
Operation MiddleFloor: Unmasking the Disinformation Campaign Targeting Moldova’s National Elections
Executive Summary:
- Ahead of Moldova’s elections on October 20, 2024, Check Point Research detected an ongoing disinformation campaign aiming to influence the results of Moldova’s elections and nationwide referendum on EU (European Union) membership.
- Using emails as its primary attack medium rather than the traditional means of social media and news sites, threat actor Lying Pigeon impersonates official European Union institutions, Moldavian ministries, and political figures to disseminate misleading content and encourage interaction so as to obtain the victims’ personal information. The latest, likely to set the stage for more targeted malware attacks.
- The campaign exploits sensitive topics and concerns connected to the pro-European government and Moldova’s potential EU membership, such as LGBT (Lesbian, Gay, Bisexual, Transgender) rights, fuel prices, immigration, anti-corruption measures, and changes in the educational system.
- We uncovered links between the threat actor Lying Pigeon and previously unattributed clusters of malicious activity across Europe, determining that they are the same source. In addition to disinformation, these campaigns also distributed infostealers
As Moldova approaches a critical juncture in its democratic journey, Check Point Research discovered a disinformation campaign, targeting its government and education sectors. Check Point Research uncovered that starting in August 2024, malicious actors are seemingly working to influence public perception ahead of the country’s pivotal elections on October 20, 2024. With a nationwide referendum on EU membership coinciding with the presidential election, the stakes are higher than ever.
After the start of the Russian-Ukrainian war, Moldova, a former Soviet republic, was granted EU candidate status and has since faced increasing scrutiny and manipulation from external forces. Exploiting sensitive topics related to the pro-European government and Moldova’s potential EU membership, the disinformation campaign likely aims to undermine support for Moldova’s current leadership and foster skepticism about European values.
Operation MiddleFloor, a disinformation campaign carried out by the threat group Lying Pigeon, uses different techniques and narratives and is linked to clusters of nefarious activity across Europe. In this blog, we uncover the layers of this unfolding narrative, the threat actor’s intention, and its connection to other European disinformation campaigns.
Email: An uncommon medium for disinformation
Unlike typical disinformation campaigns that spread via impersonated news sites and social media posts, Operation MiddleFloor relies on email to distribute its messages and gather information. Unique to email, the operation directly targets individuals. The private nature of emails makes them harder to detect and counteract. Furthermore, emails appear more credible when mimicking legitimate and trustworthy sources, encouraging recipients to click links or provide personal details. Conversely, email campaigns have a limited reach as they rarely go viral, such as social media content, and emails are more easily traced to their sources.
Disinformation Tactics: Exploiting Public Concerns
Lying Pigeon cleverly exploited controversial topics within Moldova in connection to the country joining the European Union; all this by impersonating different EU entities.
Moldovan Public Sector: Promotion of LGBT rights and Mandatory English Proficiency
The disinformation campaign against Moldova kicked off in early August by distributing a fake PDF document aimed at civil servants and state officials. Allegedly from the European Commission, this counterfeit document outlined supposed compliance measures for EU membership, including:
- Mandatory English Proficiency: Claims that officials would need to pass an IELTS exam and hold a master’s degree in public administration.
- Promotion of LGBT Rights: A controversial recommendation to raise the LGBT flag at Ministry buildings on 12 significant days throughout the year.
Although the document is entirely fabricated and does not represent any actual EU requirements, the last page features a fake email address of a genuine EU Commission expert and a feedback form to encourage engagement with threat actors, both hosted on the same malicious domain.

Corruption in Judicial System
Another fraudulent document, disguised as communication from the European Public Prosecutor’s Office (EPPO), targets Moldovan officials in the judicial system. This document requests personal information and details about the commercial activities of close family members, falsely claiming to comply with EU anti-corruption regulations. It instructs recipients to submit this data through a form through Lying Pigeon’s controlled domain. The document is absent from the actual EPPO repository, deviates from standard EPPO templates, and contains glaring grammatical errors, such as “august” in lowercase, revealing it as an apparent forgery.

Migration Policy
In early September, several organizations in the Republic of Moldova, particularly in the education sector, received an email claiming to contain a “resolution” from the Ministry of Labor and Social Protection regarding “changes in migration policy.” The attached document falsely asserted that measures would be taken to attract migrants from the Middle East to address labor market losses due to emigration from Moldova. It included claims such as requiring at least 30% of migrants in each organization, plans for new mosques in every region, and a simplified citizenship process for employed migrants. Moldovan officials have confirmed that the document is a fake.
Increasing Gas Prices
In mid-September, threat actors exploited concerns over winter gas prices by email masquerading as the Ministry of Energy. The message falsely claimed that gas prices would rise and outlined planned interruptions to the natural gas supply, tapping into public anxiety during this critical time.
EU Educational Values
Lying Pigeon sent an email impersonating a member of the European Commission to over 80 recipients at a prestigious European university. Claiming to promote a pro-European message inspired by the current Moldovian President Maia Sandu, the email instead spread falsehoods about European education values, such as the incorrect notion that lowering student grades encourages academic growth. It also contained misleading information on job opportunities for low-performing students and inaccurate requirements for working within the EU, contradicting established EU education policies emphasizing equity and fairness.
