
Decrypting Danger: Check Point Research deep-dive into cyber espionage tactics by Russian-origin attackers targeting Ukrainian entities
Highlights:
-
Gamaredon, a distinct APT player in Russian espionage, stands out for its large-scale campaigns primarily targeting Ukrainian entities.
-
The USB worm, LitterDrifter, reveals a global impact with potential infections in countries like the USA, Vietnam, Chile, Poland, Germany, and Hong Kong, expanding beyond its original targets.
-
Recently deployed by Gamaredon, LitterDrifter is a VBS-written worm designed to spread through USB drives, demonstrating the group’s evolving tactics in maintaining a flexible and volatile infrastructure.
Key Findings on LitterDrifter:
LitterDrifter, Gamaredon’s latest tool in its cyber arsenal, is a VBS-written worm with dual functionalities.
Its primary objectives are automatic spreading over USB drives and establishing communication with a flexible set of command-and-control servers. This strategic design aligns with Gamaredon’s overarching goals, allowing the group to maintain persistent access to its targets.
USB Worm’s Global Reach:
While Gamaredon primarily targets Ukrainian entities, the nature of the LitterDrifter worm introduces a global element to its operations. Indications of possible infections have been observed in countries such as the USA, Vietnam, Chile, Poland, Germany, and even Hong Kong. This suggests that, like other USB worms, LitterDrifter may have spread beyond its originally intended targets, posing a broader threat to cybersecurity worldwide.
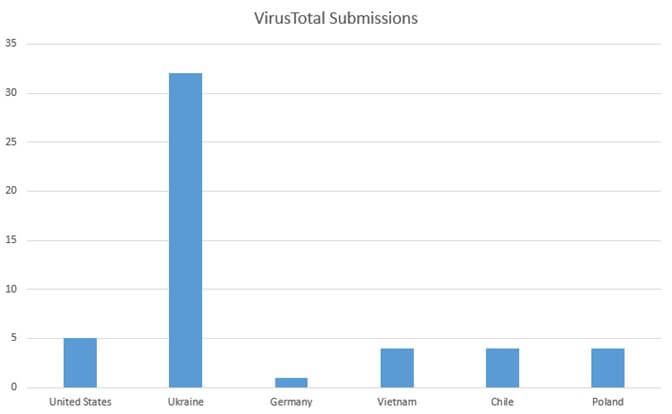
Distribution of victims’ per country
Background:
In the ever-evolving landscape of cybersecurity threats, certain adversaries stand out for their audacity and persistence. Gamaredon, also known as Primitive Bear, ACTINIUM, and Shuckworm, is a prominent player in the realm of Russian espionage, with a unique focus on Ukrainian entities. While many Russian cyber espionage groups operate in the shadows, Gamaredon is notably conspicuous in its large-scale campaigns, leaving a trail that cybersecurity researchers are keen to dissect. In this blog post, we turn our attention to one of Gamaredon’s tools – the notorious USB-propagating worm, LitterDrifter.
Gamaredon’s Affiliation:
Gamaredon distinguishes itself by targeting a wide array of Ukrainian entities, showcasing a relentless commitment to its espionage goals. The Security Service of Ukraine (SSU), the Ukrainian law enforcement authority and main intelligence and security agency in the areas of counter-intelligence activity and combating organized crime has identified Gamaredon personnel as officers from the Russian Federal Security Service (FSB), the Russian internal security and counterintelligence service responsible for counterintelligence, antiterrorism, and surveillance of the military, adding a geopolitical dimension to the group’s activities.
Unveiling the C2 Infrastructure:
In our extensive analysis, we delve into Gamaredon’s command-and-control infrastructure, highlighting its extreme flexibility and volatility. Despite these dynamic characteristics, the infrastructure maintains previously reported patterns and characteristics, indicating a certain level of consistency in Gamaredon’s approach.
Conclusion:
As cybersecurity experts continue to unravel the complexities of state-sponsored cyber espionage, Gamaredon remains a focal point of scrutiny. The LitterDrifter worm serves as a testament to the group’s adaptability and innovation, showcasing the constant evolution of cyber threats. Understanding and dissecting such malware is crucial in fortifying global cybersecurity defenses against increasingly sophisticated adversaries.
Check Point Customers Remain Protected
Check Point Customers remain protected against attacks detailed in this report while using Check Point Harmony Endpoint . When using Check Point to secure your business, you gain accurate prevention against the most advanced attacks through the power of ThreatCloud AI, the brain behind all of Check Point’s products. ThreatCloud AI.
For further information, read the detailed blog on Check Point Research blog.



