
Ransomware’s Evolving Threat: The Rise of RansomHub, Decline of Lockbit, and the New Era of Data Extortion
1.Introduction
The ransomware landscape is witnessing significant changes, with new actors like RansomHub rising to prominence, while previously dominant groups such as Lockbit experience a sharp decline. Ransomware remains the most pervasive cyber threat, with financially motivated criminal groups deploying increasingly sophisticated tactics, including Ransomware-as-a-Service (RaaS) models and double extortion. This report, based on Check Point Research’s (CPR) September 2024 analysis, provides an in-depth review of the current ransomware trends, key actors, and their impact on sectors such as industrial manufacturing, education, and healthcare.
This evolution in tactics, coupled with the growing capabilities of emerging groups, poses significant challenges for organizations worldwide. The report aims to provide insights into these developments and offer guidance on how enterprises can better protect themselves against ransomware attacks.
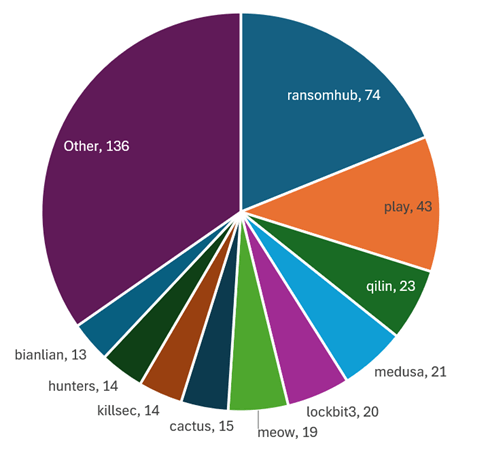
Figure 1 – Ransomware shame-sites victim analysis by threat actor, September 2024.
2.Key Findings
The key findings from Check Point Research (CPR) highlight the ongoing shift in the ransomware ecosystem, where newer actors are gaining ground while traditional powerhouses face declining influence. The September 2024 statistics reflect not only a change in the actors but also the continuous change in the strategies employed by these groups.
2.1.RansomHub’s Ascendancy
RansomHub, a relatively new player that emerged in February 2024, has quickly risen to dominate the ransomware landscape. The group has achieved significant success by operating under a RaaS model, allowing affiliates to carry out attacks using its tools and infrastructure.
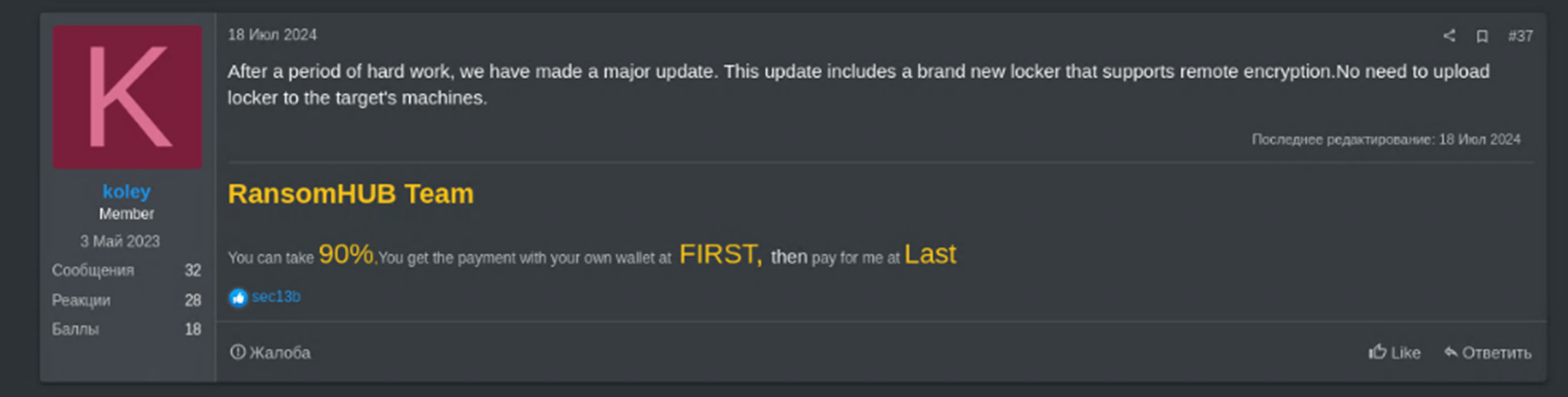
Figure 2 – RansomHub remote-encryption feature announcement on a darkweb forum.
In September 2024, RansomHub accounted for 19% of all ransomware victims, with 74 new victims, marking a slight increase from 72 in August 2024.
