Check Point Research Report: Iranian Hacktivist Proxies Escalate Activities Beyond Israel
Highlights:
· Expanded Cyber Frontline: Recent developments in cyber warfare reveal a shift in the activities of Iranian hacktivist proxies. Initially concentrated on Israel, these groups are now extending their cyber operations to include targets in other countries, with a particular emphasis on the United States.
· Emerging Narrative from Iranian Hacktivist Groups: Analysis shows that at least four Iranian hacktivist groups are now actively claiming to be targeting U.S. entities. This shift is characterized by a mix real successful attacks, reuse and reclaim of old attacks and leaks, and what seems to be exaggerated and falsified claims.
· Strategy of Iranian Affiliated Groups: Groups such as CyberAv3ngers and Cyber Toufan appear to be adopting a narrative of retaliation in their cyberattacks. By opportunistically targeting U.S. entities using Israeli technology, these hacktivist proxies try to achieve a dual retaliation strategy—claiming to target both Israel and the U.S. in a single, orchestrated cyber assault.
The landscape of cyber warfare is evolving, particularly in the context of the recent war between Israel and Hamas. This evolution has led to an increase in cyber operations against both Israeli and non-Israeli targets, particularly in the United States. Iranian hacktivist groups are at the forefront of this change, combining actual cyber successes with repeated and sometimes exaggerated claims.
These developments parallel an increase in tensions between Iran and the U.S., reminiscent of traditional physical-world conflict methods, as we see Iran employing proxies to target the US. Notable among the Iranian-affiliated groups are CyberAv3ngers and Cyber Toufan. Their operations often involve claims of retaliation against U.S. entities for using Israeli technology, reflecting a strategy of dual retaliation.
As tensions in the Middle East continue, the likelihood of ongoing cyberattacks by these Iranian affiliated proxies’ groups, particularly against U.S. targets, remains high. This trend represents a significant evolution in the nature of cyber warfare, transcending traditional geopolitical boundaries. Following are examples of Iran affiliated groups that are targeting the US:
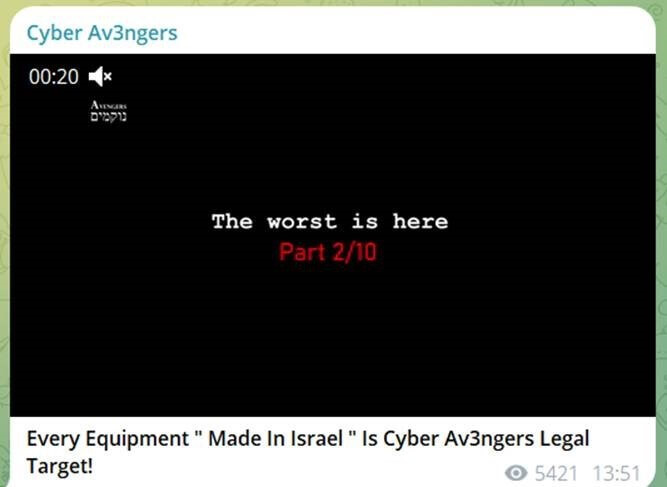
CyberAv3ngers
Cyber Av3ngers is an Iranian Government Islamic Revolutionary Guard Corps (IRGC) affiliated hacktivist group, which has operated for a long time on and off, through different telegram channels focusing on Israeli targets.
Their focus includes critical infrastructure sectors, with a history of both actual and overstated accomplishments. Recently, they have been implicated in attacks on U.S. infrastructure using vulnerabilities in specific Israeli-made equipment.
According to CISA alert, since at least November 22, 2023, this group started compromising default credentials in Unitronics devices across victims in multiple U.S. states, with a focus on critical infrastructure organizations. The IRGC-affiliated cyber actors left a defacement image stating, “You have been hacked, down with Israel. Every equipment ‘made in Israel’ is CyberAv3ngers legal target.”
