
What do the inkblots tell you? Check Point Researchers Unveil “Rorschach,” previously unseen, fastest ever Ransomware
Highlights:
- Check Point Research (CPR) and Check Point Incident Response Team (CPIRT) detected a previously unnamed ransomware strain, now dubbed “Rorschach,” deployed against a US-based company.
- Highly customizable with technically unique features previously unseen in ransomware, Rorschach is one of the fastest ransomware ever observed.
- The ransomware was deployed using DLL side-loading of Palo Alto Network’s Cortex XDR, a signed commercial security product, in a loading method not commonly used to load ransomware. The information was properly disclosed to Palo Alto Networks.
Everyone sees something different
Check Point Research (CPR) is always on guard for new and emerging cybersecurity attacks and trends. Today, CPR and Check Point Incident Response Team (CPIRT) are drawing attention to a new, more sophisticated ransomware strain that was previously unnamed. Dubbed “Rorschach” by our researchers, this ransomware was used in an attack against a US-based company.
What makes Rorschach stand out from other ransomware strains is its high level of customization and its technically unique features that have not been seen before in ransomware. In fact, Rorschach is one of the fastest ransomware strains ever observed, in terms of the speed of its encryption.
Interestingly, Rorschach was deployed using DLL side-loading of Palo Alto Network’s Cortex XDR Dump Service Tool, a signed commercial security product. This loading method is not commonly used to load ransomware, and thus, it reveals a new approach taken by cybercriminals to evade detection. The vulnerability that allowed the deployment of Rorschach was properly disclosed to Palo Alto Networks.
What did we find?
While responding to a ransomware case against A US-based company, our CPIRT recently came across a unique ransomware strain deployed using a signed component of Palo Alto Network’s Cortex XDR, a commercial security product. Unlike other ransomware cases, the threat actor did not hide behind an alias and appears to have no affiliation to any of the known ransomware groups. Those two facts, rarities in the ransomware ecosystem, piqued CPR’s interest and prompted us to thoroughly analyze the newly discovered malware.
Previously unseen speed and rarely seen features among ransomware
Throughout its analysis, the new ransomware exhibited unique features. A behavioral analysis of the new ransomware suggests it is partly autonomous, spreading itself automatically when executed on a Domain Controller (DC) while it clears the event logs of the affected machines. In addition, it’s extremely flexible, operating not only based on a built-in configuration but also on numerous optional arguments which allow it to change its behavior according to the operator’s needs. While it seems to have taken inspiration from some of the most infamous ransomware families, it also contains unique functionalities, rarely seen among ransomware, such as the use of direct syscalls.
The ransomware note sent out to the victim was formatted similarly to Yanluowang ransomware notes, although other variants dropped a note that more closely resembled DarkSide ransomware notes (causing some to mistakenly refer to it as DarkSide). Each person who examined the ransomware saw something a little bit different, prompting us to name it after the famous psychological test – Rorschach Ransomware.
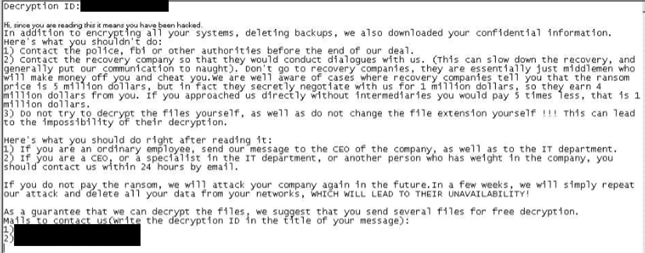
Ransom note from Rorschach.
For the full analysis of Rorschach visit research.checkpoint.com
Check Point Customers remain protected against Rorschach Ransomware
Harmony Endpoint provides runtime protection against ransomware with instant automated remediation, even in offline mode. In case of an anomaly caused by a ransomware, Harmony Endpoint anti-ransomware and Behavioral Guard capabilities identify, block and remediate the full attack chain.
When running on a machine infected with the Rorschach ransomware, Harmony Endpoint Anti-ransomware detected the encryption process in different folders, including modifications made to Harmony Endpoint ‘honeypot’ files. It ran a ranking algorithm that provided a verdict identifying the process as a ransomware.
The attack tree process was calculated and Harmony Endpoint killed all malicious processes to block the attack. The remediation component then deleted all encrypted files, including the malicious processes, and restored them to their original state, using the system backup.
To help investigate the attack, Harmony Endpoint provides a full forensic report including an attack tree and complete MITRE mapping.
As seen in this forensic report, Harmony Endpoint detected the attack, classified it as ransomware and terminated 100% of all malicious processes. During the remediation, it deleted or quarantined 100% of the affected files and restored them to their original form (except for the honeypot files).
Thanks to these capabilities, the attack is blocked without affecting business continuity.
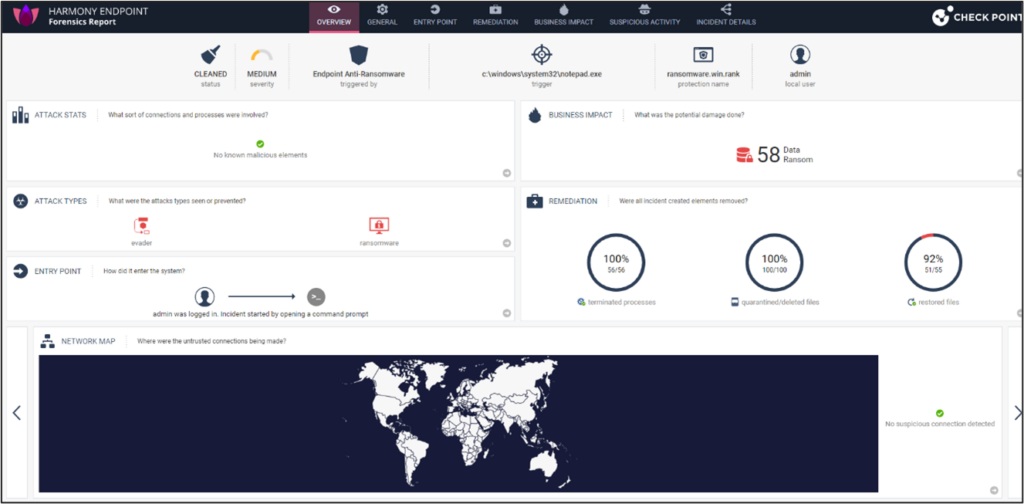
Harmony Endpoint anti-ransomware provides additional advanced capabilities against ransomware attacks including sophisticated volume-based encryption and wiper attacks. It also prevents the use of legitimate tools as ransomware agents.
Protect your endpoints from ransomware with Harmony Endpoint. We invite you to schedule a private demo or start a free trial









