
Check Point Research Alerts: Financially Motivated Magnet Goblin Group Exploits 1-Day Vulnerabilities to target Publicly Facing Servers
Key Highlights:
– Rapid Exploitation of 1-Day Vulnerabilities: Threat actor group Magnet Goblin’s hallmark is its ability to swiftly leverage newly disclosed vulnerabilities, particularly targeting public-facing servers and edge devices. In some cases, the deployment of the exploits is within 1 day after a POC is published, significantly increasing the threat level posed by this actor.
– Diverse Cyber Arsenal: The group employs a sophisticated set of tools including NerbianRAT, a cross-platform RAT for Windows and Linux, and WARPWIRE, a JavaScript credential stealer. This diverse malware suite enables a wide range of cyber attacks, from data theft to sustained access within compromised networks.
– Urgent Need for Proactive Defense: The emergence of Magnet Goblin underscores the critical importance of robust cybersecurity practices. Organizations must prioritize timely patching, advanced threat detection, and cyber security awareness to defend against the agile tactics of such threat actors.
In the ever-evolving battlefield of cybersecurity, a new adversary has emerged, showcasing remarkable agility in exploiting digital vulnerabilities. Known as Magnet Goblin, this financially motivated threat actor has swiftly adapted to leveraging “1-day vulnerabilities” — security flaws disclosed but not yet patched — to infiltrate publicly facing servers. This detailed exploration delves into the tactics, targets, and implications of Magnet Goblin’s operations, urging a re-evaluation of current security postures.
The targeting of Magnet Goblin, as of most of the cybercrime groups, is opportunistic, but in this case, our research showed us that US seemed to be most targeted by the group; in our research, we saw examples of several targets in the US, from the medical, manufacturing and energy sector.
Understanding the Threat
Magnet Goblin distinguishes itself by its rapid adoption of newly disclosed vulnerabilities, notably targeting platforms such as Ivanti Connect Secure VPN, Magento, Qlik Sense, and possibly Apache ActiveMQ. The group’s swift manoeuvring to incorporate exploits into their arsenal — at times within a day of a proof of concept being published — signifies a profound threat to digital infrastructures worldwide.
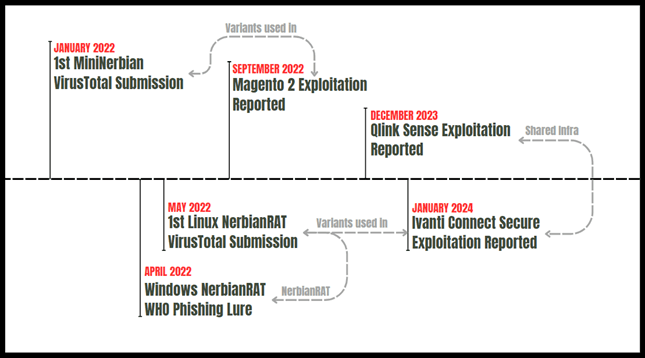
Figure 1 – Past Magnet Goblin campaigns.
Tactics and Techniques
At the heart of Magnet Goblin’s strategy lies the exploitation of 1-day vulnerabilities, primarily in edge devices and public-facing services. By doing so, they manage to stay ahead of security patches, gaining unauthorized access to sensitive systems. Their toolkit includes a novel Linux version of malware known as NerbianRAT and WARPWIRE, a JavaScript credential stealer, showcasing the actor’s sophisticated approach to cyber intrusion.
Ivanti Exploitation Campaign
While tracking the recent waves of Ivanti exploitation, we identified a number of activities leading to the download and deployment of an ELF file which turned out to be a Linux version of NerbianRAT. This cluster of activity, also described in a Darktrace report, was characterized by the download of a variety of payloads from an attacker-controlled infrastructure.
Among the downloaded payloads are a variant of the WARPWIRE JavaScript credential stealer, a NerbianRAT Linux variant, and Ligolo, an open-source tunneling tool written in GO.
After initial exploitation of the servers by the group due to these unpatched vulnerabilities, the threat actor deployed sophisticated malware which exfiltrates sensitive information from the victims.
The Arsenal of Magnet Goblin
Magnet Goblin’s malware suite is as diverse as it is dangerous. NerbianRAT, a cross-platform Remote Access Trojan (RAT), allows for comprehensive control over compromised systems, while MiniNerbian, a smaller Linux backdoor, offers a stealthier avenue of infiltration. Additionally, the group employs remote monitoring and management tools like ScreenConnect and AnyDesk, further complicating the cyber security landscape.
Mitigation and Response
The emergence of Magnet Goblin underscores the critical need for robust cyber security measures. Organizations must prioritize patch management to address vulnerabilities promptly, enhance monitoring to detect early signs of intrusion, and foster cyber security awareness among their teams. Proactive defense strategies, including the deployment of advanced threat detection systems and regular security audits, are essential to counteract the evolving tactics of threat actors like Magnet Goblin.
Check Point Customers Remain Protected against the threats described in this report.
Check Point IPS protections in our Next Generation Firewall are updated automatically. Check Point Harmony Endpoint provides comprehensive endpoint protection at the highest security level and protects with the following:
RAT_Linux_Nerbian_A
RAT_Linux_Nerbian_B
RAT_Linux_Nerbian_C
RAT_Linux_Nerbian_D
Conclusion
As we navigate the complexities of the digital age, the activities of groups like Magnet Goblin serve as a stark reminder of the perpetual arms race between cybercriminals and defenders. Staying informed about the latest threats and reinforcing our digital defenses are imperative steps in safeguarding our cyber landscape against these agile adversaries.
The accompanying visual encapsulates the urgency and complexity of the threat posed by Magnet Goblin, illustrating the need for vigilant and comprehensive cybersecurity measures to protect against such adept and versatile actors.









