Check Point Threat Alert: BlackEnergy Trojan
ByCheck Point Research Team
Executive Summary
- BlackEnergy malware has been around since 2007, first appearing as a simple DDoS tool. In 2014, it made a comeback as a highly sophisticated and customized malware, featuring support for proxy servers and a wide range of system operations.
- Observed targets on 2014 are mostly Ukrainian governmental institutes but also include those from multiple other countries including Poland and Germany. Attacks against Georgia in 2008 which used the malware, the recent Russo-Georgian confrontation, and the current political situation between Russia and Ukraine, lead researchers to believe that the ‘Quedagh’ group is the APT behind the malware.
- On Wednesday, December 23, 2015, more than 1 million Ukraine citizens in the Ivano-Frankivsk region had no electricity for several hours, due to an attack based on BlackEnergy’s destructive ‘KillDisk’ component.
Attack Timeline
- BlackEnergy was originally created in 2007 as a relatively simple Trojan, infecting machines to establish a bot network and conduct DDoS attacks against Russian sites.
- In 2010, BlackEnergy version2 was spotted in the wild. It featured Rootkit techniques and enabled plugins which allowed the malware to be used by an APT group to steal banking information and function as a click-fraud tool.
- A newer BlackEnergy variant, referred to as version3, was identified in 2014. It featured significant upgrades such as additional espionage modules, support for proxy servers, and the ability to run not only on Windows, but also on Linux, ARM-based, MIPS-based, and some Cisco networking devices. Furthermore, it contained a KillDisk component designed to destroy system functions, and was capable of infecting SCADA Industrial Control Systems.
- The third variant’s targets included mainly Ukraine government institutions. The ‘Quedagh’ group, possibly of Russian origin, was the suspected operator.
- On December 23, 2015, the BlackEnergy Trojan’s destructive component – WIN32/KillDisk – was deployed for the first time. The targets were multiple industrial systems in Ukrainian electrical companies. It is believed that the malware successfully infected those systems by sending messages from a fake email account, allegedly owned by a government office. These messages contained Office document with an embedded macro, which dropped the malware when run by unsuspecting users.
Check Point Protections
Check Point protects our customers from BlackEnergy variants with our IPS, Anti-Virus and Anti-Bot blades, based on protections released between June 2013 and January 2016.
- Microsoft Windows OLE Remote Code Execution (MS14-060)
- This IPS protection detects and blocks attempts to exploit CVE-2014-4114, a remote code execution vulnerability in Microsoft Object Linking and Embedding (OLE) technology.
- The vulnerability is known to be in wide use by the BlackEnergy Trojan.
- Microsoft Word RTF listoverridecount Memory Corruption (MS14-017)
- This IPS protection detects and blocks attempts to exploit CVE-2014-1761, a memory corruption vulnerability which exists in multiple versions of Microsoft Word.
- The vulnerability is also known to be used by the BlackEnergy Trojan
- Anti-Bot Signatures
- 8 Network signatures are currently active in our Anti-Bot
- 6 URL signatures are currently active in our Anti- Bot Blade.
- AV Reputation and Hash signatures
- 182 hash signatures are currently active in our Anti-Virus Blade.
Check Point Observation & Guidance
- Check Point has noted many attack attempts worldwide by known variants of the BlackEnergy Trojan.
- Check Point recommends activating the above IPS protections in Prevent mode.
- Check Point identified attacks directed at machines in Thailand, Europe and the US.
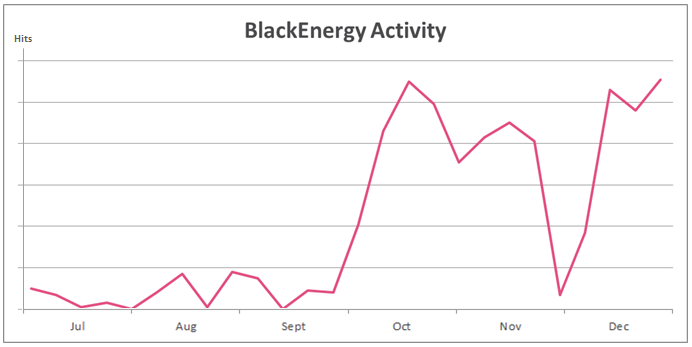
- Attack rates in the last six months appear in the chart below. The numbers represent the number of attacks per week.
References
- Technical Analysis – https://blog.bit9.com/2014/11/18/blackenergy-trojan-finds-new-life-in-variants/
- ICS_CERT Alert – https://ics-cert.us-cert.gov/alerts/ICS-ALERT-14-281-01B
- Attribution and Targeting – https://www.f-secure.com/documents/996508/1030745/blackenergy_whitepaper.pdf
- Recent Attack – http://www.welivesecurity.com/2016/01/04/blackenergy-trojan-strikes-again-attacks-ukrainian-electric-power-industry/
You may also like
Shifting Attack Landscapes and Sectors in Q1 2024 with a 28% increase in cyber attacks globally
Recurring increase in cyber attacks: Q1 2024 saw a marked ...
Not So Private After All: How Dating Apps Can Reveal Your Exact Location
Check Point Research (CPR) recently analyzed several popular dating applications ...
Agent Tesla Targeting United States & Australia: Revealing the Attackers’ Identities
Highlights Check Point Research (CPR) uncovered three recent malicious campaigns ...
Beyond Imagining – How AI is actively used in election campaigns around the world
Key Findings AI is already extensively utilized in election campaigns ...