
Top Zero Trust Platforms Evaluated by Miercom: Check Point Ranks #1
Implementing a Zero Trust security posture is an expected best practice, but platforms can differ considerably in security effectiveness, ease-of-use, and breadth of capabilities. Miercom, a leading independent network and security testing firm, evaluated the top five security platforms to compare each vendor’s performance for common Zero Trust enterprise use cases.
Check Point achieved top ratings across all categories in the Zero Trust Platform Assessment.
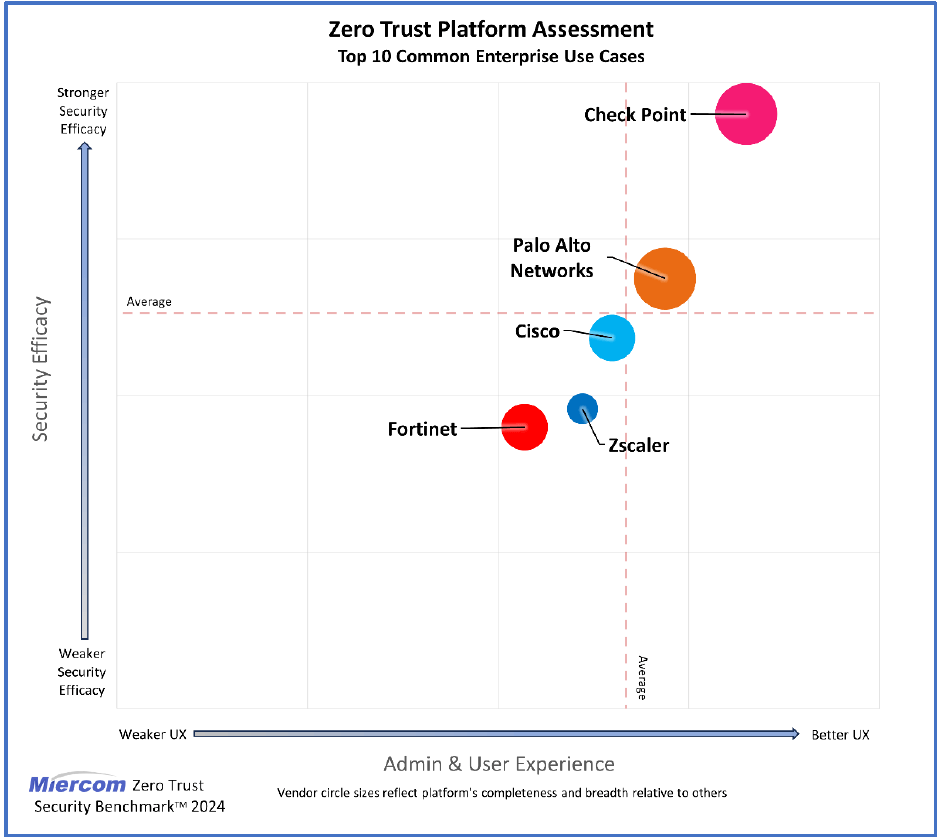
X-axis: Admin & User Experience / Y-axis: Security Efficacy
Vendor circle sizes reflect platform Completeness & Breadth relative to other vendors
What is Zero Trust?
A Zero Trust security architecture is designed to reduce cybersecurity risk by eliminating implicit trust within an organization’s IT infrastructure. This model dictates that even those within an organization’s security perimeter must be verified. Access to corporate resources is granted or denied based upon the user’s role and permissions within the organization.
Verification is augmented through several measures, including access management, multi-factor authentication, and continuous controls, such as Zero-Trust Network Access (ZTNA).
Zero Trust is relevant in the face of remote users working outside the traditional network perimeter, the use of cloud-based applications, and the increase in stolen credentials resulting from data breaches. Zero Trust also empowers security teams to isolate, secure, and control every device on the network.
A comprehensive Zero Trust solution also enables organizations to block infected devices from accessing corporate data and assets, including employees’ mobile devices and workstations, IoT devices and Industrial Control Systems.
