- Check Point Research uncovered the YouTube Ghost Network, a large-scale malware distribution operation that used fake and compromised YouTube accounts to distribute infostealers such as Rhadamanthys and Lumma.
- More than 3,000 malicious videos were identified and removed after being reported by Check Point Research, disrupting one of the largest malware operations seen on YouTube.
- The operation relied on cracked software and game hack videos to lure victims into downloading password-protected archives containing malware.
- Compromised accounts were used to post videos, share links, and flood comment sections with fake endorsements, creating a false sense of trust.
- The investigation reveals a growing trend of cyber criminals exploiting social platforms and engagement tools to distribute malware at scale.
Check Point Research uncovered a large-scale cyber network hiding in one of the internet’s most trusted spaces: YouTube. What appeared to be harmless tutorials and software demos turned out to be a sophisticated malware distribution network known as the YouTube Ghost Network.
The operation used compromised and fake YouTube accounts to spread infostealers such as Rhadamanthys and Lumma, often disguised as cracked software or gaming cheats.
After a months-long investigation, Check Point Research reported more than 3,000 malicious videos to Google, leading to their removal and disrupting a major malware distribution channel.
For a detailed technical analysis, view the complete research report by Check Point Research.
https://research.checkpoint.com/2025/youtube-ghost-network/
Inside the YouTube Ghost Network
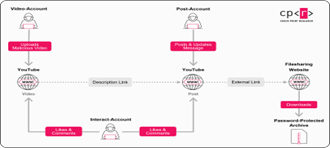
YouTube Ghost Network operation.
The Ghost Network is not a random collection of rogue uploads but a coordinated system of fake or hijacked accounts designed to appear trustworthy.
Each account type plays a distinct role:
- Video Accounts: Upload tutorial-style videos that include links to download malicious files.
- Post Accounts: Publish community posts containing passwords and updated links.
- Interact Accounts: Post positive comments and likes to make malicious videos appear safe.
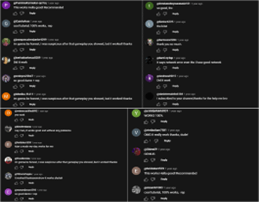
Positive comments on the video.
This modular structure allows the operation to scale quickly and survive account bans, making takedowns more complex and continuous.
From Cracked Software to Credential Theft
The most common lures were free or cracked software such as Adobe Photoshop, FL Studio, and Microsoft Office, or game hacks for titles such as Roblox.
Victims were instructed to:
- Download an archive hosted on Dropbox, Google Drive, or MediaFire.
- Disable Windows Defender temporarily.
- Extract and install what was described as legitimate software but was in fact malware.
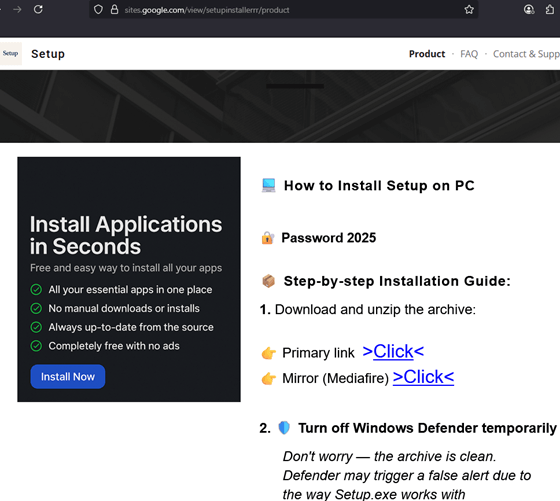
Google Sites phishing page.
Once executed, these infostealers exfiltrated credentials, cryptocurrency wallets, and system data to command-and-control servers that often rotated every few days to evade detection.
Campaign Highlights
- A compromised YouTube channel with 129,000 subscribers posted a cracked version of Adobe Photoshop, reaching 291,000 views and over 1,000 likes.
- Another compromised channel targeted cryptocurrency users, redirecting viewers to Google Sites phishing pages hosting Rhadamanthys Stealer.
- Threat actors regularly updated links and payloads, enabling persistent infection chains even after partial removals.
Disruption and Takedown
Check Point Research tracked this activity for over a year, mapping thousands of interconnected accounts and campaigns. Through direct collaboration with Google, Check Point Research facilitated the removal of more than 3,000 malicious videos, cutting off one of the most scalable malware distribution methods observed on YouTube to date.
This work demonstrates the importance of proactive threat intelligence and coordination between security researchers and platform operators. By identifying and reporting these campaigns, Check Point Research helped safeguard millions of potential victims and restore trust in one of the world’s most widely used platforms.
The Bigger Picture: Trust as a Target
This campaign reflects a broader shift in cyber criminal strategy. By exploiting engagement mechanisms such as likes, comments, and posts, attackers are turning social credibility into a tool for infection.
Unlike traditional phishing, these attacks succeed because they appear authentic. The manipulation of platform trust represents a new frontier in social engineering, where the appearance of legitimacy becomes a weapon.
How to Stay Protected
For Users
- Avoid downloading software from unofficial or cracked sources.
- Never disable antivirus protections at an installer’s request.
- Treat highly liked “free” software videos with skepticism.
For Platforms
- Strengthen automated detection of suspicious engagement patterns.
- Identify clusters of linked accounts posting similar URLs.
- Partner with cyber security vendors for proactive threat removal.
Check Point Protections
Check Point Threat Emulation and Harmony Endpoint provide protection against the Rhadamanthys and Lumma infostealers and the delivery chains identified in this campaign.
Together with industry collaboration, these solutions help close the gap between discovery and disruption.
Conclusion
The YouTube Ghost Network shows how easily trust can be manipulated at scale and how effective collaboration can be in countering it.
Through detailed investigation and coordinated reporting, Check Point Research helped remove more than 3,000 malicious videos, protecting users worldwide from infection and demonstrating that platform exploitation can be stopped when security and industry work together.
For a detailed technical analysis and full list of indicators of compromise, visit the complete research report by Check Point Research.