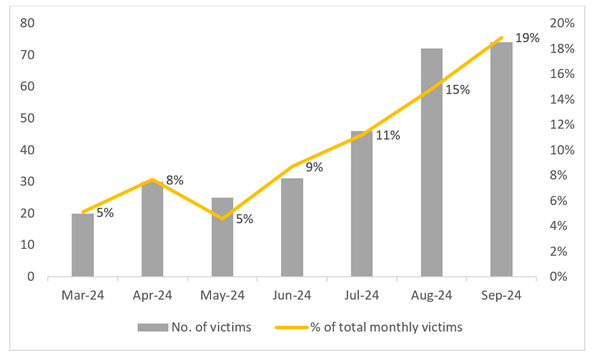
Figure 3 – RansomHub victims over time
RansomHub’s growth can be attributed to its use of advanced technological capabilities, such as remote encryption, which enables affiliates to encrypt local data without running local encryption processes, what makes its detection and prevention more complicated.
- Target Sectors: The group has primarily targeted U.S.-based companies, particularly in industrial manufacturing and healthcare. Despite a stated policy of avoiding healthcare organizations, 10 healthcare entities were attacked in September, including community clinics and surgical centers, suggesting loose oversight over affiliates.
- Global Impact: The impact of RansomHub has been felt globally, but the concentration of attacks in North America remains high, with 43% of its victims located in the United States.
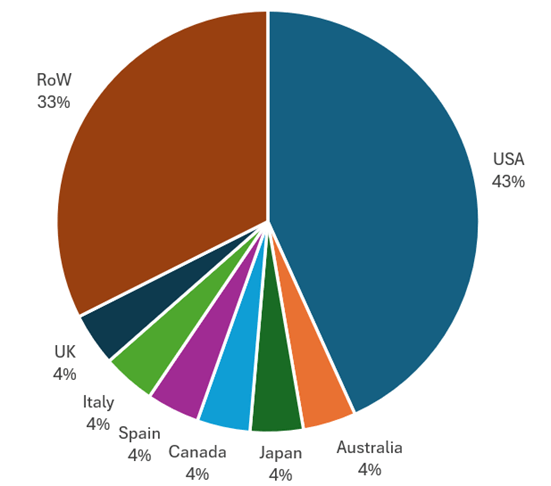
Figure 4 – Analysis of RansomHub’s reported victims by country, September 2024.
- Technological Innovation: RansomHub’s introduction of remote encryption highlights another technical improvement in the “cat and mouse” game with the defenders. This innovation allows affiliates to encrypt victim systems through exposed unprotected machines, reducing the risk of detection and increasing the success rate of attacks.
2.2.Lockbit’s Decline
Once responsible for 40% of all ransomware victims during 2022-2023, Lockbit has seen its operational capabilities plummet in recent months. In September 2024, the group accounted for just 5% of victims, with 20 new cases, down sharply from its peak activity in previous years.
A significant portion of Lockbit’s September claimed victims—approximately 40%—were recycled from previous attacks. This means that Lockbit either re-posted victims from earlier attacks or claimed victims already extorted by other ransomware groups. The recycling of victims is likely an attempt to maintain the appearance of ongoing activity following a major law enforcement crackdown in February 2024.
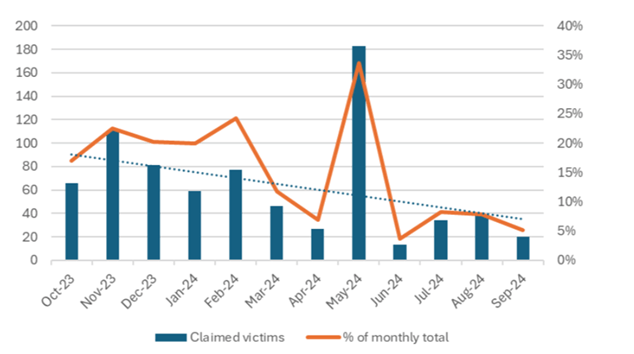
Figure 5 – Lockbit claimed victims’ data.
- Affiliate Confidence Maintenance: Lockbit’s reliance on its RaaS model means that it is dependent on the confidence of its affiliates in its platform. The posting of recycled victims is likely an attempt to show ‘business as usual’ façade following the February 2024 law enforcement crackdown on its operations. Lockbit relies on maintaining affiliate confidence in its infrastructure to ensure they continue using its platform and paying a portion of their earnings to the group. This suggests that Lockbit’s actual activity has declined even more than its already reduced claimed victim count over the past year suggests.
- Strategic Changes: Despite its diminished activity, Lockbit continues to focus on sectors that provide high returns, particularly industrial manufacturing and logistics, but its operational scale is now much smaller than before.
