
Microsoft Dynamics 365 Customer Voice Phishing Scam
Overview:
Check Point researchers have identified a new phishing campaign that exploits Microsoft’s “Dynamics 365 Customer Voice,” a customer relationship management software product. It’s often used to record customer calls, monitor customer reviews, share surveys and track feedback.
Microsoft 365 is used by over 2 million organizations worldwide. At least 500,000 organizations use Dynamics 365 Customer Voice, including 97% of Fortune 500 companies.
In this campaign, cyber criminals send business files and invoices from compromised accounts, and include fake Dynamics 365 Customer Voice links. The email configuration looks legitimate and easily tricks email recipients into taking the bait.
As part of this campaign, cyber criminals have deployed over 3,370 emails, with content reaching employees of over 350 organizations, the majority of which are American. More than a million different mailboxes were targeted.
Affected entities include well-established community betterment groups, colleges and universities, news outlets, a prominent health information group, and organizations that promote arts and culture, among others.
Campaign Execution Details:
The phishing emails center around financially focused themes. Subject lines typically discuss settlement statements, ALTA, EFT payment info, or closing disclosures.
As mentioned previously, the emails themselves include phony links. The links claim that the recipients have received a new voicemail or PDF document. All messages are intended to appear legitimate, as shown in the examples below:
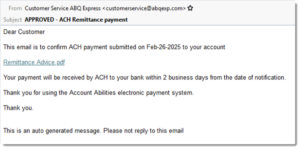
Example of phishing email
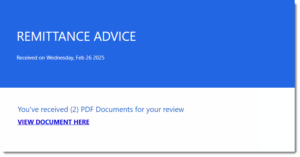
Example of phishing email
In the latter email, the attackers left a legitimate link embedded within the page and also added a fake additional link.
When recipients click on the illegitimate links, they are directed to a Captcha test, which is intended to convince targets that they are not interacting with a phishing email, and that instead, they are interacting with an authentic request.
Afterwards, the recipient is directed to a phishing site, which mimics a Microsoft login page. This is where the attackers attempt to steal users’ information.
Impact:
The primary objective of this phishing campaign is to pinch user credentials. In the event that cyber criminals are successful, they can gain unauthorized access to sensitive information and systems.
As a result, organizations could see the manipulation of internal accounts, the theft of funds and/or operational disruptions.
Mitigations:
Microsoft has blocked some of these phishing pages. However, some attempts may have reached inboxes before pages were taken down.
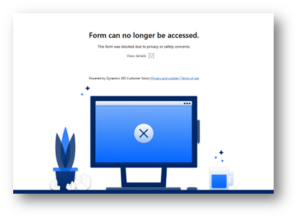
Example of Microsoft blocking phishing page
Cyber security leaders should inform employees about the potential for suspicious emails and the importance of confirming their origination points; especially those that claim to be from Microsoft services, including Dynamics 365 Customer Voice.
It goes without saying that businesses should ensure that they have the most advanced email security possible. Think AI-powered, cloud-delivered and multi-layered with inline, integrated threat protection mechanisms.
Check Point has successfully blocked emails from this campaign by extracting the links, and security layers have been added to products to prevent and detect future related threats.
More Information:
Check Point’s researchers have observed similar scams in the past, as documented in this article.



