
Unlocking the Power of In-Context Emulation in Malware Sandboxing
In the cyber security world, malware analysis is crucial for identifying and neutralizing threats. Attackers constantly evolve their methods, and defenders must stay ahead with advanced tools. One such tool is sandboxing, a controlled environment where suspicious files are executed and observed safely.
At Check Point, our Threat Emulation blade’s new feature “In-Context Emulation”, improves malware detection by replicating real-world environments, addressing some of the toughest detection challenges.
What is In-Context Emulation?
Traditional sandboxing runs files in isolation, which helps identify basic malicious behavior. However, modern malware often requires specific files, interactions, or system configurations to activate fully. This is where In-Context Emulation shines.
Instead of analyzing files in isolation, it moves all contents of an archive to a virtual environment, simulating a more realistic execution scenario.
By copying the entire archive file into the sandbox and opening it there, In-Context Emulation allows malware to interact with all its components, such as executables, scripts, and libraries, as it would on a real system.
This approach helps identify malicious behavior that may not be triggered in isolated sandboxes where files are analyzed separately.
In-Context Emulation is particularly effective for detecting complex or multi-stage malware attacks, as it reveals how different files within an archive interact with one another.
For example, it can expose self-extraction routines, the activation of embedded malicious code, or dependencies between different components that are necessary for the malware to function fully.
This allows for a more thorough detection of sophisticated threats, improving the chances of uncovering hidden or evasive malware that would otherwise go undetected.
By providing a more realistic environment for malware to run in, In-Context Emulation enhances detection capabilities, offering a deeper level of analysis compared to traditional sandboxing methods.
Below are key ways that In-Context Emulation exposes common methods that attackers use to hide malware among seemingly innocuous files or with other evasive conditions.
- Improved DLL Side-Loading Detection: Attackers often exploit DLL side-loading to run malicious code. In-Context Emulation accurately simulates these conditions, enabling the detection of such techniques, even when malware hides in trusted applications.
- Accurate Analysis of Complex Dependencies: Many malware types rely on specific files or executables. By ensuring all dependencies are present during emulation, analysis is more complete and accurate, with fewer false negatives.
- Better Detection of Multi-Stage Payloads: Some malware executes in stages, making it hard to detect in standard sandboxes. In-Context Emulation simulates the entire lifecycle to catch threats that would otherwise go unnoticed.
- Context-Aware Behavioural Analysis: By simulating the actual environment, the sandbox provides deeper insights into how malware interacts with systems, including attempts to modify settings, establish persistence, or exploit system processes.
Case Study: Uncovering an Undetected Info-Stealer Using In-Context Emulation In a recent analysis, we encountered a particularly deceptive malware sample sent via email as a ZIP file named Examplefile.pdf.zip. At first glance, the file’s name suggests it is a PDF document, a tactic commonly employed by attackers to deceive users into opening the file. However, within the ZIP file, the real payload was an executable named Examplefile.pdf.exe, a clear attempt to exploit the familiarity of PDF files and bypass basic examination.
Examplefile.pdf.exe (Figure 1) had zero detections and Examplefile.pdf.zip (Figure 2) had only one detection on VirusTotal, as shown in the screenshots below.
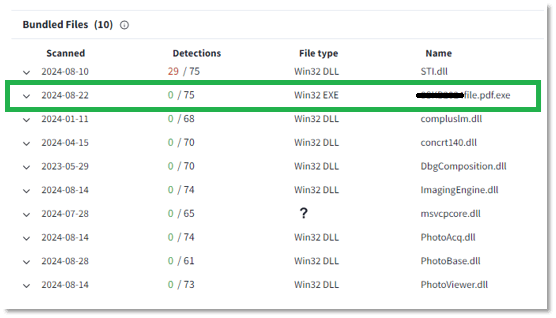
Figure 1: Files inside the ZIP file, executable has 0 detections
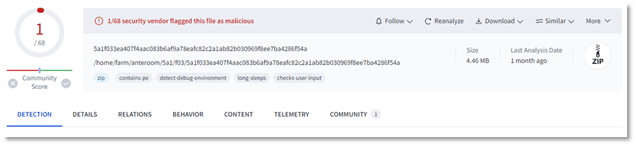
Figure 2: VirusTotal low detection
But the deception didn’t stop there. The archive also contained several DLL files, as shown below.
