
Securing the Road Ahead: Addressing Persistent Cloud Misconfigurations in the Automotive Industry
Explore a pair of security exposures from the automotive industry and how the proper security tools could have prevented these ‘same old issues’ from happening.
Earlier this month, BMW was yet another victim of dangerous misconfigurations in their cloud storage, which exposed private keys and sensitive data. According to a recent article by TechCrunch, a public Azure storage bucket held “script files that included access information, secret keys for accessing private bucket addresses, and details about other cloud services.”
To be fair, BMW is not alone in these issues, in fact, according to the 2023 Check Point Cloud Security Report, misconfigurations are the #1 security issue facing organizations using cloud storage today. And why is that? Human error. With the amount of new code, applications, and instances being pushed to the cloud every second of every day, it is increasingly difficult for proper security checks to be put in place prior to production.
Now, this does not mean that the cloud should be abandoned, in fact, the speed of the cloud is critical for organizations to keep up in today’s business landscape. However, security measures must be put in place to monitor, alert, and prevent threats to protect cloud environments and allow businesses, like BMW to move forward.
The good news is that this is no longer a pipe dream. The solutions needed to address these concerns exist. And what’s better is that you don’t have to engage 7 different vendors to cover all your concerns.
CNAPP has entered the chat.
Back in 2021, Gartner coined the term Cloud Native Application Protection Platform, or CNAPP. This technology was created for an extremely specific purpose. Due to the nature of the cloud, everything is an attack vector. So how do you secure every angle of attack and give yourself visibility into your inevitably human mistakes? CNAPP. These types of solutions are different because they are platforms (it’s right in the name), meaning you do not need to have point