
Disrupting the Ransomware Attack Chain with Hybrid Mesh Security (Part 1)
In this three-part blog series, we explore how a hybrid mesh architecture can effectively break the ransomware attack chain.
- Part One examines the evolving state of ransomware in 2025, unpacks the stages of the ransomware attack chain, and explains why fragmented security architectures continue to fail.
- Part Two highlights five critical ways a hybrid mesh approach uniquely disrupts the ransomware lifecycle, from initial access to lateral movement and data exfiltration.
- Part Three features four key recommendations for CISOs from cyber security expert Pete Nicoletti and offers a concise overview of Check Point’s hybrid mesh architecture strategy.
Stopping Ransomware: How a Hybrid Mesh Architecture Disrupts the Attack Chain
Part One
The Evolving Threat of Ransomware in 2025
Ransomware has matured into a persistent and sophisticated business risk. According to the World Economic Forum’s Global Cybersecurity Outlook 2025, ransomware remains one of the top five global cyber threats due to its destructive impact, frequency, and increasing organizational disruption. The Cybersecurity and Infrastructure Security Agency (CISA) continues to issue joint advisories warning about ransomware groups adopting more advanced tactics, including extortion, data theft, and long undetected dwell times inside hybrid networks.
Recent data from Check Point Research shows that ransomware attacks surged by 33% globally in 2024, with the average number of weekly attacks per organization exceeding 1,200—the highest in three years. Notably, the State of Cyber Security 2025 report highlights a disturbing trend: attackers are spending more time inside networks before executing payloads, with dwell times extending up to 9 days in some cases. This extended presence allows threat actors to conduct reconnaissance, disable backups, and identify high-value targets—maximizing damage and pressure during encryption extortion and data exfiltration. The implication for CISOs is clear: traditional point-in-time “detect only” defenses are no longer sufficient—continuous monitoring, tool coordination and real-time containment are now mission-critical.
In today’s hybrid enterprise environments—where critical workloads span data centers, multiple cloud providers, 3rd parties and remote users—the attack surface is broader and more complex. According to the IBM Cost of a Data Breach Report 2024, breaches involving data distributed across multiple types of environments occurred more often (40%) than those in public cloud (25%), on-premises (20%) or private cloud (15%). The challenge is no longer preventing every breach but containing the attacker before real damage is done.
Breaking Down the Ransomware Attack Chain
Ransomware follows a structured, multi-stage attack pattern commonly referred to as the attack chain. See figure 1. These stages typically include:
- Initial access – via phishing, credential theft, or exploitation of vulnerabilities (often listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog).
- Establishing foothold and persistence.
- Privilege escalation.
- Lateral movement.
- Data exfiltration and target discovery.
- Payload execution and extortion.
Both Gartner and CISA identify lateral movement as the most under-monitored and least-controlled phase of this chain—yet it’s where attackers gain access to the systems that truly matter to a business. Once inside, threat actors often escalate privileges, impersonate users, and silently move through unsegmented networks, searching for backup systems, file servers, and high-value databases.
This stage is also where the opportunity to contain an attack still exists—but only if the organization has east-west visibility and responsive controls in place. Without it, ransomware becomes a business continuity crisis within hours.
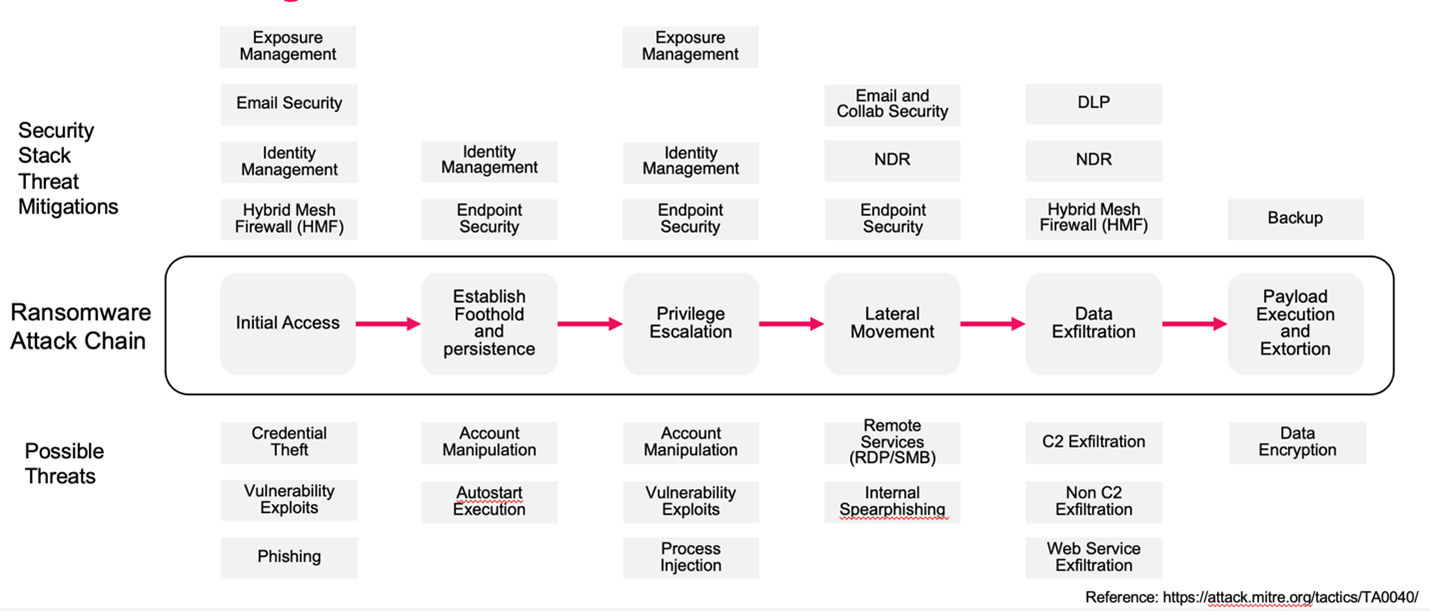
Figure 1. Ransomware Attack Chain
Why Fragmented Defenses Fall Short
Despite heavy investment in cyber security tools, many organizations still operate with siloed infrastructure: one set of firewalls for on-prem networks, cloud-native security groups for cloud workloads, endpoint agents for remote workers, and yet another console for SD-WAN or SaaS controls. See figure 2.