Among these, all were benign except for one: STI.dll. This malicious DLL played a crucial role in the attack, loaded by Examplefile.pdf.exe using DLL side-loading techniques. STI.dll then acted as a loader for a shellcode into memory, which we subsequently dumped from memory using our sandbox. This file, identified as 400000.wmplayer.exe, does not exist in VirusTotal at all.
Further automatic analysis, including the application of YARA rules to the dumped files generated by the sandbox, revealed that this file was not just any piece of malware, it was a variant of the infamous FormBook info stealer.
Understanding the DLL Loading Order in the Attack Chain
An important aspect of this attack is how Examplefile.pdf.exe leverages the DLL side-loading technique to load the malicious STI.dll from the ZIP file rather than the legitimate STI.dll files typically located in C:\Windows\System32\sti.dll and C:\Windows\SysWOW64\sti.dll.
In Windows, when an application loads a DLL, it follows a specific order to search for the DLL file. This order is crucial to understanding how attackers can manipulate the system to load a malicious DLL instead of a legitimate one. The typical search order for loading DLLs is:
- The directory from which the application is loaded: This is the first location Windows checks. If a DLL with the same name as the one requested by the application is found here, it will be loaded, regardless of any legitimate versions located elsewhere.
- The system directory (System32 or SysWOW64): If the DLL is not found in the application’s directory, Windows then searches these directories.
- The Windows directory: If the DLL still isn’t found, Windows searches its main directory.
- The current directory: Windows checks the current working directory.
- Directories listed in the PATH environment variable: Finally, Windows searches any additional directories specified in the PATH variable.
In this attack, Examplefile.pdf.exe loads the STI.dll located within the same directory (the directory where the executable resides) due to this search order. This is how the attacker ensures that the malicious STI.dll is loaded instead of the legitimate one in the system directories.
By placing the malicious DLL in the same location as the executable, the attacker effectively bypasses the security measures that would otherwise protect the system from unauthorized DLLs. This strategy is particularly effective in evading detection, as the system sees the loading process as legitimate, given the standard DLL search order.
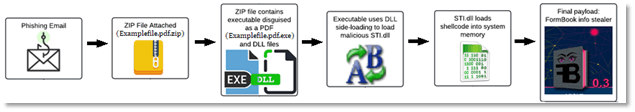
Figure 3: Attack Chain
About FormBook
FormBook is a notorious info-stealer that has been circulating in the wild for several years. It’s primarily designed to capture sensitive information from infected systems, including keystrokes, clipboard data, and browser credentials. Once collected, this data is exfiltrated to a command-and-control server controlled by the attacker. FormBook is often distributed via phishing emails, malicious attachments, and compromised websites, making it a significant threat to both individuals and organizations.
What makes FormBook particularly dangerous is its ability to remain undetected on infected systems for extended periods. It employs various evasion techniques, including code obfuscation, anti-debugging measures, and memory-only execution, to avoid detection by traditional antivirus solutions.
In this case, the in-context emulation allowed us to uncover the full extent of the attack, from the initial deception to the final payload. This level of detailed analysis underscores the importance of using advanced tools like In-Context Emulation in the fight against sophisticated malware.
This case study highlights the practical benefits of In-Context Emulation in identifying and mitigating sophisticated threats that would otherwise go undetected.
Conclusion
In-context emulation represents a significant advancement in the field of malware analysis. By accurately replicating the real-world environment in which malware operates, this feature enhances the depth and accuracy of our analysis, enabling us to detect even the most complex threats. Combined with the inherent advantages of sandbox technology, In-Context Emulation is a powerful tool in the ongoing fight against cyber threats. At Check Point, we are committed to leveraging the latest innovations to protect our clients and stay ahead of emerging threats.
Protections
Check Point customers remain protected against the threats described in this research.
Check Point Threat Emulation provide comprehensive coverage of attack tactics, file-types, and operating systems and protect against the type of attacks and threats described in this report.
Check Point customers using Quantum and Harmony products with activated Threat Emulation are protected against the campaigns detailed in this report.
To learn about Check Point threat prevention, schedule a demo or a free security checkup to assess your security posture.



