
Check Point Shares Analysis of Qakbot Malware Group
On August 29, 2023, the FBI announced it dismantled the Qakbot (also referred to as Qbot) multinational cyber hacking and ransomware operation, impacting 700,000 computers around the world – including financial institutions, government contractors and medical device manufacturers. The Qakbot malware infected victims via spam emails with malicious attachments and links. It also served as a platform for ransomware operators. Once infected, the victims’ computer became part of Qakbot’s larger botnet operation, infecting even more victims.
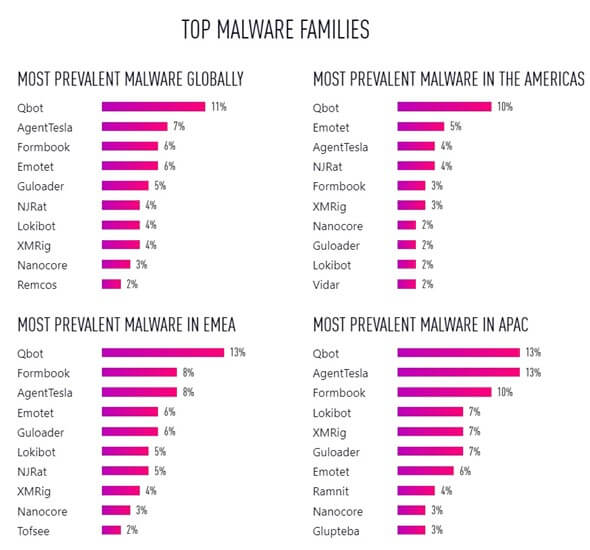
Check Point Research (CPR) has tracked Qakbot and its operations for years. This year, Qakbot was highlighted in the 2023 Mid-Year Security Report as the most prevalent malware, globally.
What is Qakbot?
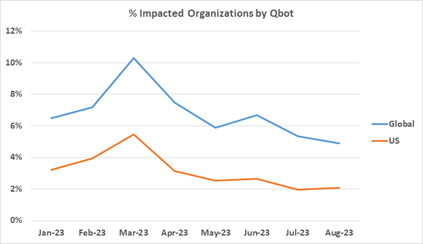
Operated by Eastern European cybercriminals, Qakbot has been in operation since 2008. It is the most commonly detected malware, with 11% of corporate networks worldwide impacted in 1H’23. However, since March 2023, CPR has observed a marked decrease in Qakbot attacks worldwide. For example, the United States experienced a 38% decrease in Qakbot attacks in August 2023 vs March 2023. Globally, there was a 48% decrease in the same time period.
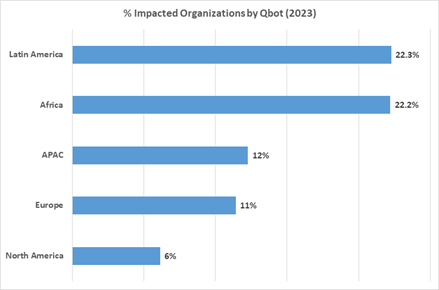
So far in 2023, Latin America is the most impacted region by Qakbot, followed closely by Africa.
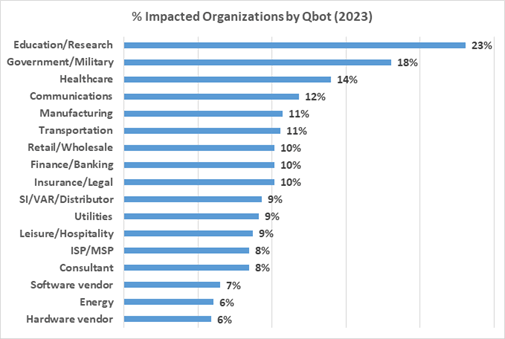
In 2023, Qakbot targeted education/research organizations and government/military, followed by healthcare.
Qakbot is especially tricky: it is a multipurpose malware, akin to a Swiss Army knife. It allows cybercriminals to directly steal data (credentials to financial accounts, payment cards, etc) from PCs, while also serving as an initial access platform to infect victims’ networks with additional malware and ransomware. Qakbot is mainly distributed by phishing emails and is highly adaptive and flexible, allowing it to bypass security measures. It uses file types including OneNote, PDF , HTML, ZIP, LNK and more to infect machines.
How to Prevent Ransomware Attacks
While cyberattacks are on the rise, prevention is possible. Check Point recommends
- Investing in phishing awareness campaigns so employees can easily identify and report phishing attempts. Phishing emails continue to be the #1 successful tactic of hackers.
- Staying up-to-date with security patches to ensure computers always have the latest protection.
- Leveraging anti-ransomware solutions that continuously monitor for suspicious behaviors to take action and stop encryption before further damage can be done.
For a more detailed analysis of Qakbot, visit the CPR blog.








