Top Considerations for Securing AWS Lambda, part 3
Serverless computing or function-based computing, is a way by which customers can develop backend systems or event-driven pipelines without worrying about the underlying infrastructure, which is managed by the cloud provider. It is billed based on the invocations and the duration of execution. While powerful, serverless computing has special security considerations that organizations must address. This is the first of three blogposts to discuss how best to secure your serverless computing environment in AWS Lambda.
Blogpost 1: What is AWS Lambda?
Blogpost 2: What are the top security topics for AWS Lambda?
Blogpost 3: How can CloudGuard help enhance security for AWS Lambda?
Introduction to Check Point CloudGuard
Given all the above considerations, implementing and developing AWS Lambda functions securely can seem cumbersome and even overwhelming. To implement better security protocols, developers can leverage CloudGuard for full-security lifecycle support for AWS Lambda functions.
CloudGuard is a cloud security platform from Check Point, one of the leading companies in the field of cyber security and threat intelligence. CloudGuard provides the following benefits:
- Unified workload protection: CloudGuard ensures that all applications in the cloud are fully secured and empowers DevOps teams with a shift-left tool to efficiently secure code.
- Multi-cloud support: You can integrate CloudGuard with most cloud solution providers for a multi-cloud approach. It is versatile based on your cloud plan and goals.
- Unified Visibility: CloudGuard comes with a modern UI that allows customers to track and react to third parties and threats to their serverless function stack. The UI enables teams to monitor the security of their cloud applications at a single location without having to dig around multiple places.
How CloudGuard Helps Secure AWS Lambda
CloudGuard provides multiple features that help customers secure their serverless applications in production.
Serverless Risk Assessment
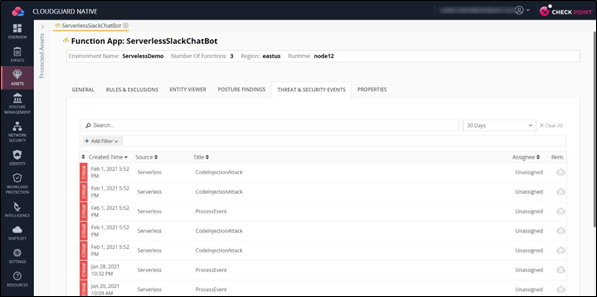
CloudGuard Proact Serverless protection allows customers to run risk assessments on their AWS Lambda functions. CloudGuard thoroughly scans and analyzes the AWS Lambda functions and their dependent libraries across all onboarded accounts for vulnerabilities, unnecessary IAM permissions, and sensitive data like secrets and hardcoded credentials.
Check Point CloudGuard Serverless Risk Assessment (Source)
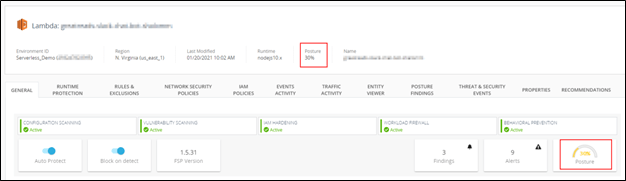
Based on the number, nature, and severity of the threats, CloudGuard calculates a posture score that allows customers to get alerts and, in most cases, recommends actions needed to mitigate those. The posture score provides an overview of the severity of threats on the console based on the score and classifies them as high, medium or low.
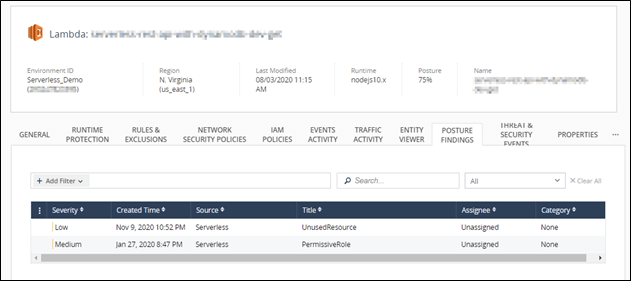
Posture Score
Runtime Protection
CloudGuard also provides runtime protection for AWS Lambda functions. This feature checks for input values provided to the AWS Lambda function during the execution and identifies potential malicious behavior and anomalies. Based on the configuration, it can also block or deny access to the AWS Lambda function during the execution. The runtime protection acts as a workload firewall for AWS Lambda functions and consumes minimal resources to operate.
A profile for each AWS Lambda function can be generated that would allow or reject certain types of activities during the execution of the function. For example, an allowlist may be created that will allow the AWS Lambda function to access files and local storage, APIs and network during the execution. But when there are actions not described in the allowlist, the runtime protection will trigger and block those actions.
The runtime module can also be integrated with the CI/CD pipeline that checks the security policy to determine the AWS Lambda functions that have been configured to use the runtime protection module. To learn more about enabling runtime protection for AWS Lambda functions, please follow the guide here.
IAM Least Privilege Protection
CloudGuard is able to scan through the AWS Lambda functions and detect loopholes within IAM policies and provide proactive alerts in case there are policies that do not adhere to the rules defined.
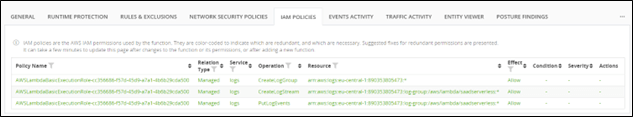
Viewing AWS IAM Permissions
To learn more about considering CloudGuard for serverless security, please refer to the Check Point product page.
With respect to the common AWS Lambda unauthorized event examples discussed above, CloudGuard helps in taking a proactive step to protect the AWS Lambda functions.
- OS Command Injection can be detected by the Runtime Protection tool.
- Compromised credentials can be detected by the Risk Assessment tool. If implemented within the CI/CD pipeline, it can also be configured to block deployment to AWS and prevent credentials from being leaked.
- Risk assessment can also identify IAM full access policies and necessary actions can be undertaken to allow minimum privileges.
Conclusion
Serverless functions let customers build stateless and event-driven functions in the cloud. With its ease of use and development, security of those functions can often be unwieldy to manage. In a shared responsibility model, enforcing security in the cloud is the responsibility of the customer—and that’s why tools like CloudGuard are indispensable.
CloudGuard is always “on”, 24 hours a day, seven days a week, proactively watching and protecting your cloud assets—AWS Lambda and otherwise. With only manual processes in place, it’s difficult to keep up with security needs, but with CloudGuard’s automation and functionality enhancing AWS Lambda security, security architects, admins and their leaders can rest easy.