
Docker Images: Why are Many Cyber Attacks Originating Here?
What happens when you need to set up a container environment quickly? You may use a popular platform called Docker Hub to find an application that can be rapidly deployed. Then, let’s say you find an image that looks perfect and download it. Everything seems to be going smoothly, but a few days later, you notice something strange. Your CPU usage is through the roof, so you investigate and realize that you’ve been a victim of a cyber attack: the Docker image you downloaded was infected with malware.
While that sounds like the punchline to a terrible joke, this scenario is not as far-fetched as it may seem. A new report revealed that over 1,600 publicly available images on Docker Hub hid malicious behavior, including DNS hijackers, cryptocurrency miners, and embedded secrets used as backdoors.
Unfortunately, due to the size of the Docker Hub public library, its administrators cannot review every upload on a daily basis, which means that many malicious images go unreported.
With this in mind, it’s crucial to be vigilant when downloading images from Docker Hub—not everything is what it seems.
The Lowdown on Docker Images: What They Are and How They’re Used
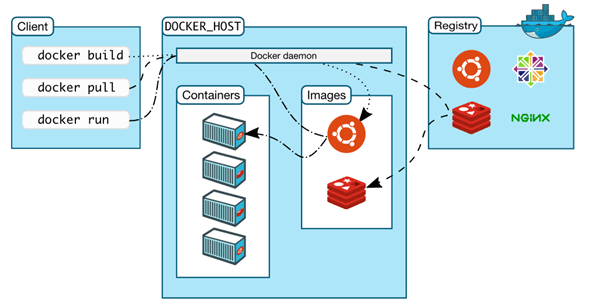
Docker – how it works
Docker images are the building blocks of containerization. They are a snapshot of an application and its dependencies bundled together in a single package. Think of them like a blueprint for a house—just as a blueprint lays out all the architectural details and specifications, a Docker image provides the same information for running an application.
These images can be stored in a registry, such as Docker Hub, and can be pulled down and run on any system with the Docker engine installed. This process makes it easy to distribute and run applications in a consistent and portable way, regardless of the underlying infrastructure.
You can create Docker images using a Dockerfile, which contains instructions on how to build the image. For example, the Dockerfile might specify the use of a certain operating system or software for the image at hand. Once you’ve built the image, you can run it as a container, which is an isolated environment that allows the application to run as if it were on its own system.
Docker Danger: Why Hackers Love Targeting Docker Images
Docker images have become a favorite target for hackers due to their inherent vulnerabilities. They are often built on top of other images and include various libraries and dependencies. If these underlying components contain known vulnerabilities, attackers can easily exploit them to access the containerized application and sensitive data.
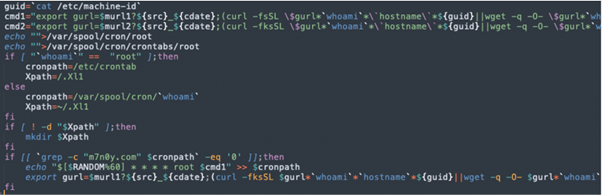
Adding a malicious cronjob
Another reason is that Docker images are common in cloud environments, which are highly dynamic and can scale quickly, making them an attractive target for attackers looking to gain access to a large number of systems. Additionally, containers can make it difficult for traditional security solutions to detect and respond to attacks, as hackers can easily move between hosts and networks.
Even the ways Docker images are stored and distributed aren’t safe from threats. 61% of all images pulled from Docker Hub in 2022 come from public repositories, up 15% from 2021 statistics. As they are typically stored in public or semi-public registries where anyone can download and use them, it’s easy for attackers to find and exploit known vulnerabilities in images and distribute malicious ones that look legitimate.
Docker’s Biggest Weaknesses: A Closer Look
1. Misconfigured Docker Daemon API
The Docker daemon API controls and manages Docker containers. Misconfigurations in this API allow unauthorized access to the host system, potentially leading to a complete compromise. It’s often caused by leaving the API exposed to the internet or not properly securing the API with authentication or access controls.
2. Exposed Container Ports
By default, Docker containers expose several ports to the host system. Suppose these ports are not properly configured or are left open to the internet. In that case, it can allow an attacker to connect to the container and gain access to the application or data.
3. Unpatched Software
Docker images are often built on top of other images, and these underlying images may contain known unpatched vulnerabilities.
4. Insecure Volumes
Using Docker, you can store large volumes of data outside of the container. If these volumes are not properly secured, an attacker can modify the data stored in the volume.
5. Privilege Escalation
Docker containers run with a restricted set of permissions. However, if a vulnerability exists in the application running inside the container, an attacker can gain additional permissions and take complete control of the container.
How to Detect, Remediate, and Fix Docker Image Vulnerabilities
As more and more companies adopt containerization technology, it’s crucial to ensure that the images used to build these containers are secure. One effective method for detecting vulnerabilities is to use image scanning tools that analyze an image’s contents and compare them to a database of known vulnerabilities. Scanning tools can help identify potential weaknesses that may be present in an image, such as outdated libraries or known vulnerabilities in the underlying operating system.
Another step in securing Docker images is to keep them up to date, including updating the underlying operating system and any libraries or dependencies used within the image.
You can also remediate vulnerabilities in Docker images using configuration management tools that automatically update images and ensure secure configuration. Additionally, it can be helpful to use a tool that allows for continuous monitoring of images to identify and fix vulnerabilities in a timely manner.
Finally, it’s important to pay attention to the supply chain of the images you use. This involves monitoring the source of the images and any third-party components included within it.
Securing Docker images requires a multi-faceted approach that includes regular image scanning, keeping images up to date, and continuously monitoring the image supply chain. Taking these steps makes it possible to reduce the risk of exploitation by attackers significantly.
Securing Your Docker Images: The Final Frontier
Docker images have become a popular target for hackers due to the inherent vulnerabilities in their construction and usage. These vulnerabilities stem from the use of underlying components that contain known vulnerabilities, the dynamic nature of cloud environments, and the ease of distribution.
To protect against these threats, you must have a comprehensive approach to detecting, remediating, and fixing Docker image vulnerabilities. Organizations should consider implementing a robust security strategy to keep their Docker images and containerized environments safe to stay ahead of the curve.
Protect Your Docker Images with CloudGuard Spectral
CloudGuard Spectral is available as a standalone solution or as a component of CloudGuard CNAPP.
Spectral’s secret scanning tool safeguards IAM frameworks by identifying and remediating vulnerabilities, giving you peace of mind that your code, assets, and infrastructure are protected from malicious actors.
CloudGuard CNAPP provides a fully integrated developer solution that streamlines cloud security operations from code to cloud. With CNAPP, you have a unified platform that not only identifies security issues throughout your pipeline but also provides in-depth insights and context. This allows you to understand effective IAM permissions and privileges and prioritize risks across your entire cloud infrastructure.



