Highlights
· Old Vulnerabilities Still Pose Risks: Despite being several years old, CVEs from 2017 and 2018 in Microsoft Word and Excel remain active threats in the cybersecurity landscape. Examples include CVE-2017-11882, CVE-2017-0199, and CVE-2018-0802.
· Widespread Use by Cybercriminals: These vulnerabilities are exploited by well-known malware such as GuLoader, Agent Tesla, Formbook, and others. APT groups also got on the list, with Gamaredon APT being a notable example. They target lucrative sectors like finance, government, and healthcare, indicating a strategic approach by attackers.
· Challenges in Detection: Despite their age, these MalDocs can evade detection due to their sophisticated construction and the use of various tricks to bypass security measures.
Persistent Threats from Old Vulnerabilities
In the ever-evolving world of cybersecurity, new threats emerge daily. However, some old vulnerabilities, specifically in Microsoft Word and Excel, continue to pose significant risks. These include CVE-2017-11882, CVE-2017-0199, and CVE-2018-0802, which are still effectively used in cyberattacks despite not being zero-day vulnerabilities.
Usage by Notable Malware
These vulnerabilities have been instrumental in spreading various infamous malware families. For instance, Dridex malware exploited CVE-2017-0199 in 2017, while GuLoader and Agent Tesla used CVE-2017-11882 in subsequent years. One more example includes Gamaredon APT exploiting CVE-2017-0199 in 2023. These attacks primarily targeted sectors with high profit potential, such as banking, government, and healthcare.
Detection Difficulties
Despite being known for several years, these MalDocs often slip through security nets. They employ various techniques to avoid detection, including encryption, peculiar URLs, and shellcode obfuscation. This makes them particularly challenging for automated security systems to detect and neutralize.
Insight on Attacked Industries and Countries
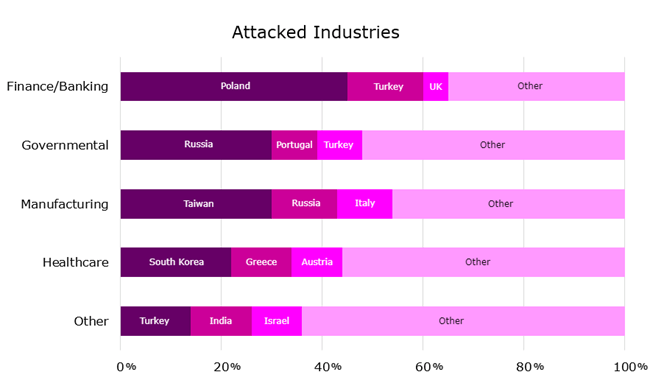
Attacked Industries
The use of MalDocs leveraging old CVEs has been notably prevalent in industries where the potential for data exploitation and financial gain is significant. These industries include:
- Finance/Banking: Given the sensitive financial data, this sector is a prime target for cybercriminals. Malware attacks often aim to steal credentials, manipulate transactions, or gain direct access to financial resources.
- Governmental Agencies: These attacks typically focus on extracting confidential state information, disrupting public services, or espionage.
- Healthcare: With access to personal health information and critical infrastructure, this sector is vulnerable to ransomware and data theft.
The MalDocs have been designed to deliver payloads that are on the top of prevalent malware lists, indicating a strategic and targeted approach by attackers. These payloads are often part of more extensive campaigns with specific objectives, be it financial gain, data theft, or disruption of services.
Attacked Countries
The geographical spread of these attacks is also notable. While the report may not provide specific details on each country affected, it’s observed that countries with significant economic or geopolitical importance are more likely to be targeted. This can be due to the higher value of the data or systems in these regions or their significance in global affairs.
Highlighted Payloads
The payloads delivered by these MalDocs include various types of malware, each designed for specific purposes:
- Banking Trojans like Dridex: Aimed at stealing banking credentials.
- Downloaders like GuLoader: Used to install additional malicious software.
- Info stealers like Agent Tesla and Formbook: Designed to extract sensitive information like login credentials and personal data.
Lures in Different Attack Campaigns
Nature of Lures
The lures used in these campaigns are cleverly crafted to entice the target into opening the maldoc. These lures can be:
- Emails Mimicking Legitimate Communications: Appearing as if they’re from trusted sources, such as banks or government agencies.
- Topical Themes: Leveraging current events or trending topics to spark curiosity or urgency.
- Personalized Content: Tailored to the target’s interests or activities, based on gathered intelligence.
Tricks to Fool Automated Sandboxes
Despite the age of these CVEs, MalDocs have evolved to bypass modern security defenses, particularly automated sandboxes, through various techniques:
- Obfuscation of Malicious Code: Using techniques like encryption and encoding to hide the true nature of the code.
- Use of Legitimate-Looking URLs and Domain Names: To avoid raising red flags in automated systems.
- Shellcode with Junk Instructions: Including irrelevant code or commands to mislead automated analysis tools.
- Timing-Based Execution: Some malicious actions are delayed or triggered by specific user interactions, which may not be replicated in a sandbox environment.
- Remote Templates and Links Without Extensions: Making it less obvious what the contacted site will reveal, complicating the detection for security solutions.
- Document Formatting Tricks: Such as requiring the user to “enable editing” or “enable content,” which can bypass some automated security measures that don’t interact with documents as a user would.
- Embedding Malicious Payloads in Non-Executable File Formats: Like Word or Excel documents, which are less likely to be flagged as dangerous compared to executable files.
Evolving Tactics
These techniques demonstrate the adaptability of cybercriminals in the face of advancing cybersecurity measures. The use of well-crafted lures and sophisticated evasion tactics makes it challenging for automated systems to keep up, necessitating a combination of advanced detection technologies and heightened user awareness to effectively combat these threats.
In conclusion, while the CVEs in question are not new, their continued exploitation underscores the need for ongoing vigilance in cybersecurity practices. Understanding the targeted industries, countries, and the evolving nature of these attacks is crucial for developing effective defense strategies against these persistent threats.
Conclusion and Recommendations
The continued relevance of these old vulnerabilities highlights the importance of vigilance in cybersecurity. To mitigate these risks, it is essential to:
– Keep operating systems and applications updated.
– Be cautious of unexpected emails with links, especially from unknown senders.
– Enhance cybersecurity awareness among employees.
– Consult security specialists for any doubts or uncertainties.
Check Point customers remain protected against the threat described in this research.
Check Point Threat Emulation and Harmony Endpoint provide comprehensive coverage of attack tactics, file-types, and operating systems and protect against the type of attacks and threats described in this report.
Against CVE-2017-11882:
- CVE-2017-11882.gen.TC.*
- CVE-2017-11882.TC.*
- HEUR:Exploit.MSOffice.CVE-2017-11882..TC.
Against CVE-2017-0199:
- CVE-2017-0199..TC.
- CVE-2017-0199..TC.
- CVE-2017-0199.TC.*
- HEUR:Exploit.MSOffice.CVE-2017-0199.gen.TC.*
- Maldoc_cve-2017-0199.*
Against CVE-2018-0802:
- CVE-2018-0802.gen.TC.*
- CVE-2018-0802.gen.TC.*
- CVE-2018-0802.TC.*
- HEUR:Exploit.MSOffice.CVE-2018-0802.gen.TC.*









