
Cloud Security in Action: Meet the New Check Point CloudGuard
Digital transformation and the widespread adoption of cloud technologies are creating mega-shifts across all industries. The adoption of cloud is far from straightforward and linear, as companies navigate their cloud adoption journey in phases. Moreover, the range of technologies employed within cloud applications is extensive and the dynamics of security teams within organizations is changing.
The interdependency of these changes creates major challenges when organizations are trying to establish a cloud security operation. Organizations that have tried to implement individual security solutions to safeguard different cloud components are struggling to demonstrate significant business and security benefits.
Implementation of cloud security operations calls for a shift away from fragmented cloud security capabilities and a focus on a unified security platform that grants teams the power and flexibility to proactively take-action.
Today, we are unveiling our latest CloudGuard solution and showcasing how leading companies are leveraging it to drive essential cloud security operations.
Check Point CloudGuard in Action
Throughout the years, Check Point has invested substantial resources in building the most comprehensive cloud security platform. Incorporating elements such as CSPM, CIEM, DSPM, CWPP, CDR, WAAP, Code Security, IaC Security, and Open-Source Security into a unified platform where the collective whole outperforms the individual components.
The latest version of Check Point CloudGuard revolutionized cloud security, prioritizing outcomes over features, signifying a shift from fixed to active, preventive security.
Leveraging our unique cloud security approach, organizations can drive crucial security operations across clouds, applications, and teams using Check Point CloudGuard. Our customers are adopting best security practices such as Risk Management, Zero Trust, Workload Security, and Data Security Posture Management, leading to notable business outcomes, an exceptional developer experience, and high-grade cloud application security.
Risk Management in Action
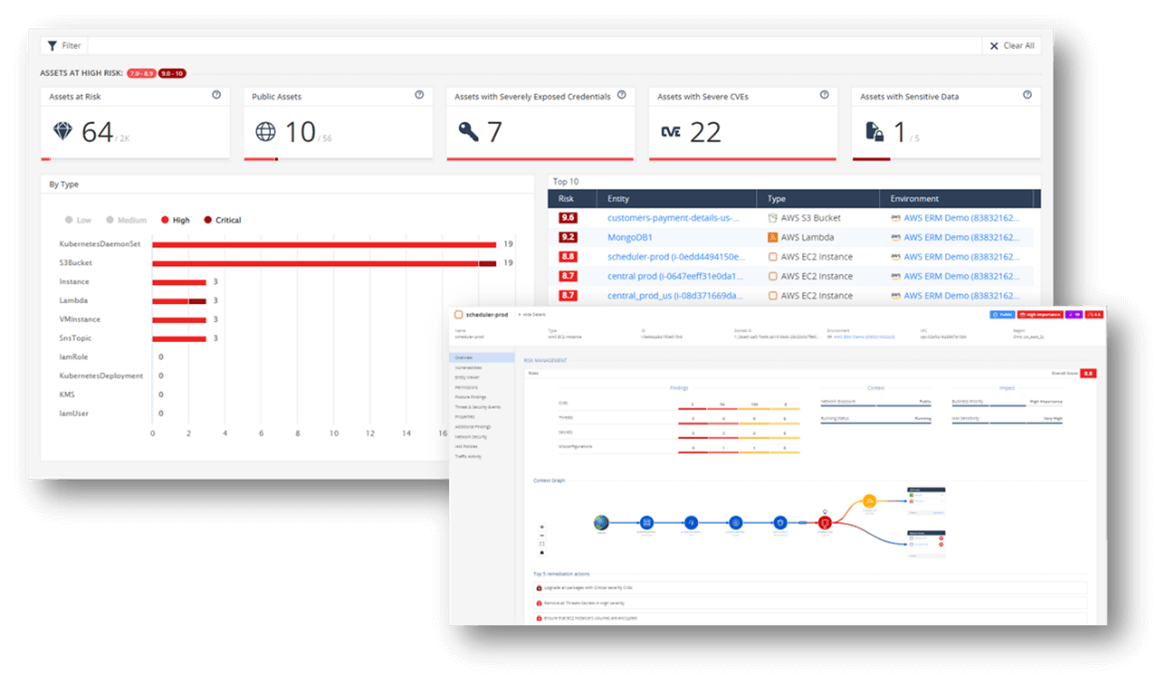
Applying Context-Based Risk Assessments to Patching Strategies
A new CVE or vulnerability is identified almost every day. Security teams need to plan their patching strategies to ensure that the applications they are managing remain secure while allowing developers to continue with their day-to-day activities of introducing new innovative capabilities. Check Point CloudGuard transforms the workflow of the security team by transitioning a frustrating, time-consuming situation into an easily managed and well-triaged list of high-priority assets based on the context of the specific cloud environment. Then, the patching efforts can be executed gradually, offering both a higher business value and strengthening cloud security.