Zero Trust Platforms: Put to the Test
Miercom’s evaluation focused on common security policy use cases that enterprises face daily.
The report aligns with real-world security requirements and provides a meaningful benchmark for Zero Trust capabilities. The use cases that Miercom evaluated are outlined below.
- URL Categories Access Restriction – Platforms were evaluated on access control to social media platforms, including the ability to fine-tune control settings for specific circumstances.
- Concurrent Administrators – Operational collaboration was assessed by verifying if multiple administrators could manage simultaneous requests across a centralized management system as well as across branch offices. Common issues, such as conflicting or overlapping policies, were evaluated.
- Cloud Service Provider Integration – Integration with cloud providers was assessed with a focus on enabling administrative access control to database servers. These servers require dynamic policy updates to ensure seamless access is maintained despite frequent changes.
- Delegated Management – Security management role granularity and security were assessed by testing the ability for branch administrators to manage localized access control and URL filtering policies. This exercise evaluated the ability to decentralize certain admin policies without affecting centrally managed policies.
- Malicious Website Protection – Protections against malicious web pages (including HTML & PDF files) were evaluated to test the policy’s redundancy and effectiveness. This evaluation identified which vendor offers the most user-friendly and efficient solution for preventing the execution of zero-day ransomware files.
- Phishing Protection – Miercom evaluated the ease-of-use for implementing protective measures, success rate in effectively blocking access to phishing websites based on admin-enacted rules, and ability to educate end users on the dangers of phishing.
- Troubleshooting False-Positives – Vendors were challenged to locate blocking logs and configure exceptions. This exercise’s goal was to permit previously blocked traffic that was erroneously stopped by an intrusion prevention system (IPS).
- Email Protection – Protection against email phishing (including QR code phishing) was assessed. This included testing the user-friendliness of the solution, and its ability to empower users to recover emails that were wrongly identified as phishing threats (false positives) without needing intervention from an administrator.
- Clientless Zero Trust Network Access – This ZTNA use case evaluated the ability to accommodate secure remote access from personal and unmanaged devices. This included establishing a policy on the SASE environment, enabling a connection to the internal enterprise server and using strict access control based on posture checks.
- Remote User Browser Interface –Miercom assessed the ability to implement SSL Inspection along with Threat Prevention to oversee and secure web traffic. This includes downloading various file types and sizes from SharePoint, followed by internet speed testing to evaluate the stability and throughput of their secure connection.
The Results: Check Point Leads
Check Point achieved the top ratings in all categories, by leading in functionality, ease-of-use, and security effectiveness for enterprise policy management tasks.
Check Point’s Infinity Platform delivers AI-powered, enterprise-grade security across the data center, network, cloud, branch office and remote users. It provides unified threat management and visibility across the entire estate via a single pane of glass dashboard.
The Check Point Infinity Platform distinguished itself in Miercom’s benchmark through:
Superior Platform Capabilities
Check Point’s platform enabled completion of each use case in under half the time required by others. For enterprises, this can translate into thousands of staff-hours saved annually.
Exceptional User Experience
Check Point provides streamlined operations with fewer configuration steps than other vendors, reducing the risk of misconfigurations. Ease-of-use is a critical win for operations teams.
Industry-Leading Zero Trust Security Effectiveness
Check Point achieved a 3.8 out of 4 score, surpassing all others in security efficacy.