solutions sprawled across your environment. It also means that instead of having several different tools, all throwing you disparate alerts, and not communicating with each other, you can have all the security tooling you need integrated into a single interface with the various risk alerts being weighed contextually. What does this look like in practical terms? Let me show you.
Mis (re)configuration
The headline issue for the BMW exposure is that a storage bucket containing sensitive data was found to be publicly accessible. From there, the potential for exploitation grows rapidly. What sort of data was exposed? Well, “container access information” and “secret keys”. These types of issues are immediately brought to your attention with a CNAPP.
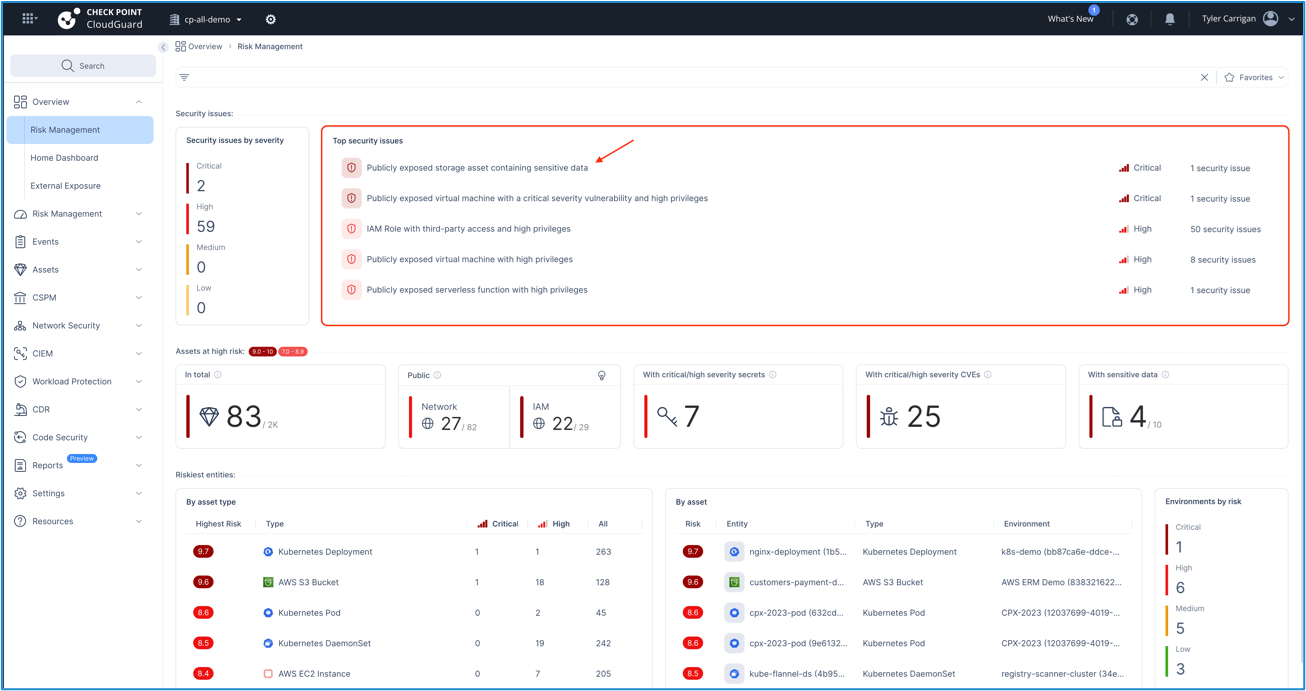
In the screenshot above is a look at the risk-management dashboard in our CloudGuard CNAPP. You can see in the highlighted area that this exact type of exposure has been designated as a critical severity and pushed to the top of the security issues tab. Meaning that your teams will see this alert and begin to take steps to investigate and remediate the issue. Speaking of remediation, a good CNAPP will also guide you in how to begin the process. Here is a drill down of the “publicly exposed storage asset” alert…
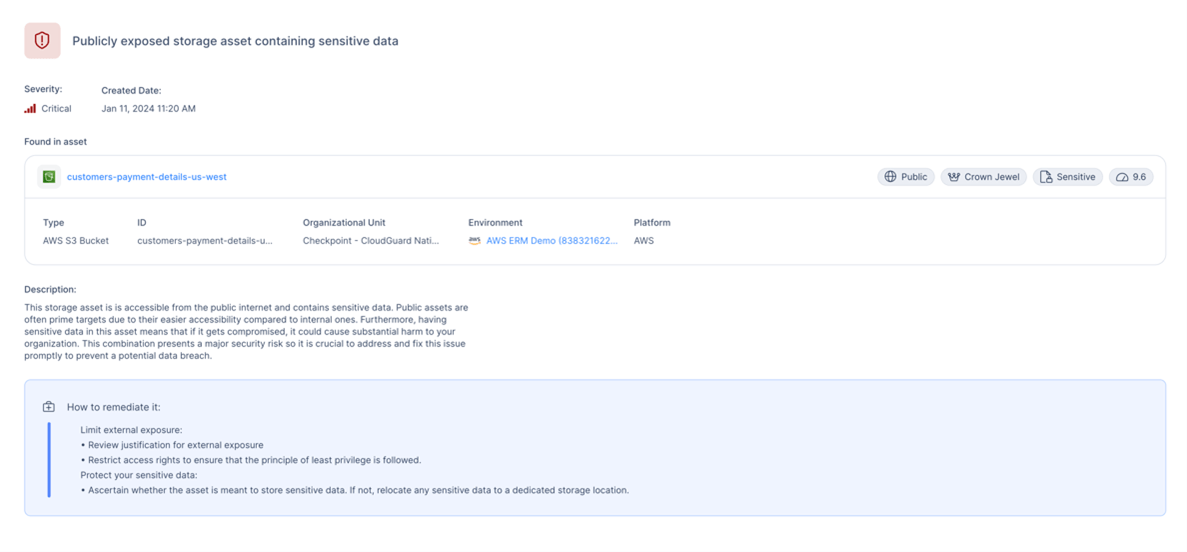
This type of alert doesn’t happen in a vacuum. Behind the scenes, the CNAPP looks at the asset and the circumstances surrounding the misconfiguration and begins to assign a risk score based on factors such as public exposure, data sensitivity, known vulnerabilities, business priority, and more.
Need another example of the value here? Let’s look at the Mercedes-Benz exposure from earlier this year. The TLDR on this one is that an employee authentication token was hardcoded into a public GitHub repository. This token provided “unrestricted access to the company’s source code”. I won’t insult you by explaining why this is a nightmare scenario. Instead, let’s look at how a CNAPP with code-security can help prevent these issues from happening to you.
