app takes into account not only the behavioral indicators from Harmony Mobile’s engines but also data from Threat Cloud, which centralizes insights from across our entire security ecosystem. This cooperation allows our products to analyze more than just the APK itself; they assess other characteristics and events that may not be explicitly present in the app but can still signal malicious intent.
This integrated approach provides a more comprehensive understanding of threats, giving Check Point products access to a broader range of data and insights that enhance detection capabilities. Notably, Harmony Mobile detected the app before execution, preventing it from carrying out malicious activities. Additionally, Check Point was able to block malicious communication, stopping the app from interacting with its malicious server. To further protect users, the system alerted the user and admin console in real-time, ensuring a prompt response. To stay protected, users should consider advanced mobile security solutions like Harmony Mobile, which proactively detects and blocks SpyLoan apps, preventing unauthorized data exfiltration and malicious connections in real-time.
As threats like RapiPlata continue to evolve, it is crucial for users to remain vigilant when downloading financial or loan-related applications. Cybercriminals frequently exploit victims’ trust to steal sensitive data, making it essential to download applications only from verified sources, carefully review app permissions, and be cautious of apps requesting excessive access to personal data. RapiPlata, for example, was actively deployed in the wild, masquerading as a legitimate financial service, and even though it has been removed from the App Store, it had a significant period of availability and continued targeting real users.
For financial transactions and loan services, it is always safer to rely on official institutions such as banks and government-regulated lenders rather than third-party apps with unclear origins. Threat actors often create fake loan apps to trick victims into sharing banking credentials, personal data, or even making fraudulent payments. RapiPlata is a clear example of this fraudulent behavior, and its existence shows the real, tangible consequences victims face when interacting with these fraudulent apps.
With industry-leading threat intelligence and detection capabilities, Check Point ensures that your device and sensitive information remain secure from emerging mobile threats. For comprehensive protection, individuals and organizations should implement a multi-layered security strategy, combining robust endpoint protection with network-level defenses. Stay one step ahead of cyber criminals—secure your mobile environment with Check Point today.
Keywords for SMS retreival
| dia | day |
| saldo | balance |
| crediti | credits |
| credito | credit |
| recarga | recharge / top-up |
| monto | amount |
| vence | expires / due |
| interes | interest (financial) |
| bancaria | banking / bank-related |
| hasta | up to / until |
| efectivo | cash |
| codigo | Code |
| para | for |
| dinero | money |
| prestamo | loan |
| Numero | number |
| Esta | this (feminine) |
| cuenta | account / bill |
| PAGO | PAYMENT |
| Pesos | pesos (currency) |
| Por | by / for / per |
| sido | been |
| pagar | to pay |
| tarjeta | card |
| Pago | payment |
| exito | success |
| Informa | informs / reports |
| Bancolombia | Bancolombia (bank name) |
| Factura | invoice / bill |
| Aplica | applies |
| Banco | bank |
| Paga | pay / pays |
| compra | purchase |
| Tarjeta | Card |
| Consulta | Inquiry / Check |
IoCs
Websites:
• https[:]//www[.]dineroya[.]co/
• https[:]//www[.]rapiplata[.]co
• https[:]//home[.]parkwaysas[.]co/
- https[:]//www[.]rapiplata[.]pe/
Payload Url:
- https[:]//t[.]copii[.]co/9YEPe
RapiPlata sha256:
- d2413262042fa01e679795298d4541a114a73574c09d93240be64303946fc7f4
•e0028b4cfe4216f49556f4e5b6b5fd62ebd3cbce0ed774efe893e86ee65fb649
•3f87000c43f3cc2e37019ed590da72ec0c6c663257734095c5fd9306c11a6ce5
•ea453b597cf6610e9a7f4e87e25509d3d48e50f2fbd2cc65f3f641566448511f
•f13238211b5df56eb8901fb2d8d11355ab4f442f24f45c79b14e60c83a1d48b9
•cf597690738b875daddb964abc313b34049c76afb001df0f3b8bcd9f3d358826
•afb116cf99c020419679684035ff7c4e3ecdfce6c8842108c228eef4a13058bd
Prestamo Rapido sha256:
- f19c438d98921e5cb468395228fe51f98eb1670a20b3f7cad40783cc5a6156ca
•5a81cfd390f96b1797b65ecf528d6f2dc110a2393192e27c92e7232be8b31efc
•bca3a8a2ef6733e379b4b2e17c4b51f1b2ac147101b3196182c103a64d7059e7
•608ffecca9c20b1b8da704256727225987d2da7223e106e5f2dea3c383bfe6a3
•99b61add54c2e322f1ab48260197e10a99e1fd039a97744f2d14320c5c0ca646
•37086709e265de909df5b84384b934c9f5427f4b636287da6d1f9ecc70c73a9c
•2093d63e9bd882e0fe4033aa78544481e1ddf7f3d9932b1df6afa08fbeb795f0
•da6ccef711ad52b598a34de69b4dbefd21242b75a79272463bc66d3935e0e6a2