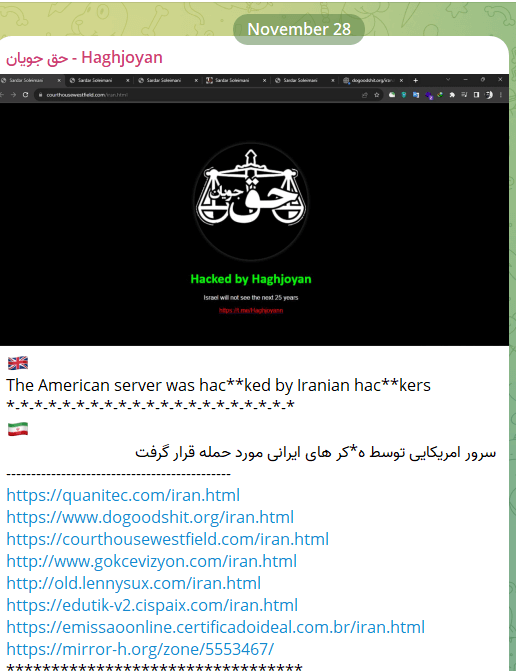
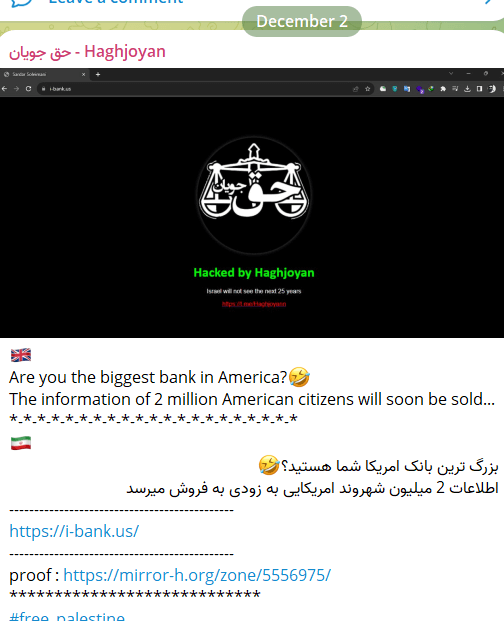
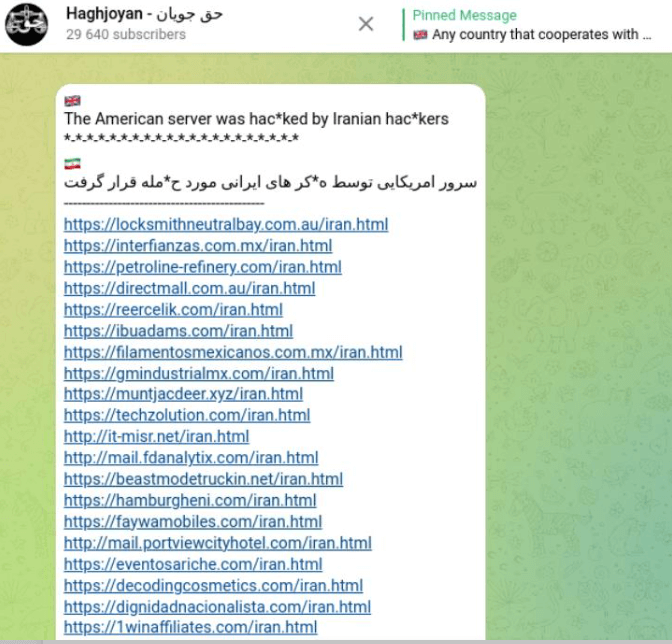
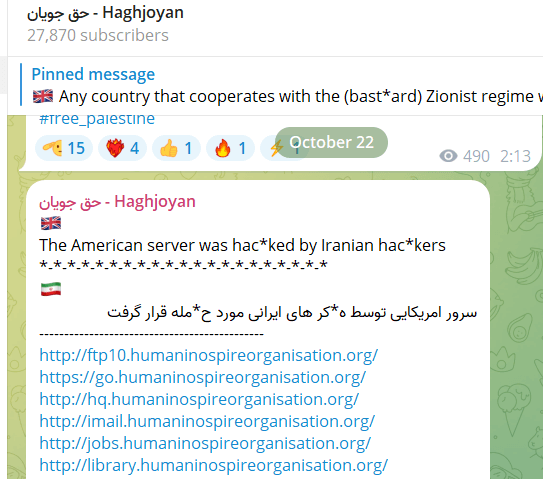
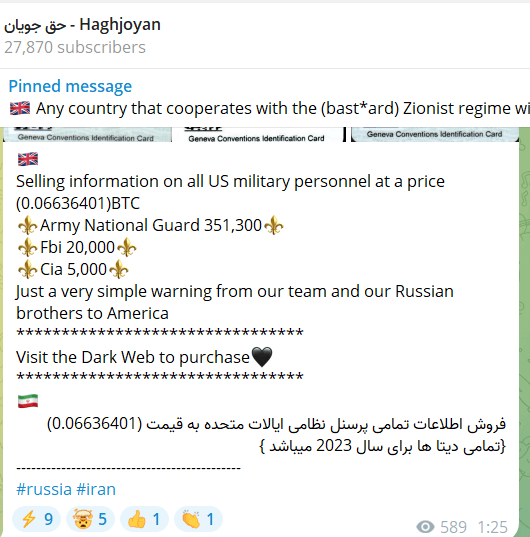
Haghjoyan
This group emerged at the beginning of the war, initially targeting Israel before shifting focus to the U.S. This group’s activities have included data leaks and website defacements.