- Figure 5: Lockbit Activity Decline – Monthly Victim Data Extortion from 2023 to September 2024.
2.3.Meow Ransomware: Shifting to Data Extortion
Meow ransomware first appeared in late 2022 and initially followed the typical encryption-based attack model. However, in recent months, the group has shifted its focus toward data theft and extortion, abandoning encryption in favor of selling stolen data.
- New Business Model: Instead of locking files and demanding a ransom for decryption, Meow now steals sensitive data and offers the victim a choice: pay a ransom to prevent the data’s public release or allow the data to be sold to other cybercriminals. The Meow leak site currently lists stolen data with prices ranging from $500 to $200,000.
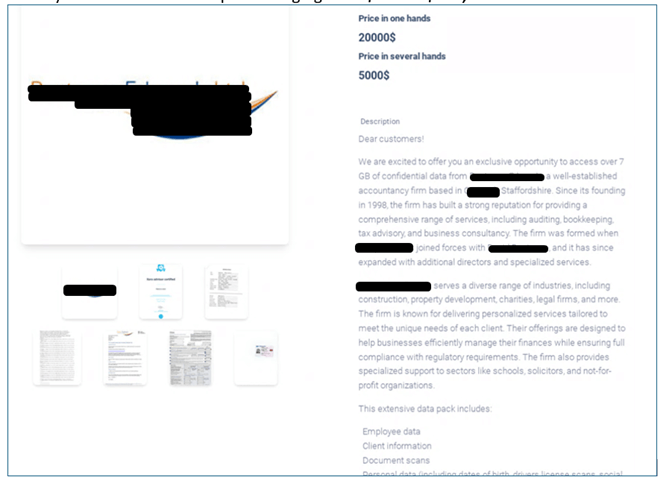
Figure 6 – Data offered for sale on the Meow Onion site.
- Non-Encryption Attacks: Meow’s approach reflects a broader continuous industry shift, as many ransomware groups are moving away from encryption-based attacks, which expose the attackers to higher risk of detection and the increasing use of backup solutions. By focusing on data theft, these groups can exploit sensitive information in ways that encryption alone cannot achieve.
2.4.Play Ransomware and Qilin’s Steady Activity
Play ransomware ranked second in September 2024, with 43 new victims, which is in line with its monthly average of 32 victims. Play continues to target U.S.-based companies, with 75% of its victims located in the United States, focusing primarily on the manufacturing and consumer goods sectors.
Similarly, Qilin ransomware (Agenda), a Russian-speaking RaaS group, continues to focus on North American targets. In September, 86% of its victims were located in North America, particularly in the U.S. and Canada. Both groups show steady, consistent activity but remain secondary to the dominant RansomHub.
3.Sectoral Targeting of Ransomware Groups
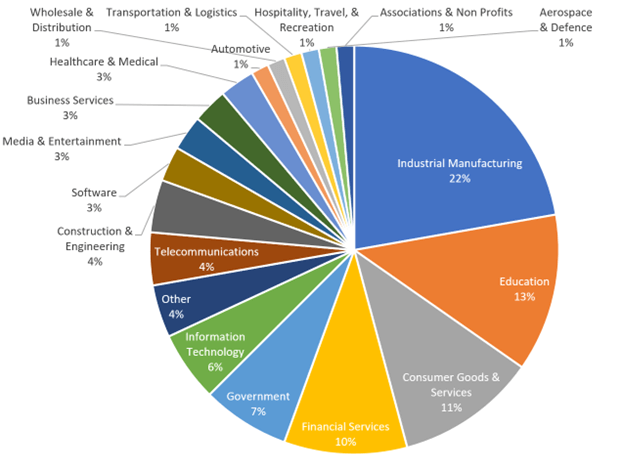
Figure 7- Analysis of reported ransomware victims by industry, September 2024.
3.1.Industrial Manufacturing: The Most Targeted Sector
The industrial manufacturing sector remains the most attacked by ransomware groups. In September 2024, RansomHub and Play ransomware directed a significant portion of their attacks at manufacturing companies, particularly in the United States.
- Legacy Systems Vulnerability: Many industrial manufacturers continue to rely on legacy systems that lack the necessary security measures to defend against modern ransomware attacks. These systems are often critical to production processes, and downtime can result in significant financial losses, making companies in this sector more likely to pay ransoms.
- Combination of IT and OT Networks – most industrial manufacturers have a unique combination of both IT and OT operational networks that in many cases interconnected to some degree. This combination poses a significant challenge to protect those efficiently.
