
A Continuing Cyber-Storm with Increasing Ransomware Threats and a Surge in Healthcare and APAC region
Highlights:
- The first 3 quarters of 2023 has witnessed a 3% uptick in average weekly global cyberattacks compared to the corresponding period in the previous year.
- The Global Healthcare sector faced an average of 1613 attacks per week, indicating a substantial 11% year-over-year surge.
- APAC was the most heavily attacked region with a substantial 15% YoY increase
- One in every 34 organizations globally encountered a ransomware attack attempt, marking a 4% increase compared to the same timeframe last year.
Navigating the Cyber Storm: A Global Snapshot by Check Point Research
As we step into October, the month dedicated to global cyber awareness, it is crucial to illuminate the evolving landscape of cyber threats that impact us all. Check Point Research’s latest report provides a comprehensive view of the storm brewing in the digital realm, specifically for the timeframe of Q1-Q3 of 2023. In 2023, global cyberattacks have seen a 3% uptick compared to last year’s figures, with the Healthcare sector particularly in the crosshairs, witnessing an 11% surge in attacks. Notably, one in every 34 organizations worldwide faced the chilling reality of a ransomware attempt, marking a 4% increase from the same period last year. Join us on this exploration of the cyber frontier, arming ourselves with insights to stay vigilant and secure in a world where the digital winds of change blow stronger each day. Welcome to October—the month we deepen our understanding of the cyber challenges we collectively face.
Overall global attacks
In 2023 so far, there was an 3% increase in the average weekly global cyber attacks compared to the same period last year. The average number of attacks per organization per week so far this year stands at 1200 attacks.
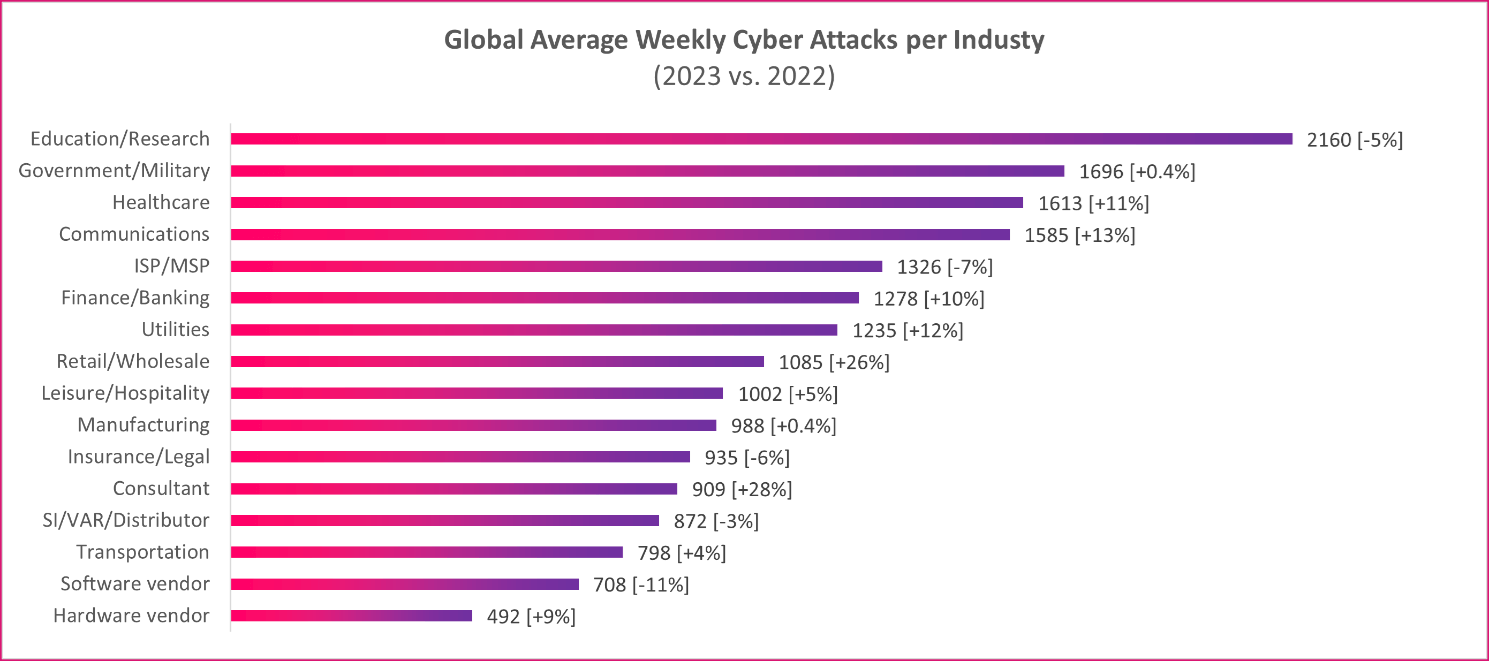
Global Attacks per Industry: Healthcare under attack
The Education/Research sector experienced the highest number of attacks, with an average of 2160 attacks per organization per week, marking a 5% decrease compared to the same period in 2022. The Government/Military sector was the second most attacked, with an average of 1696 attacks per week, which represents a 0.4% increase from the same period in the previous year, while the Healthcare sector followed closely behind, with an average of 1613 attacks per week, reflecting a significant YoY increase of 11%.