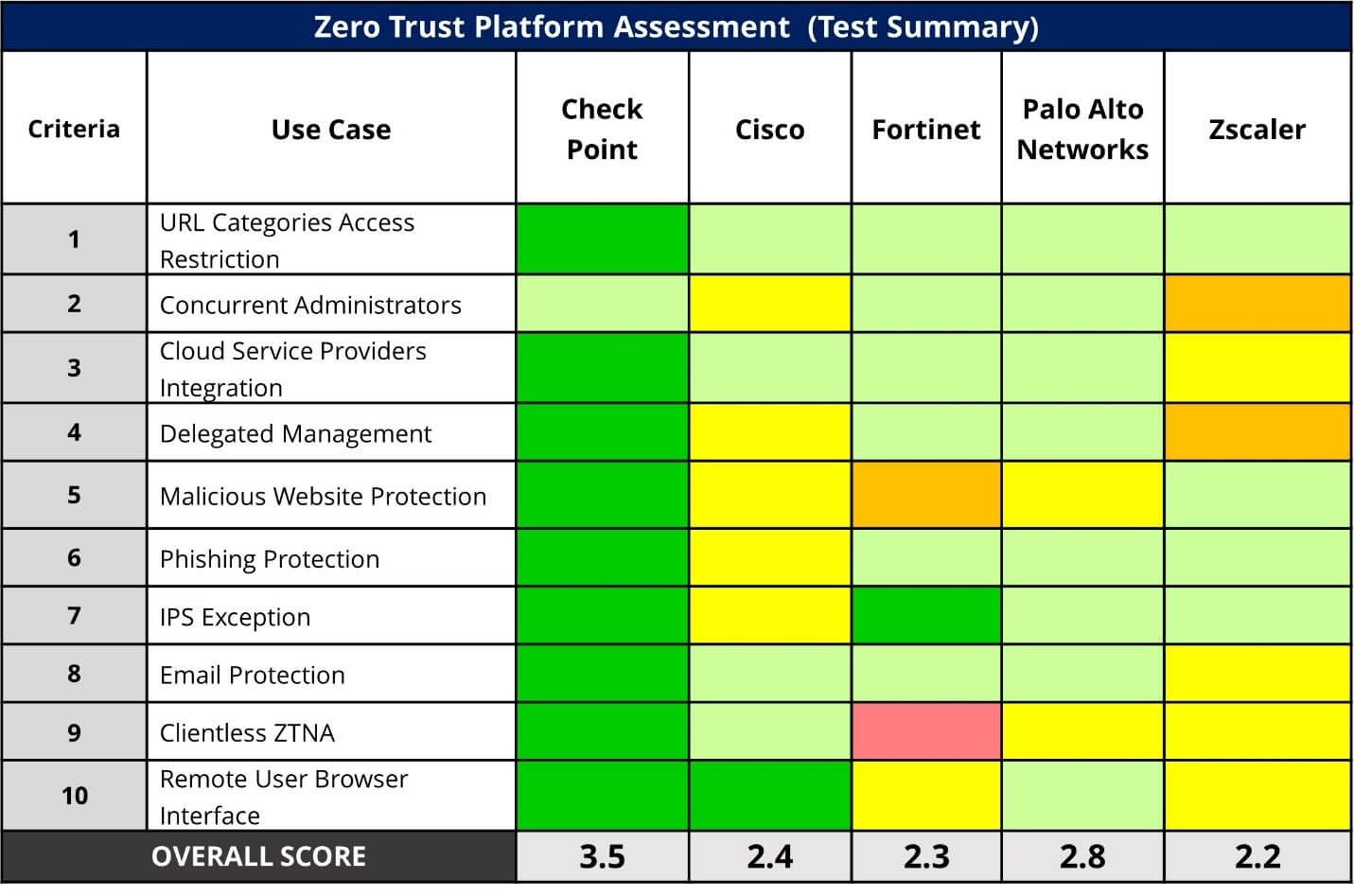
Check Point significantly outscored the other vendors by achieving a 3.5 (out of 4) overall score vs. an average 2.4 score for the combined four other vendors in the Miercom Zero Trust Platform Assessment. Check Point also achieved a security efficacy score of 3.8 (out of 4) score, surpassing all others.
This Zero Trust Platform recognition follows Check Point’s earlier success in Miercom’s 2024 Next Generation Firewall Benchmark Report, in which Check Point delivers an industry-leading 99.8% block rate for Zero+1 Day malware threats.
Learn how each vendor scored in Miercom’s real-world enterprise use cases, along with detailed assessments. See how Check Point outperformed the competition.