Zero Trust in Action
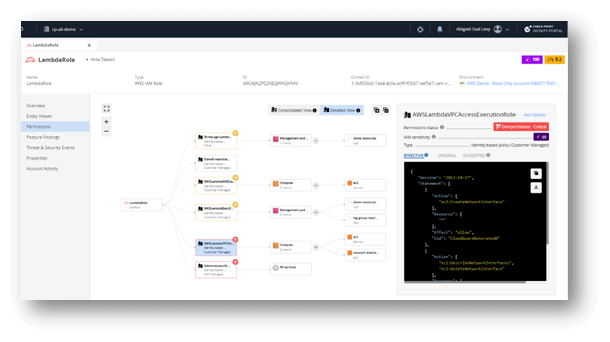
Shifting from Perimeter Protection to Identity Management with CIEM and Secret Scanning
Security teams have adopted Check Point CloudGuard as a central component of their Zero Trust security strategy. In the absence of traditional perimeters, organizations have worked to streamline access control while handling overprivileged accounts. Within this framework, Cloud Identity and Entitlement Management (CIEM) automatically detects over-privileged entities and provides least-privileged recommendations, issuing alerts for anomalies in user permission usage and deviations from best practices. However, these efforts will not save you if a developer accidentally embeds keys or secrets within their code. To complete their zero-trust framework, organizations are embracing CloudGuard’s secret scanning. This integrates seamlessly to the development lifecycle and executes in just a matter of seconds. By adopting CloudGuard in their Zero Trust strategy, organizations can offer both exceptional developer experience and highly secured cloud applications.
Workload Security in Action
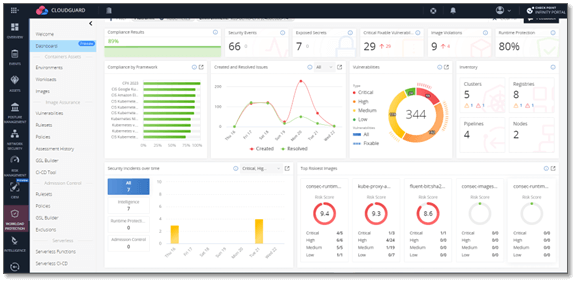
Continuously Securing VMs, Containers, & Serverless Functions Across the Development Lifecycle
Workloads play a pivotal role within a cloud application as they are responsible for executing the application’s processes. They change frequently to accommodate scale, business demands, compliance requirements and software updates. Since cloud workloads are highly dynamic, securing them requires a comprehensive continuous security approach:
- Image assurance – continuously ensuring workload integrity pre- and post-build across software development lifecycle (SDLC)
- Kubernetes (K8) admission controller – continuously providing visibility and control across container clusters. Both verifying the integrity of containers and ensuring zero-trust running workloads.
- Posture & Compliance – continuously managing VMs, Containers, and Serverless functions, as well as agentless VM scanning.
- Runtime Protection – continuously securing the workloads in runtime through 3-layers of protection: Workload Protection, Web and API protection, and Cloud Network Security
Having these workload capabilities unified under a single platform grants cross-functional teams the power and flexibility to proactively secure all cloud workloads.
Data Posture in Action
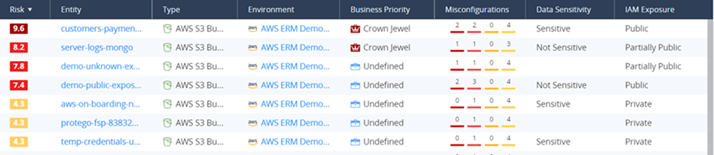
Addressing Sensitive Data Vulnerabilities Based on Their Context Within the Application
A primary concern in cloud security involves threats directed on cloud data, specifically those aimed at stealing or exploiting sensitive information. However, sensitive data storage is an essential component of cloud applications and, by itself, is not a security risk. Some sensitive data storages are resilient to breaches while other data storages are exposed to significant risks. Check Point CloudGuard helps organizations identify the storages that are vulnerable to attacks and prioritize them over others that are more secure. CloudGuard leverages leading data sensitivity technologies such as Amazon Macie and Azure Purview and analyzes their sensitivity findings in the context of the application. This enables security teams to triage their most crucial data risks and improve the overall security of their cloud environment.
Leading Cloud Security Provider Recognized by Top Analyst Firms
With three decades of security experience and extensive knowledge of the fundamental hurdles that arise in cloud environments, Check Point offers an unparalleled level of cloud security expertise. Check Point CloudGuard provides a comprehensive approach, enabling cloud security in action. Our platform was recognized in 2023 by top analysts’ firms as a leader in various categories such as: CSPM, CNAPP, CWPP, WAAP, Cloud Network Security, and more.
Getting Ready for Action
Learn more about our unique cloud security in action approach and how you can build a winning cloud strategy together with Check Point CloudGuard by contacting your Check Point account team or scheduling a demo.