In a public statement, MCNA(Managed Care of North America) says it determined someone “was able to see and take copies of some information in our computer system between February 26, 2023 and March 7, 2023” . MCNA, a dental insurer, has been hit with the largest breach of health data in 2023, which affected more than 8.8 million Americans.
Another type of Health Scare – why we see many cyberattacks against hospitals?
Attacks on hospitals and healthcare institutions have become increasingly prevalent for several reasons:
- Rich Data Troves: Healthcare organizations store a treasure trove of sensitive information, including personal health records, financial data, and other personally identifiable information. Cybercriminals target this data for identity theft, financial gain, or even extortion.
- Critical Infrastructure: Hospitals are part of critical infrastructure, and disrupting their operations can have severe consequences. Cyber attackers may leverage this to extort ransoms or create chaos for political or ideological motives.
3. IoT Danger : Many health care organizations are using IoT, and there are large numbers of unmanaged IoT devices connected to the network. Each of these IoT devices is an entry point for hackers, making almost every hospital vulnerable to cyberattacks.
- Vulnerabilities in Legacy Systems: Many healthcare systems rely on legacy technology, which might not have robust cybersecurity measures in place. These outdated systems can be more vulnerable to exploitation, making them attractive targets.
- Limited IT Resources: Healthcare institutions often have limited resources allocated to cybersecurity, both in terms of budget and expertise. This makes them attractive targets as they may have weaker defenses compared to other industries.
- High Stakes, Low Tolerance: The nature of healthcare means that any disruption can have immediate and life-threatening consequences. Cybercriminals may exploit this urgency, knowing that healthcare providers are more likely to pay ransoms quickly to restore critical services.
- Supply Chain Vulnerabilities: The healthcare ecosystem involves various interconnected entities, including pharmaceutical companies, medical device manufacturers, and insurance providers. Cyber attackers may exploit vulnerabilities in these interconnected systems to gain access to sensitive healthcare data.
- Global Health Concerns: Events like global health crises or pandemics can create a sense of urgency and distraction, providing cover for cybercriminals to carry out attacks when attention is focused elsewhere.
Overall Attacks per Region: APAC witnessed a substantial 15% YoY increase
During 2023 so far, Africa experienced the highest average number of weekly cyberattacks per organization, with an average of 1987 attacks. This signifies a year-on-year increase of 6% compared to the same period in 2022. The APAC region also witnessed a substantial 15% YoY increase in the average number of weekly attacks per organization, reaching an average of 1963 attacks.
| Region | Avg. Weekly attacks per organization | YoY Change |
| Africa | 1987 | +6% |
| APAC | 1963 | +15% |
| Latin America | 1663 | +0.4% |
| Europe | 966 | -1% |
| North America | 939 | +5% |
1 out of every 34 organizations worldwide experienced an attempted ransomware attack
In 2023 so far, every week on average 1 out of every 34 organizations worldwide experienced an attempted ransomware attack, representing an increase of 4% compared to the same period last year.
Organizations in Africa and Latin America were most impacted by attempted ransomware attacks, with 1 in every 19 organizations on average experiencing such an attack every week.
North America showed the highest increase compared to last year with 25% compared to the same time in 2022.
| Region | Organizations Attacked | YoY Change |
| Latin America | 1 out of 19 | +22% |
| Africa | 1 out of 19 | +7% |
| APAC | 1 out of 20 | -8% |
| Europe | 1 out of 47 | +0.3% |
| North America | 1 out of 69 | +25%
|
Global Ransomware Attacks per Industry:
In 2023 so far, the Government/Military sector experienced the highest number of ransomware attacks, with 1 out of every 24 organizations impacted, marking a 11% decrease compared to the previous year. The Healthcare sector was the second most affected, with 1 out of every 25 organizations experiencing such attacks, representing an increase of 3% YoY. With a similar increase from last year, the Education/Research industry followed closely behind as the 3rd most impacted sector globally, with 1 out of every 27 organizations affected by attempted ransomware attacks.
