
How to Defend Against Credential Attacks with a Hybrid Mesh Architecture
Introduction
Credential-based attacks have reached epidemic levels. The 2025 Verizon Data Breach Investigations Report (DBIR) underscores the trend: 22% of breaches now start with compromised credentials, while Check Point External Risk Management found that leaked credential volumes surged 160% year-over-year. Attackers increasingly prefer to “log in” rather than “hack in,” leveraging a flood of exposed passwords, API keys, and tokens circulating from breaches and dark web leaks.
For CISOs, the message is clear: identity is now the perimeter, and defenses must reflect that reality with coherence and context.
Key takeaway: Credential threats — from OAuth abuse, to API key exposure — demand identity-aware, unified defense architectures.
The Expanding Credential Threat
Credential abuse now goes far beyond passwords, as attackers exploit keys, tokens, and AI-driven phishing to expand risk across cloud and SaaS.
- Beyond passwords: Attackers target API keys, OAuth tokens, SSH keys, and cloud service tokens. Many of these bypass MFA and can persist even after password resets.
- Infostealer malware: According to Check Point Research, families like Lumma, RedLine, and StealC surged 58% in 2024, harvesting browser-stored credentials and session tokens en masse.
- AI-enhanced phishing: Generative AI tools now craft flawless phishing emails, fake portals, and even voice-cloned calls, bypassing awareness programs and traditional filters.
Key takeaway: Credentials are no longer just user logins—they’re infrastructure keys and tokens woven deep into SaaS and cloud operations.
Why Traditional Security Fails: Fragmentation
Credential attacks succeed because tools don’t work together. Traditional security systems often operate in isolation, leaving gaps attackers can exploit.
Siloed visibility: IdPs see logins, firewalls track traffic, endpoints catch malware, but none connect the dots. A suspicious login may be logged, but without endpoint or network context, it’s dismissed.
Inconsistent policies: MFA on VPN but not SaaS; strong AD passwords but static API keys in the cloud. The 2024 Snowflake breach exploited precisely these gaps, enabling attackers to enter environments with inconsistent MFA enforcement.
Slow threat sharing: An endpoint may detect infostealer malware, but the alert never reaches SaaS or the IdP quickly enough. Attackers replay stolen credentials while defenders are still correlating logs.
Key takeaway: Fragmentation leaves exploitable seams. Attackers exploit those seams faster than siloed defenses can respond.
Hybrid Mesh Architecture: The Unified Model
Fragmented defenses leave gaps. A Hybrid Mesh Architecture closes them by unifying identity, policy, and threat intelligence across all environments.
A Hybrid Mesh Architecture (Hybrid Mesh) blends:
- Gartner’s Cybersecurity Mesh Architecture (CSMA): Distributed controls with unified intelligence.
- NIST SP 800-207 Zero Trust: Continuous verification, least privilege, and adaptive access.
- Hybrid Mesh Firewalls (HMF): Combining hardware, virtual, and cloud-native enforcement into a single policy layer.
With Hybrid Mesh, identity becomes the connective tissue: a login anomaly detected by one tool automatically propagates across endpoints, firewalls, and SaaS platforms. AI-driven analytics and automation enforce real-time responses, reducing mean time to detect (MTTD) and mean time to respond (MTTR).
Key takeaway: Hybrid Mesh operationalizes Zero Trust through an identity-centric, interoperable mesh that spans hybrid environments.
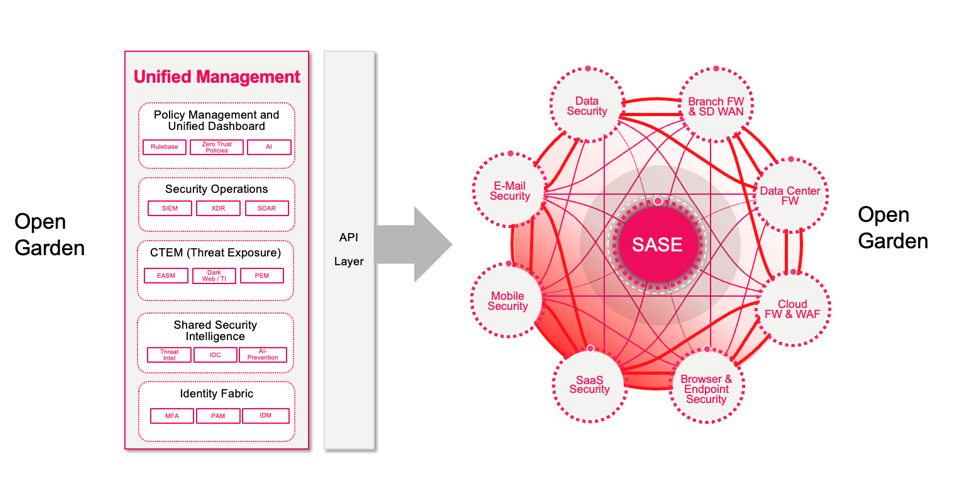
Figure 1: Hybrid Mesh architecture
Figure 1 depicts Hybrid Mesh as a connected hub: unified management and dashboards at the center, Zero Trust enforcement across endpoints, browsers, and firewalls, and AI-driven analytics orchestrating detection and response. Solid mesh lines replace the broken arrows of fragmented architectures.
