Cloud Risk Mitigation: Putting it in Context
For many cloud security teams, prioritizing alerts on a day-to-day basis can be overwhelming and impossible to manage. For every cloud application, server, and workload added, the number of alerts piles up. Security teams have no time to go into each alert, investigate the findings, and prioritize the alerts themselves—never mind other security issues that may not even be on their radar due to a complete lack of visibility.
Gartner: It is Critical to Prioritize Risks Identified and Provide Sufficient Context for Remediation
To address this issue, Gartner emphasizes the importance of context within CNAPP solutions when it comes to risk management in their 2023 Market Guide for Cloud Native Application Protection Platforms
“Deep understanding of the relationships between the different elements of a cloud-native application is critical in order to deliver against the vision of RiskOps. In other words, to make risk identification remediation operational, CNAPP tools must be able to build a model of the application code, libraries, containers, scripts, configuration and vulnerabilities to identify where the effective risk resides. Since risk-free applications are impossible, the challenge for information security shifts to risk-prioritizing findings according to business context, identifying the root cause and getting developers to focus first on the findings that are of the highest risk and the highest confidence of potential impact to the business. Likewise, a deep understanding of the relationship between developers/development teams across the life cycle of an application is critical to identifying the right developer/development team or engineering team to remediate the risks identified (and to provide them with sufficient context to understand and remediate the risks quickly and effectively).”
– 2023 Gartner Market Guide for Cloud-Native Application Protection Platforms (CNAPPs)
Solution: Check Point CloudGuard’s Effective Risk Management Capabilities
This is where Check Point CloudGuard’s Effective Risk Management (ERM) engine comes in. By applying context across cloud implementations to identify and prioritize risks and security vulnerabilities—even those in unknown workloads—security teams can easily determine where to take action. Even more, CloudGuard will base its prioritization on the unique needs determined by the business. This allows teams to solve issues quickly by focusing on the risks critical to their business while automating security throughout their cloud environment.
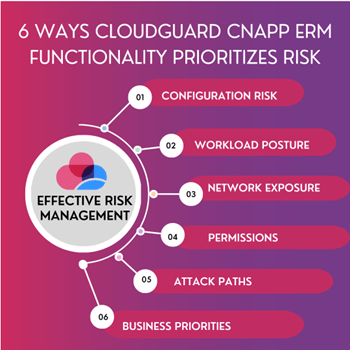
With CloudGuard, teams can:
- Prioritize risks based on full context, including:
- configuration risks
- workload posture
- network exposure
- permissions
- attack path
- business priorities
- Focus on threats across clouds, workloads, and code
- Deliver optimized remediation guidance based on the fastest path to risk reduction
Let’s take a deeper look at how CloudGuard’s ERM capabilities help security teams.
Manage risk at a glance for greater operational efficiency
CloudGuard’s ERM engine automatically brings organizations’ data and inputs together to prioritize and quickly address any risks or vulnerabilities. This helps eliminate the overall complexity of managing cloud security.
First, CloudGuard maps the attack surface of each cloud asset and combines it with contextual information, assessing the business impact of each asset and giving security teams a prioritized list of assets at risk along with clear, actionable remediation steps. All of this is consolidated into the CloudGuard ERM risk dashboard:
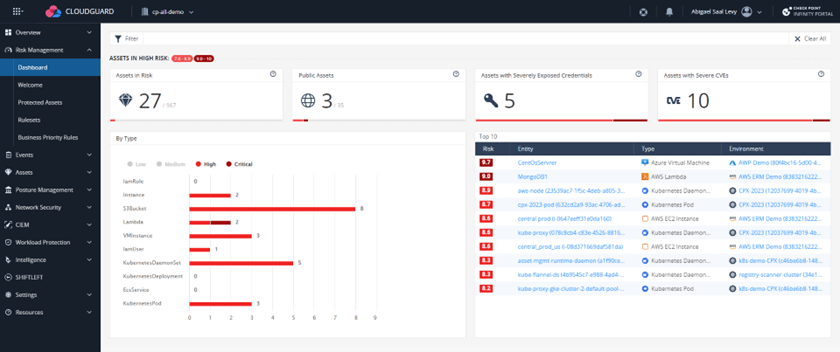
Figure 1. CloudGuard’s ERM dashboard offers a simplified view of security data at a glance.
Quickly drill down to identify issues that require immediate attention
Security teams will see at a glance which assets are at higher risk. For instance, the dashboard below highlights those publicly exposed or with high-severity common vulnerabilities and exposures (CVEs).
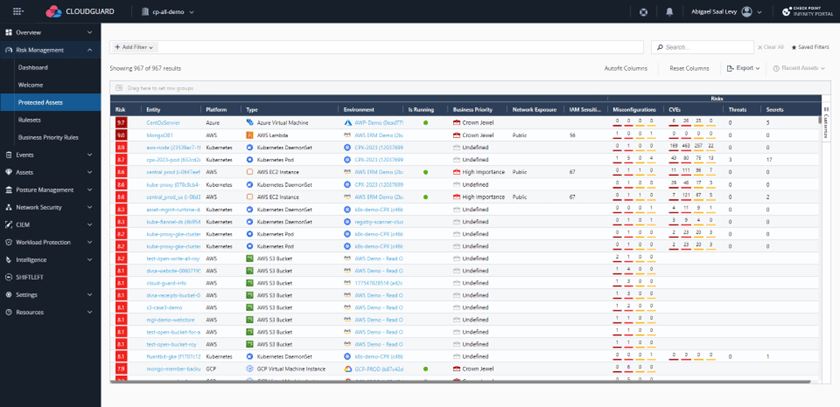
Figure 2. CloudGuard’s ERM reduces time to remediation by prioritizing known assets by risk score and providing guidance toward the most efficient action.