- High-Value Data: Manufacturing companies store valuable intellectual property, including designs, patents, and supply chain information. This makes them prime targets for cybercriminals, who seek to monetize this data through extortion or black-market sales.
- Impact on Supply Chains: The disruption of manufacturing processes can have a ripple effect on global supply chains, amplifying the financial and economic impact of ransomware attacks on these businesses.
3.2. Education: A Growing Target
The education sector has become a key target for ransomware groups, second only to industrial manufacturing.
- Vast Networks and Insufficient Resources: Educational institutions operate vast digital networks that often lack adequate security measures. Budget constraints and a lack of dedicated cyber security staff make it difficult for schools and universities to implement robust defenses against ransomware attacks.
- Personal Data Risks: Schools store large amounts of personal data, including information on students, parents, and staff, making them valuable targets for data theft and extortion.
3.3. Healthcare: A Persistent Target Despite Public Statements
Despite some ransomware groups publicly stating that they avoid targeting healthcare organizations, RansomHub attacked 10 healthcare institutions in September 2024. These attacks included community clinics and surgical centers, demonstrating that affiliates are often not bound by these promises.
- Critical Data: Healthcare organizations hold sensitive patient data, including medical records, insurance information, and payment details. The critical nature of healthcare services makes these organizations more likely to pay ransoms to avoid disrupting patient care.
- Life-Threatening Consequences: The potential for life-threatening consequences due to service disruption makes healthcare one of the most vulnerable sectors. Cyber criminals exploit this urgency, knowing that healthcare organizations are under immense pressure to restore operations quickly.
4.Geographical Distribution of Ransomware Attacks
Ransomware attacks remain concentrated in North America, with 48% of all victims in September 2024 located in the United States. This is consistent with trends from previous months, where U.S.-based organizations have been the primary targets for ransomware actors.
- Western Europe also experienced a significant number of attacks, particularly in Germany, France, and the U.K., although these regions remain secondary to the crown jewel of victims in North America.
- Non-Western Victims: Ransomware groups continue to attack non-Western countries as well. In September 2024, an Iranian company paid $3 million in ransom to prevent the release of sensitive banking data from 20 Iranian banks.
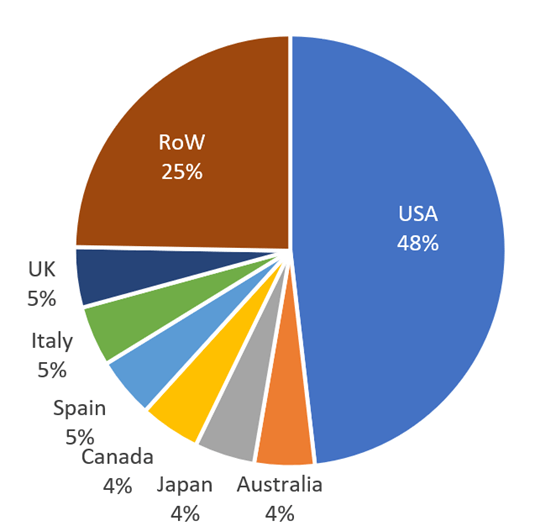
Figure 8 – Analysis of reported ransomware victims by country, September 2024.
5.Tactical Shifts: From Encryption to Data Extortion
One of the most significant changes observed in 2024 has been the shift in ransomware tactics, with many groups moving away from encryption-based attacks toward data theft and extortion.
5.1. Data Theft as the New Revenue Model
Traditional encryption-based attacks, while still effective, have been increasingly countered by companies through the implementation of backup systems that mitigate the damage caused by data encryption. In response, ransomware groups like Meow have pivoted to stealing sensitive data and threatening to release it unless ransoms are paid.
- Meow’s Shift to Extortion: Meow ransomware has embraced this model fully, with stolen data now being sold or auctioned on the Darkweb. Data pricing ranges from $500 to $200,000, depending on the sensitivity and potential market value of the stolen information.
5.2. The Challenges of Data Extortion for Enterprises
This shift toward data extortion presents a new challenge for enterprises. Even if data is backed up, the leakage of sensitive information can still cause significant reputational damage and result in legal liabilities. Organizations are now forced to balance the cost of paying a ransom with the risk of having their data exposed publicly.
6.What This Means for Enterprises
The findings from Check Point Research have far-reaching implications for businesses across sectors. As ransomware tactics evolve, companies must adjust their cyber security strategies to remain resilient.
6.1. Increasing Ransomware Sophistication
Ransomware groups like RansomHub are leveraging new tactics such as remote encryption and take to the heights the RaaS business models to scale their operations. Enterprises can no longer rely on traditional defenses to protect their systems.