It is also important to notice many of the top impacted industries include critical infrastructure and services, including the Utilities sector which is ranked 6th, but has a dramatic 26% increase in Ransomware impact in the past year.
| Industry | Organizations Attacked | YoY Change |
| Government/Military | 1 out of 24 | -11% |
| Healthcare | 1 out of 25 | +3% |
| Education/Research | 1 out of 27 | +3% |
| Finance/Banking | 1 out of 29 | +15% |
| ISP/MSP | 1 out of 33 | -9% |
| Utilities | 1 out of 34 | +26% |
| Communications | 1 out of 35 | +4% |
| Consultant | 1 out of 38 | +45% |
| SI/VAR/Distributor | 1 out of 42 | -2% |
| Transportation | 1 out of 46 | +22% |
| Manufacturing | 1 out of 47 | -14% |
| Retail/Wholesale | 1 out of 48 | -1% |
| Leisure/Hospitality | 1 out of 48 | +16% |
| Insurance/Legal | 1 out of 49 | +22% |
| Software vendor | 1 out of 62 | -3% |
| Hardware vendor | 1 out of 65 | +17% |
Ransomware continues to grow for several interconnected reasons:
- Lucrative Business Model: Ransomware has proven to be a profitable venture for cybercriminals. The ability to extort money from individuals, businesses, or even governments fuels its growth. The relative anonymity provided by cryptocurrencies makes it easier for attackers to receive payments without being traced.
- Sophisticated Techniques: Cybercriminals are constantly evolving their techniques. The use of advanced tactics, such as leveraging zero-day vulnerabilities and employing social engineering, allows them to bypass traditional security measures.
- Ransomware-as-a-Service (RaaS): The rise of Ransomware-as-a-Service platforms makes it easier for even less skilled individuals to execute ransomware attacks. This ‘plug-and-play’ model provides malicious tools and infrastructure, lowering the barrier to entry for aspiring cybercriminals.
- Exploiting Weak Cyber Hygiene: Many organizations, particularly smaller ones, may have inadequate cybersecurity measures in place. Exploiting weak passwords, unpatched systems, and insufficient employee training provides avenues for ransomware attackers to gain entry.
- Targeting Critical Infrastructure: Cybercriminals increasingly target critical infrastructure, including healthcare, energy, and transportation. These sectors are more likely to pay ransoms quickly to avoid disruptions that could have severe consequences.
- Insufficient Regulation: In some regions, regulations and laws around cybersecurity are not robust enough to deter attackers effectively. This lack of consequences further emboldens cybercriminals.
- Cryptocurrency Anonymity: The use of cryptocurrencies like Bitcoin for ransom payments provides a level of anonymity that traditional banking systems do not. This facilitates the financial transactions necessary for ransomware operations without easy traceability.
Practical advice: preventing ransomware and other attacks
Cyber Awareness Training
Phishing emails are one of the most popular ways to spread ransom malware. By tricking a user into clicking on a link or opening a malicious attachment, cybercriminals gain access to the employee’s computer and begin the process of installing and executing the ransomware on it. Frequent cybersecurity awareness training is crucial to protecting the organization against ransomware, leveraging their own staff as the first line of defence in ensuring a protected environment. This training should instruct employees on the classic signs and language that are used in phishing emails.
Up-to-Date Patches
Keeping computers up-to-date and applying security patches, especially those labelled as critical, can help to limit an organization’s vulnerability to ransomware attacks as such patches are usually overlooked or delayed too long to offer the required protection
Utilize Better Threat Prevention
Most ransomware attacks can be detected and resolved before it is too late. You need to have automated threat detection and prevention in place in your organization to maximize your chances of protection, including scanning and monitoring of emails, and scanning and monitoring file activity for suspicious files.
AI has become an indispensable ally in the fight against cyberthreats. By augmenting human expertise and strengthening defense measures, AI-driven cybersecurity solutions provide a robust shield against a vast array of attacks. As cybercriminals continually refine their tactics, the symbiotic relationship between AI and
cybersecurity will undoubtedly be crucial in safeguarding our digital future.
Anti-Ransomware Solutions
Anti-ransomware solutions monitor programs running on a computer for suspicious behaviors commonly exhibited by ransomware, and if these behaviors are detected, the program can take action to stop encryption before further damage can be done.
Robust Data Backup
The goal of ransomware is to force the victim to pay a ransom in order to regain access to their encrypted data. However, this is only effective if the target actually loses access to their data. A robust, secure data backup solution is an effective way to mitigate the impact of a ransomware attack.