Prioritize assets based on the risk score
CloudGuard displays assets sorted by risk score, which is based on several factors clearly outlined in the columns, such as business priority, public exposure, number of misconfigurations, etc.
The highest-risk assets that need attention first are shown at the top:
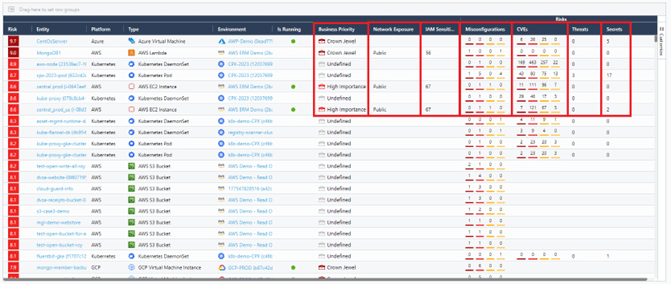
Figure 3. CloudGuard’s ERM engine analyzes inputs from within the platform and external inputs to identify risks in context and accurately prioritized.
To calculate a risk score, several factors are taken into consideration:
Misconfigurations
CloudGuard can be configured to only consider specific misconfigurations or all findings from our posture management module by default.
Vulnerabilities when relevant
There are three types of vulnerabilities: CVEs, Threats (such as malicious files on a machine), and Secrets (exposed credentials). With our Agentless Workload Posture, vulnerability information can be obtained natively within CloudGuard or through integration with external vulnerability scanners, such as AWS Inspector.
Asset exposure
Internet exposure contributes to the likelihood of an asset being exploited. Using its graph database, CloudGuard analyzes connections between assets and creates a topology map of the organization’s cloud network. This allows CloudGuard to discover exposed assets even when the network configuration is complex and the exposure results from unplanned asset connections.
IAM Sensitivity
ERM considers not only the likelihood of an attack but also the impact it may have. One of the factors that relate to impact is IAM sensitivity. CloudGuard’s ERM engine calculates the IAM sensitivity, measuring the potential damage an asset with IAM permissions could cause. For example, the consequences could be severe if an attacker gains access to an instance with a highly privileged IAM role.
Business Priority
Business Priority is another vital consideration as it measures a compromised asset’s overall impact on the business. Optionally, business priorities can be defined for assets using parameters such as the cloud account that holds the asset, tags, or naming conventions. Teams can also define which assets are “the crown jewels” and which are less critical to ensure their risk is prioritized if problems are discovered.
For example, an organization can assign the highest priority to its payment application—”the crown jewel”—and ensure assets in a testing environment containing only mock data are lower priority. When a crown jewel is misconfigured or vulnerable, its risk score is elevated, prioritizing the business’s most critical risks.
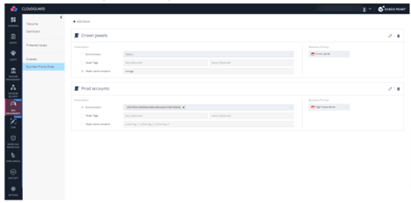
Figure 5. Using CloudGuard ERM to define business priority–such as low, high, or crown jewel – and rank specific assets accordingly.
Drill down into the risk with detailed information about each asset.
Putting all this data together gives a complete risk view of any specific asset in a company’s cloud environment. To get more detail, security teams can drill down into any particular asset from the ERM dashboard or the Protected Asset list.
The example below details the vulnerabilities found on a cloud asset. On the left, tabs are shown for CVEs (organized by package), Threats, and Secrets. Additionally, the agentless workload protection (AWP) component, integrated into the CloudGuard CNAPP platform, allows access to the Remediation Summary tab, providing a list of necessary remediation actions. This could include packages to upgrade, credentials to remove from a specific line of code, or other recommendations.
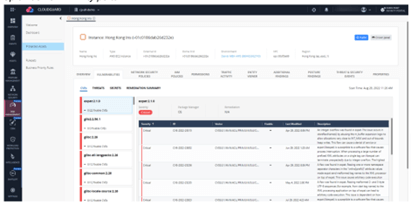
Figure 6. CloudGuard’s ERM dashboard lets teams drill down into a single asset to view risk type, remediation, exposed secrets, and package updates needed, delivering both context and efficient steps for resolution.
With asset prioritization based on risk scoring and actionable insights based on Artificial Intelligence (AI), security teams can stay one step ahead, centering their efforts first on the threats that have the highest impact on the business while ensuring that security is properly maintained across the cloud environment.
CloudGuard ERM: A better way to manage real-world risk
Cloud security today is more complex than ever, and security teams are spread thin. Teams not only need greater visibility, they need security tools that can seamlessly move faster. A seismic shift in mindset is necessary: moving from “locking it all down” to simplifying cloud security and making it easier to do the right thing. With the release of CloudGuard CNAPP, including integrated ERM functionality, Check Point does just this—delivering a smooth experience with agentless deployments and seamless integrations to provide actionable security guidance in context. Security teams get the resources needed to stay ahead, to stay focused on critical business priorities, and to ensure nothing falls through the cracks.
Securing all cloud assets and environments in one easy-to-use platform, CloudGuard covers the entire development lifecycle from code to cloud. In addition to its integrated ERM functionality, CloudGuard CNAPP includes:
- Cloud security posture management (CSPM)
- Workload Protection (Containers, Serverless)
- Web Application & API Security
- Cloud Detection and Response (CDR)
- Cloud infrastructure entitlement management (CIEM)
- Developer Security
To see these capabilities for yourself, sign up for a free demo or start using CloudGuard CNAPP today,