
Secure and Scalable Cloud Networking with Oracle Cloud Intra-VCN Routing and Check Point CloudGuard
When it comes to cloud computing, security is one of the most important considerations. Moreover, even the best cloud security must be easy and intuitive to deploy, configure, use and maintain.
Customers of Oracle Cloud Infrastructure (OCI) can streamline their security by using Check Point CloudGuard’s integration with OCI’s new intra-VCN routing feature. This OCI service enables network traffic to be routed within the virtual cloud network, instead of through the public internet, allowing for increased control and visibility.
In this blog post, we’ll discuss the benefits of the integration between CloudGuard and OCI intra-VCN routing and how it can help to improve your Oracle cloud security.
Register here to join my deep-dive hands-on webinar, “Oracle Cloud Security technical deep-dive: Insights and Innovations”.
Scalable network security with Intra-VCN routing
Intra-VCN routing allows communication between virtual cloud networks (VCNs) within the same region. This provides greater control and security for traffic that is not exposed to the public internet. With this, you can confidently and securely build applications spanning multiple VCNs, ensuring that traffic is isolated from the public internet.
Inserting a Check Point CloudGuard Network Security gateway for traffic inspection reduces VCN sprawl by centralizing security. You deploy different application tiers into separate subnets and route the traffic through a central CloudGuard security gateway, giving your users efficient, simple and scalable networking with industry-leading security.
How does the integration work?
Before this integration, VCN routing was managed by OCI through the control plane or “routing” and a database. This inherent VCN functionality performed direct local routing between two endpoints without user administration. OCI implemented three important and related feature enhancements to enable user control and ease of use,:
- Intra-VCN routing: admins can set routes for intra-VCN traffic between two different subnets in the same VCN.
- Internet and NAT gateway ingress routing: the ability to create routes for inbound public traffic to your VCNs through an Internet or NAT gateway.
- Service gateway ingress routing enhancement: create routes for a service gateway to route traffic from OCI services to destinations inside your VCN.
These enhancements allow more configuration flexibility when controlling traffic. User-defined routes can now be defined between subnets in the same VCN. Also, local peering gateways (LPG) or dynamic routing gateways (DRG) can be the target of an intra-VCN route rule and thus allow directing of traffic to a centralized security VCN for inspection by a security gateway.
The following diagram shows an example design where the Security VCN and the Internal VCN are connected by a DRG. The web and database subnets are in separate subnets of the same VCN. Intra-VCN route rules allow the subnets to reach each other within the VCN with the DRG as the target. The DRG forwards the traffic to the security VCN to the CloudGuard security gateways for inspection and then sends it to its destination. Internet ingress traffic coming from the Ingress Gateway transits through the security gateways, is inspected and sent to its destination. This design shows a single Internal VCN but many VCNs can share connectivity through the DRG in the same way.
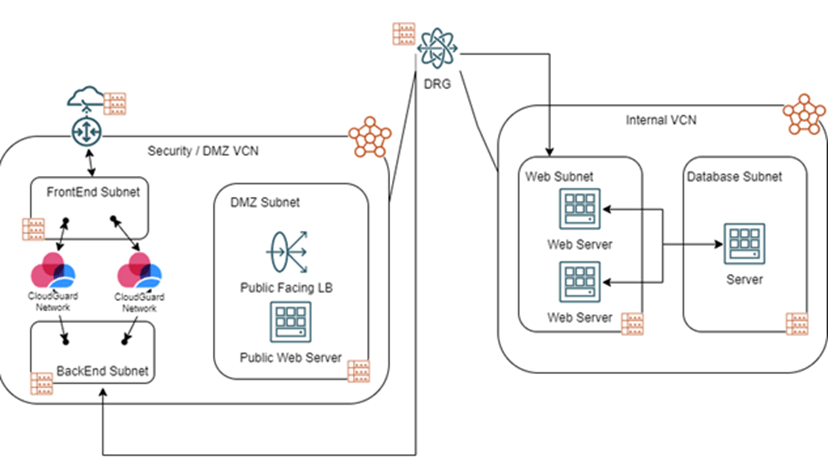
Reference architecture for deploying Check Point CloudGuard
Intra-VCN routing for greater cost-effectiveness and easier implementation
Before intra-VCN routing when the subnets were in the same VCN, direct routing did not allow the insertion of a security gateway as an intermediate hop in the routing. This direct routing complicated the routing tables and created much more difficult configurations to create and manage.
The solution was to leverage inter-VCN routing by deploying into different VCNs. The security gateway could then be routed through the inter-VCN route table. This was a reasonable solution for a few VCNs, but the exponential complexities made managing the infrastructure difficult as your deployment scales.
With intra-VCN routing, you can apply the most effective architecture by leveraging security hubs for inspection. The intra-VCN routing allows application traffic in different subnets to be routed to the Security VCN security gateways. The routing targets are inserted and managed centrally, which is a more cost-effective design. Intra-VCN routing makes OCI network management easier and the implementation of CloudGuard Network Security more effective.
Best practices for intra-VCN and ingress routing with Check Point and OCI
We recommend leveraging a centralized “hub-and-spoke” architecture as a best practice when designing secure network solutions.
With this design concept, you will route traffic between different parts of the network using intra-VCN routing. Thus, all traffic within a single VCN will be isolated from traffic in other VCNs and the public Internet.
This architecture ensures that traffic remains within your OCI environment and is not exposed to any potential malicious actors. When traffic passes from East to West or North (Internet) to South (applications VCN), it will transit through a CloudGuard Network Security gateway where it will be inspected. Additionally, access control rules will control authorized access.
Additionally, Check Point’s advanced features such as Threat Emulation and Threat Extraction, anti-malware scanning, and Application Control through deep packet inspection, prevent malware and malicious actors from gaining entry to your cloud networking.
Using recommended architectures and industry-leading security solutions from Check Point, you can ensure that your networks remain safe and secure. In addition, with the range of ingress routing options available through intra-VCN routing, you can easily route traffic from other cloud providers or services hosted by OCI into your VCN of choice. The end result is an efficient, fast, scalable and CloudGuard-protected OCI network.
Next Steps
Now that you’re familiar with intra-VCN routing and its various benefits, it’s time to get started on your own intra-VCN and ingress gateway routing implementation protected by CloudGuard.
This step-by-step article will help you set up an effective, efficient and cost-conscious intra-VCN solution. The article includes configuring the correct ports, routing protocols, and security gateway policies to protect your data from malicious actors. Finally, once everything is configured correctly, test your setup by ensuring the traffic flows properly between your subnets.
Intra-VCN routing with CloudGuard Network Security is the best way to add the best security and the fastest, most efficient VCN networking to your OCI deployment. Using CloudGuard, you can maximize your security while taking advantage of the scalability and flexibility that OCI offers.
Most importantly, if you’d like to join my deep-dive hands-on webinar, “Oracle Cloud Security technical deep-dive: Insights and Innovations”, please register here. I will present these new innovations and show how they are important and relevant, together with related architectures. I will also dive into a few use cases and review important resources that should be leveraged.
If you would like to schedule a deep-dive personalized workshop around CloudGuard or best practices for secure migration, please fill in the form here and a cloud security architect will contact you to discuss your needs and schedule next steps.
If you are in the process of planning your migration to the cloud, please fill in the form to schedule a demo, and a cloud security expert will help to understand your needs.