A good code-security tool will allow you to integrate all your development environments – whether it be CI/CD, IDE, etc. – into the system so you have full visibility into all parts of the SDLC. It will also be fast enough to scan your environments without causing slowdowns for the system itself or the developers who depend on them. Finally, it will alert you when issues are detected and provide you with guided steps on how to remediate.
Back to the example above, it also works with GitHub…
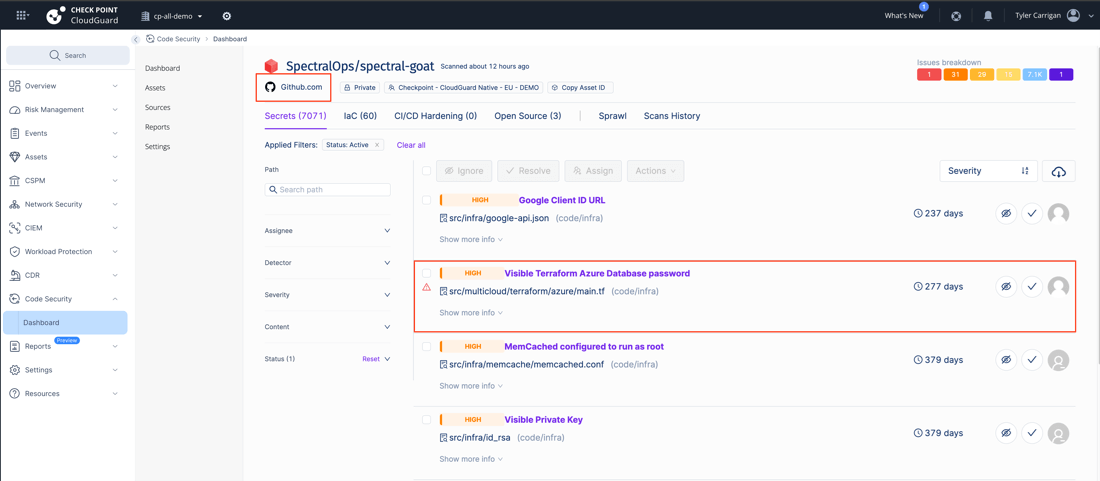
Here you can see a scan of a demo repository (using the CloudGuard code-security module), and the types of alerts you can expect when issues are found.
NOTE: this is all within the same interface as the Risk Management dashboard highlighted earlier in the article.
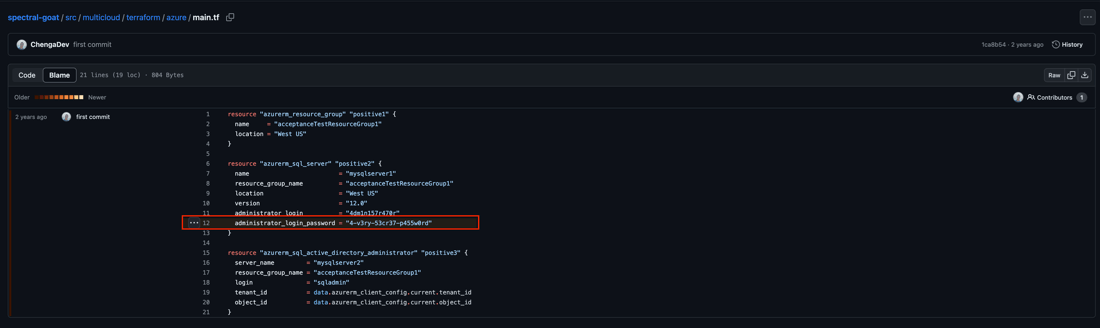
In this example, you can see an Azure Database password has been found in the codebase and needs to be remediated. If we drill down into the issue further, we get a playbook for how to handle these types of issues, as well as a highlighted look at the exact line where the issue was detected. Allowing for quick, easy remediation of an otherwise severe problem.
Know better, do better
At the end of the day, we are all human. We all make mistakes. But the truth is, in 2024, these types of issues can be avoided rather easily with the right security platform. If your company does business in the cloud and uses or stores customer data, you owe it to yourself and your clients to implement a CNAPP solution. Point solutions used to be good enough, but with the interconnectivity of the cloud, all it takes is a malicious actor finding one of the issues highlighted above to string together a publicly exposed database with a hardcoded API secret or account credential before you end up being the next big breach story. Don’t wait until then.