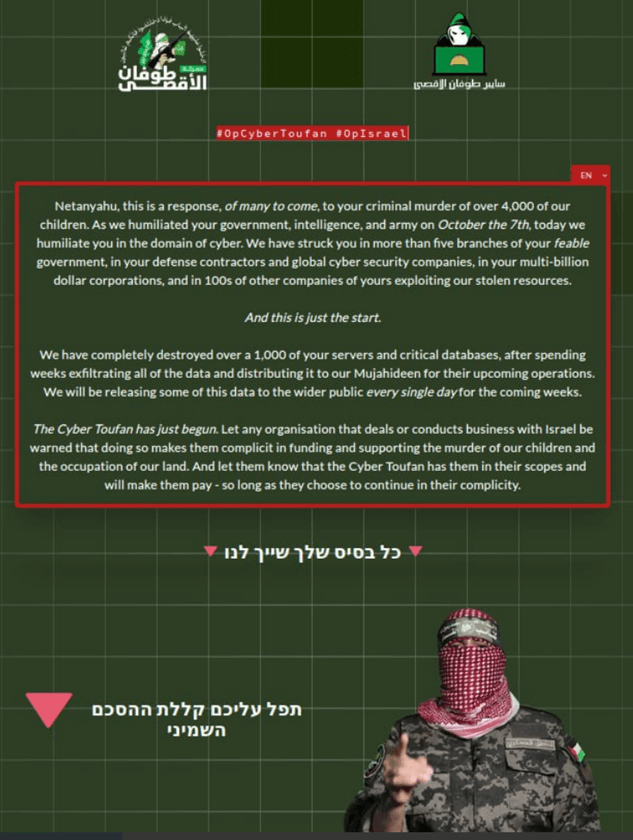
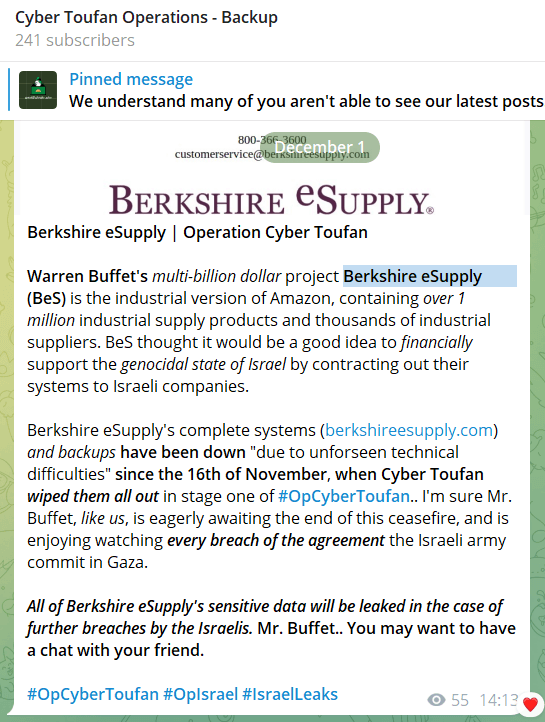
CyberToufan Group
Initially focused on Israeli organizations, this group recently has claimed responsibility for targeting Berkshire eSupply , an American. company, allegedly due to their use of Israeli IT infrastructure.