Identifying the Source
The disinformation campaign surrounding European education values appears to have Russian-speaking origins, given the email’s awkward phrasing that suggests it was translated from Russian. Phrases like “has already addressed to you” and references to “toilets for the middle floor,” a direct translation of a Russian term for gender-neutral toilets, highlight this linguistic inconsistency. Additionally, the metadata of associated PDF documents indicates a Russian language setting, with timestamps corresponding to the UTC+3 time zone, which aligns with regions including parts of Moldova, Russia, Belarus, and other Eastern European countries. This suggests that the source of the campaign may be linked to Russian-speaking individuals or entities.
During Operation MiddleFloor, Lying Pigeon registered the domains spoofing European and Moldovan entities through domain name registrars, all of which had interconnected IP addresses, allowing us to link seemingly different techniques and messages to the same operation.
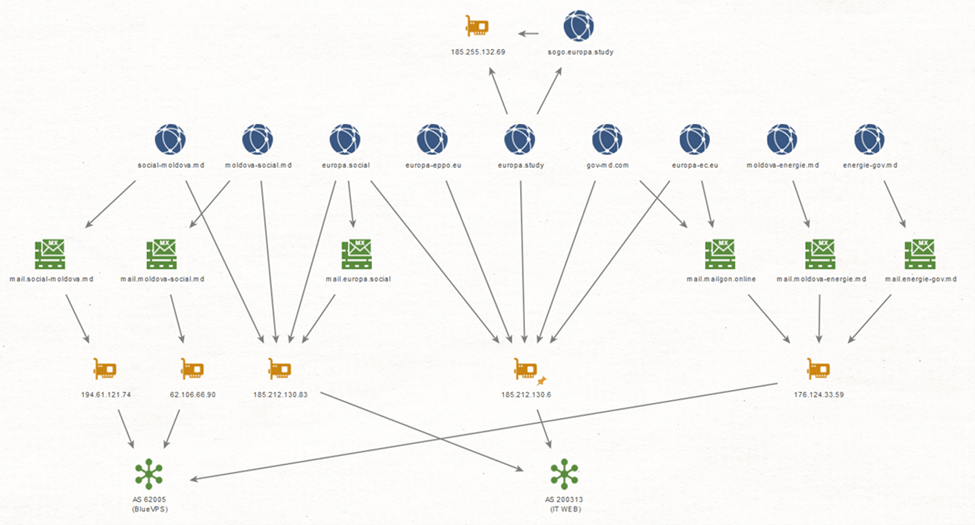
Connecting MiddleFloor Operations to Previous Disinformation Campaigns
Based on infrastructure analysis and correlation, we were able to link the threat actor MiddleFloor campaign to additional disinformation campaigns that targeted EU countries during the last two years.
These discoveries showed that Lying Pigeon was behind additional false narratives within the European Union. Around the time of significant events like the NATO summit and the Economic Forum, official entities were spoofed. In the case of Spain’s 2023 parliamentary elections, Spanish Russian-speaking communities were targeted with a Telegram message leading to a counterfeit website resembling the Community of Madrid’s official site. An “official warning” from the Ministry of Interior was posted, alerting citizens to a series of attacks planned by the ETA—a Basque separatist organization. The message encouraged recipients to abstain from voting, ostensibly to safeguard their lives. Also, official technological entities in Poland, like CERT PL and the National Research Institute, were spoofed, likely as part of similar targeted disinformation campaigns in Poland.
Influencing National Interests and Distributing Malware
The disinformation campaign led by Lying Pigeon represents a significant and ongoing threat to the political stability of the Republic of Moldova, particularly as the campaign seeks to influence the outcomes of both national elections and the EU membership referendum. Our investigation also connected Lying Pigeon to previous election interference activities in Spain in 2023, highlighting their persistent involvement in undermining European democratic processes. The group’s activity around major European events furthers their disinformation efforts.
Some parts of the campaign websites have similar code and look similar. They load an additional script that collects all content entered in the fields, the victim’s user agent, and the victims’ IP addresses. Though the data is limited, when combined with personal details, it could enable more focused attacks, such as drive-by attacks.
Beyond their influence operations, Lying Pigeon most likely uses campaigns to distribute infostealer malware and collect sensitive information for future targeted attacks. This dual approach of combining disinformation with information harvesting underscores the sophisticated and multifaceted nature of Lying Pigeon’s operations, making them a critical threat actor to monitor in the ongoing struggle to protect democratic integrity and ensure cyber security in Europe.
Remaining Protected in an Age of Disinformation
In the ongoing battle against disinformation, organizations must adopt a multifaceted and holistic approach. Rather than seeking a one-size-fits-all solution, organizations should meticulously assess their existing systems and controls for vulnerabilities related to disinformation attacks. These efforts should extend beyond reactive measures; proactive strategies, threat intelligence, and robust incident response protocols are essential to detect and counter disinformation campaigns effectively.
To learn more about the Operation MiddleFloor read Check Point Research’s full report.