Key takeaway: Visualize the mesh as a cohesive identity-aware hub connecting all defenses.
How Hybrid Mesh Defeats Credential Attacks
Hybrid Mesh isn’t just an architectural concept — it actively stops credential abuse. By combining prevention, remediation, and rapid response, it disrupts every stage of the attack lifecycle.
- Threat Prevention – One Detects, All Block
Prevention in a Hybrid Mesh means no tool works alone. A detection in one layer immediately triggers protection across all others.
- A phishing detection in email security propagates instantly to endpoints, firewalls, and SaaS.
- Infostealer malware detected on an endpoint automatically triggers protective policies across the mesh.
- Suspicious logins flagged by the identity provider (IdP) flow directly into network and endpoint controls.
- AI-driven continuous threat exposure management (CTEM) platforms feed internal exposures (e.g., vulnerabilities, misconfigurations) into the mesh, enabling prioritized, risk-based enforcement.
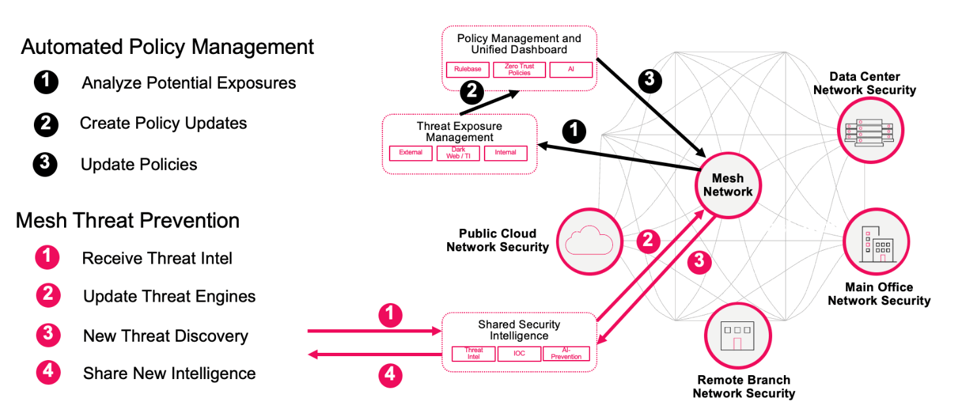
Figure 2: Hybrid Mesh threat prevention
Figure 2 shows proactive threat prevention across layers.
Key takeaway: Hybrid Mesh turns isolated detection into distributed prevention, guided by continuous risk scoring.
- Proactive Remediation – Closing Exposures
Hybrid Mesh with external risk management (ERM) discovers external credential exposures and enables real-time remediation, reducing enterprise risk and strengthening resilience.
In Hybrid Mesh:
- Leaked AWS keys found on GitHub trigger automated revocation.
- OAuth tokens detected on dark web markets are invalidated instantly.
- Service account credentials exposed in SaaS breaches are rotated automatically.
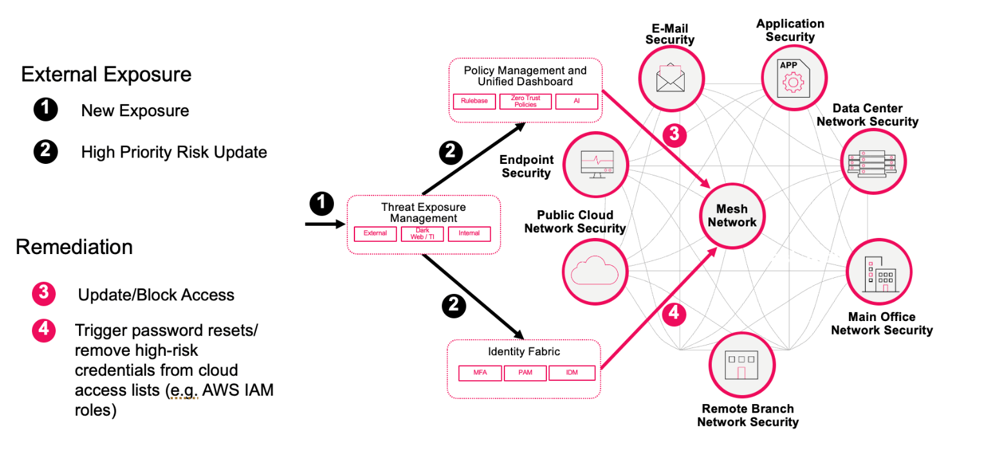
Figure 3: Hybrid Mesh proactive remediation
Figure 3 depicts rapid remediation of external exposures through automated workflows.