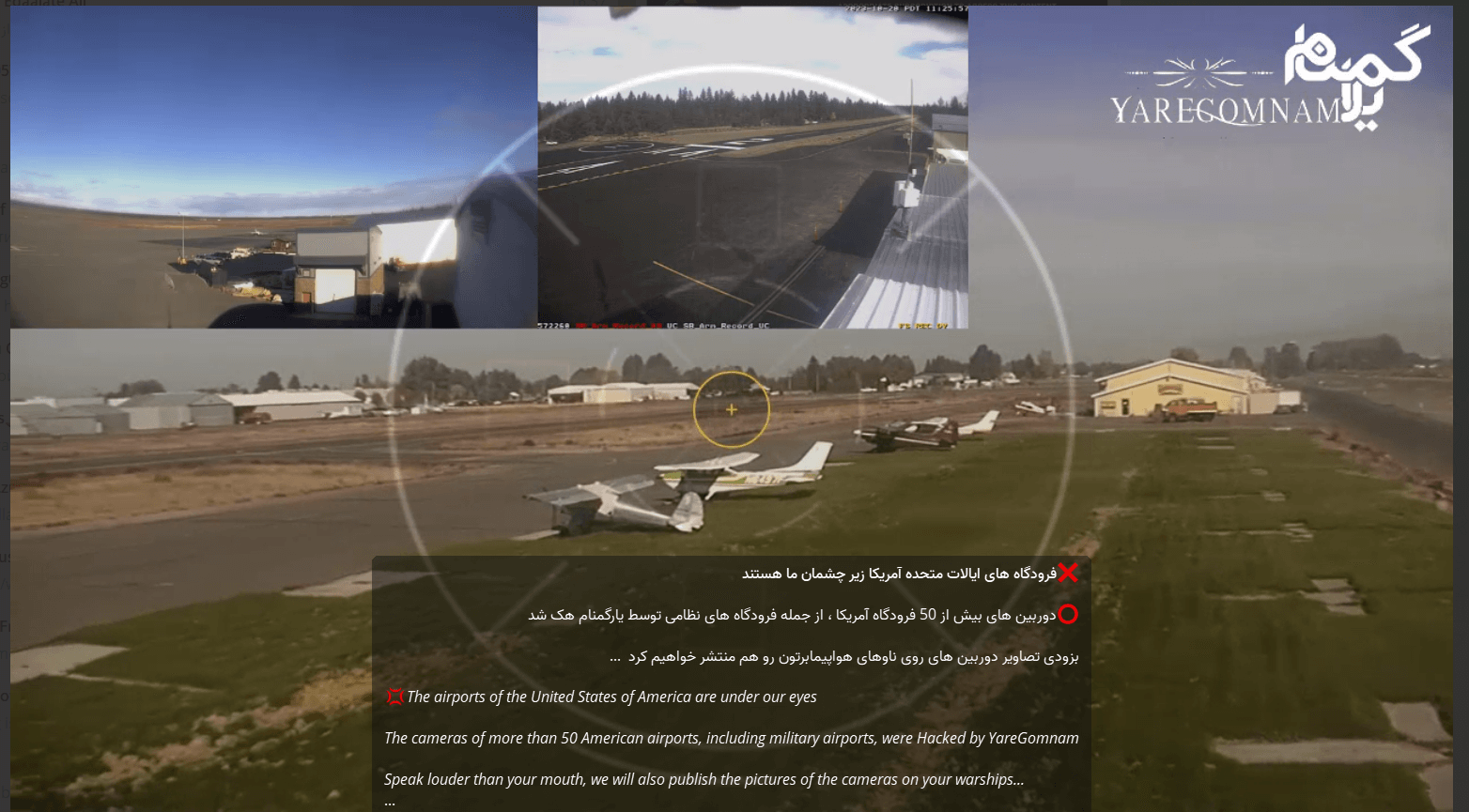
YareGomnam Team
A pro-Iranian group active since 2018, recently claimed attacks on U.S. infrastructure, including pipeline and electrical systems, and allegedly hacked CCTV systems at numerous U.S. airports.
During the last week, the group has accelerated its anti-Western messaging and on December 2nd ,attackers from the group claimed to have hacked CCTV cameras of more than 50 US airports.

Disclaimer: The details regarding the attacks presented in this blog are relayed exactly as reported by the hacktivist groups. It is important to note that Check Point Researchers cannot independently verify each claim, and the accuracy of the attacks as described by the hackers is not confirmed.
Check Point Research advise organizations to stay alert and maintain a prevention-first approach to cyberattacks
1. Ensure Robust Security: Confirm the use of strong, non-default passwords for all PLC and HMI devices to fortify your organization’s defense against potential cyber threats.
2. Prioritize Patch Management: Establish a consistent and proactive patching routine for all internet-facing servers, with a specific emphasis on securing Microsoft Exchange servers. Regular updates are crucial to bolstering system resilience.
3. Eradicate Default Password Risks: Mitigate risks by changing all default passwords associated with internet-facing servers and edge devices. This simple yet effective measure adds an extra layer of protection against unauthorized access.
4. Enhance Authentication Measures: Strengthen your organization’s security posture by implementing multi-factor authentication across sensitive sections of both your network and Operational Technology (OT) environments. This additional layer of verification significantly reduces the risk of unauthorized access and safeguards critical assets.
5. Utilize better threat prevention: Most attacks can be detected and resolved before it is too late. You need to have automated threat detection and prevention in place, in your organization to maximize your chances of protection.
- Scan and monitor emails. Emails are a common choice of cybercriminals executing phishing schemes, so take the time to scan and monitor emails on an ongoing basis, and consider deploying an automated email security solution to block malicious emails from ever reaching users.
- Scan and monitor file activity. It is also a good idea to scan and monitor file activity. You should be notified whenever there is a suspicious file in play—before it becomes a threat.