- AI-Powered Defense: Companies must invest in AI-driven threat prevention solutions that can detect and neutralize ransomware attacks in real-time. The ability to predict and prevent attacks before they occur is critical to staying ahead of these sophisticated threats.
- Cloud-Based Solutions: Cloud-based cyber security platforms are essential for businesses looking to secure their networks in a decentralized work environment. These platforms offer real-time detection, automatic response, and scalability to defend against large-scale ransomware attacks.
6.2. Data Theft and Extortion Require Comprehensive Solutions
The shift from encryption to data extortion highlights the need for companies to focus on securing sensitive data, not just protecting against encryption-based attacks.
- Data Encryption and Segmentation: Organizations must ensure that data encryption is implemented across all critical systems, and network segmentation is used to minimize the risk of lateral movement in case of a breach.
- Zero-Trust Architectures: By adopting zero-trust architectures, companies can reduce the risk of attackers gaining access to critical systems. Under this model, every entity inside and outside the network is verified continuously, reducing the potential for insider threats or lateral movement after a breach.
6.3. Sector-Specific Cyber security Strategies
Industries like industrial manufacturing, education, and healthcare are particularly vulnerable to ransomware attacks. These sectors must invest in tailored cyber security solutions to address their specific challenges.
- Operational Technology (OT) Security: Manufacturing companies need to focus on securing their OT environments, which are often poorly protected and susceptible to ransomware attacks. This includes implementing intrusion detection systems and AI-based monitoring to detect anomalies in OT networks.
- Educational Institutions: Schools and universities should focus on strengthening their IT infrastructures and providing cyber security awareness training to staff and students. Educational networks are large and often difficult to secure, making them prime targets for ransomware groups.
- Healthcare Security: Healthcare organizations must prioritize securing medical devices and protecting patient information. These organizations need real-time monitoring systems and automated incident response tools to ensure the continuity of care during a cyber incident.
6.4.The Importance of AI-Driven Defenses
As ransomware tactics continue to evolve, companies must adopt AI-driven security solutions to defend against these emerging threats. AI-powered systems can automatically detect and neutralize threats based on behavior patterns, significantly reducing the risk of a successful attack.
- Proactive Defense: Investing in AI-based threat intelligence platforms will allow businesses to predict and prevent ransomware attacks before they cause significant damage.
Conclusion: The Future of Ransomware and What It Means for Enterprises
The September 2024 Ransomware Status Report reveals a rapidly evolving ransomware landscape marked by more complex and dangerous tactics. RansomHub’s rapid rise, Lockbit’s decline, and the shift to data extortion by groups like Meow indicate that ransomware is becoming more difficult to prevent and mitigate. These changes demand a stronger focus on safeguarding data rather than relying solely on preventing breaches.
Ransomware has transitioned into an organized, scalable business model via Ransomware-as-a-Service (RaaS), where even low-skilled cybercriminals can launch sophisticated attacks. Global affiliate networks have democratized cybercrime, driving an alarming increase in attack volume. For enterprises, this shift means facing an ever-growing threat from a global marketplace of cybercriminals.
As groups like Meow prioritize data theft and extortion, even the most prepared companies with solid backup strategies remain vulnerable. Data can be stolen and sold, causing significant reputational and legal damage. To counter this, businesses must go beyond traditional backups and implement data-loss prevention (DLP) systems, enhanced encryption, and stringent access control policies. AI-driven threat detection is also crucial in combating modern ransomware tactics.
Lockbit’s decline serves as a reminder of the competitive and volatile nature of cybercrime. Although diminished, it has been replaced by groups like RansomHub, demonstrating that vigilance and real-time threat intelligence are essential to stay ahead of emerging threats.
To defend against this new wave of ransomware, enterprises must adopt AI-driven security solutions and implement zero-trust architectures. AI systems are vital for detecting and mitigating ransomware in real-time, while zero-trust ensures that no user or device is trusted by default, preventing further damage if a breach occurs.
Certain industries, like industrial manufacturing, healthcare, and education, are particularly vulnerable. These sectors need tailored solutions to secure legacy systems and protect sensitive data. In healthcare, ransomware is not just a cyber security threat—it can disrupt critical services, making automated incident response and real-time monitoring essential.
The future of ransomware shows no signs of slowing down. Enterprises must adopt proactive cyber security strategies, including AI-driven defenses and zero-trust models, to survive in this ever-changing threat landscape. Those that invest in real-time threat intelligence and comprehensive data protection will be the ones to withstand these evolving challenges.
By implementing these solutions, organizations can navigate the next generation of cyber threats and maintain resilience in an increasingly hostile environment.