This fractured approach results in inconsistent policy enforcement, incomplete visibility, and slow response coordination. In their Strategic Roadmap for Zero Trust Security Program Implementation, Gartner calls out “The need to define policy at scale…” as one of the main internal complications that hinder effective implementation of a zero trust architecture. A fractured policy environment makes this task that much more difficult.
Even more troubling, cloud misconfigurations continue to be a top initial access vector. CISA has repeatedly warned that improperly configured IAM roles, overly permissive storage buckets, and unused open ports continue to serve as footholds for ransomware in hybrid and multi-cloud environments.
Legacy firewalls are not designed to address this hybrid complexity. They struggle to inspect traffic between cloud workloads, remote users, and SaaS apps. They don’t integrate with identity providers. And they don’t provide centralized control—leaving critical decisions siloed across teams.
Many organizations are also struggling with fragmented security management, many security products, and services don’t communicate or share knowledge with each other.
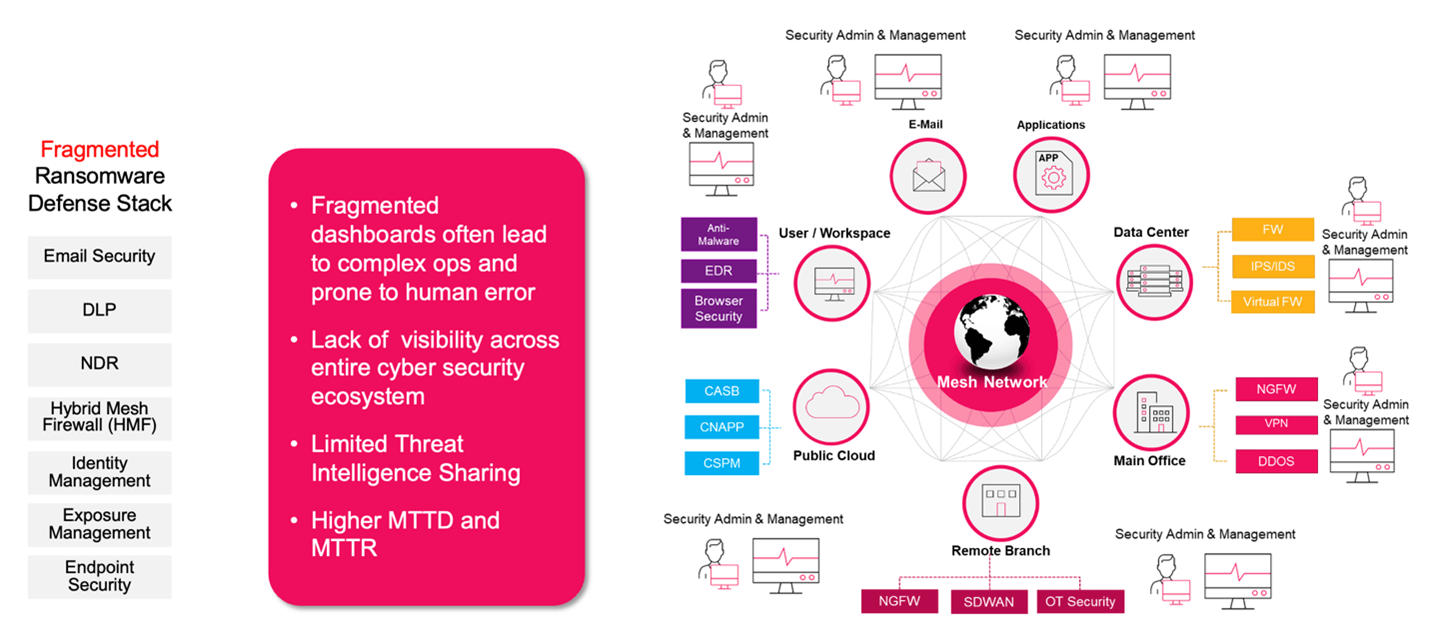
Figure 2. Fragmented Ransomware Defense
Coming Soon: Part 2 of “Stopping Ransomware: How a Hybrid Mesh Architecture Disrupts the Attack Chain”
In the next installment; we’ll explore the five key ways a hybrid mesh architecture breaks the ransomware kill chain—strengthening defenses at every stage of the attack.