Key takeaway: Hybrid Mesh reduces months of exposure into minutes through automated workflows.
- Coordinated Detection & Response – Containing the Impact
Even with prevention and proactive remediation, some intrusions succeed. Hybrid Mesh responds by:
- Quarantining devices infected with malware.
- Microsegmenting networks to block lateral movement.
- Revoking tokens to cut off session hijacking.
- Enforcing just-in-time access for privileged accounts.
According to IBM’s 2025 Cost of a Data Breach Report, organizations with automation shortened containment by 98 days on average, saving millions in breach costs.
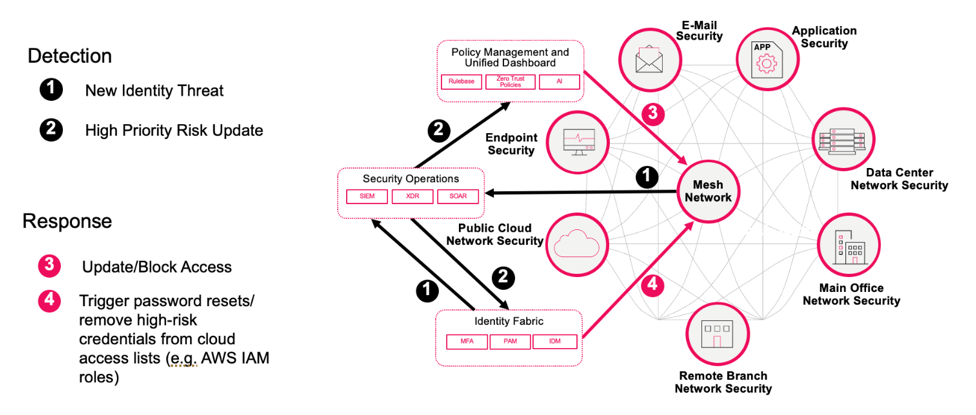
Figure 4: Hybrid Mesh coordinated response
Figure 4: Hybrid Mesh Coordinated Response
Figure 4 illustrates coordinated containment: isolating compromised devices and accounts in real time.
Key takeaway: Hybrid Mesh reduces attacker dwell time from months to minutes.
Real-World Relevance: Nx “s1ngularity” Supply-Chain Breach
In August 2025, attackers stole a software publishing token from Nx’s build system and used it to release compromised packages. When organizations downloaded these packages, they silently collected developer credentials and access keys, spreading quickly through development and build environments.
More than 2,300 credentials and secrets were stolen, giving attackers access to hundreds of private code repositories across many companies. This shows how one stolen credential can create a cascading supply-chain breach — and why organizations need an identity-aware Hybrid Mesh with threat exposure management to find exposed credentials early and revoke them automatically before attackers can move further.
Key takeaway: The Nx breach shows how a single stolen token can ripple through entire supply chains — and why early exposure detection and automated response are critical.
Conclusion
Credential abuse will remain the attacker’s preferred weapon. From phishing to OAuth token theft, adversaries exploit weak silos and delayed responses. But a Hybrid Mesh Architecture shifts the balance.
By unifying detection, enforcing consistent identity-aware policies, and automating response, it reduces risk, shortens dwell times, and empowers defenders. For CISOs, the imperative is clear: replace fragmented controls with a Hybrid Mesh to protect the enterprise at the speed attackers move.
Key takeaway: Identity is the new perimeter. Hybrid Mesh is the architecture that makes it defensible.
FAQ –
Q: What is a Hybrid Mesh?
It is a unifying security architecture where identity is a key anchor. Endpoint, mobile, browser, network, cloud, and SaaS defenses are interconnected to share context and enforce policies consistently.
Q: How does this differ from Zero Trust, CSMA or HMF alone?
Zero Trust defines the framework, CSMA ensures interoperability, and HMF provides network defense — Hybrid Mesh unites them with other security tools to orchestrate consistent enforcement across hybrid environments.
Q: How does risk management fit in?
CTEM feeds internal and external exposures (vulnerabilities, misconfigurations dark web leaks, GitHub secrets) into the mesh, enabling prioritized, automated containment.
Q: What does the Nx “s1ngularity” breach reveal about supply-chain credential risk?
A: It showed how a stolen build token can compromise entire supply chains. Attackers used it to publish malicious packages that harvested thousands of developer secrets from downstream environments. This underscores why organizations need an Identity-Aware Hybrid Mesh integrated with Threat Exposure Management to detect exposed credentials early, correlate risks, and trigger automated containment before attackers can move laterally.
Q: How can a CISO begin implementing this?
Start with MFA everywhere and credential hygiene. Connect tools to share identity context. Deploy CTEM platforms and introduce automation for credential incidents.
Q: What measurable benefits can be expected?
- Reduced misconfigurations
- Faster detection and response
- Shorter dwell times (IBM: 98 days faster containment with automation)
- Reduced SOC fatigue
- Lower breach costs
- Greater resilience against supply-chain attacks



